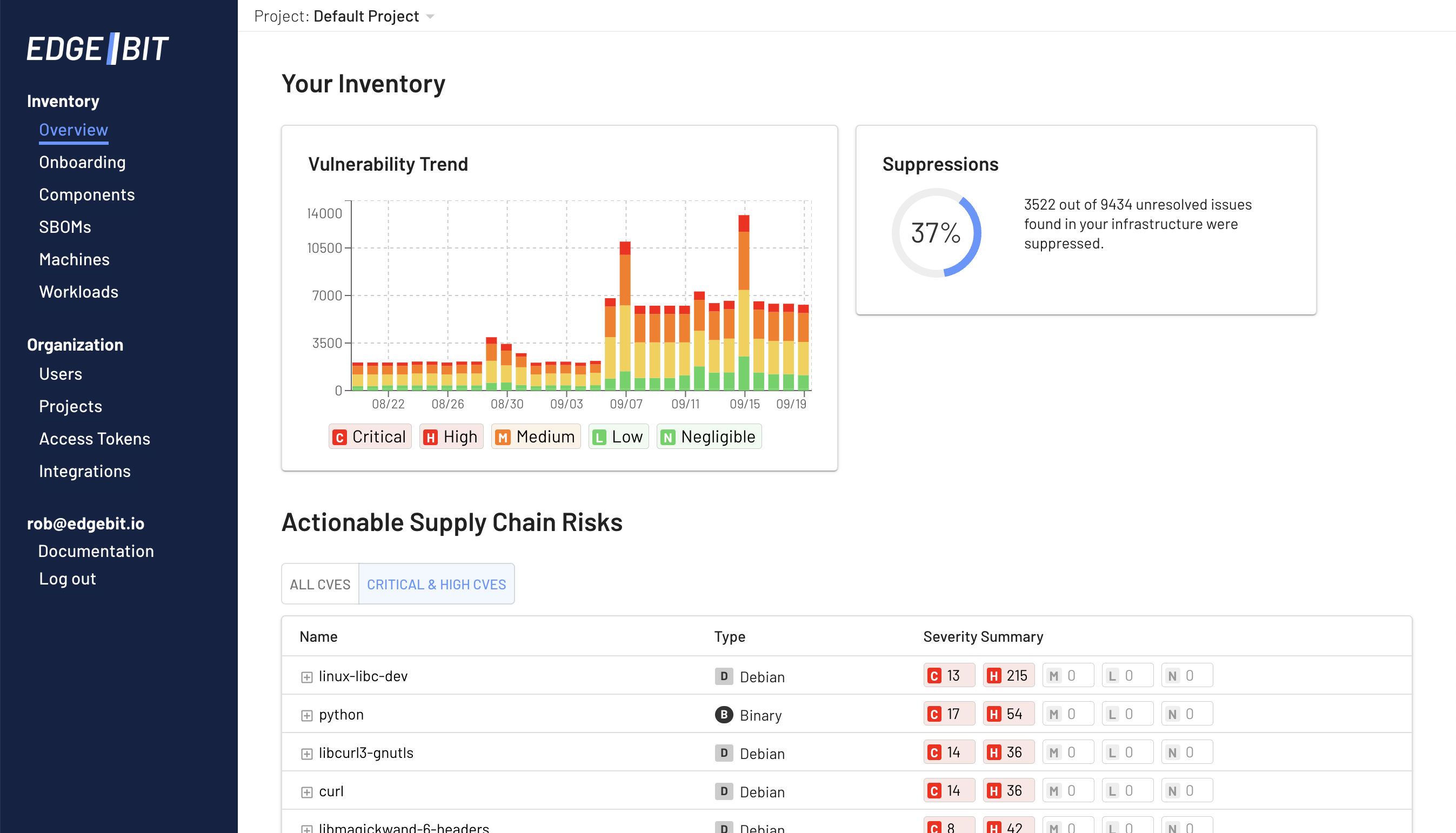
Prioritizing CVEs & Vulnerabilities
Each origanization has their own policies for prioritizing vulnerabilities, but here’s how EdgeBit recommends it:
- High severity score (CVSS)
- High Exploit Predicability score (EPSS)
- Workloads known to contain the vulnerability are deployed
- Packages known to contain the vulnerability are active within that Workload
- High prevalence in your fleet
You can find a live list of these vulnerabilites in the Overview page of the Edgebit Console.
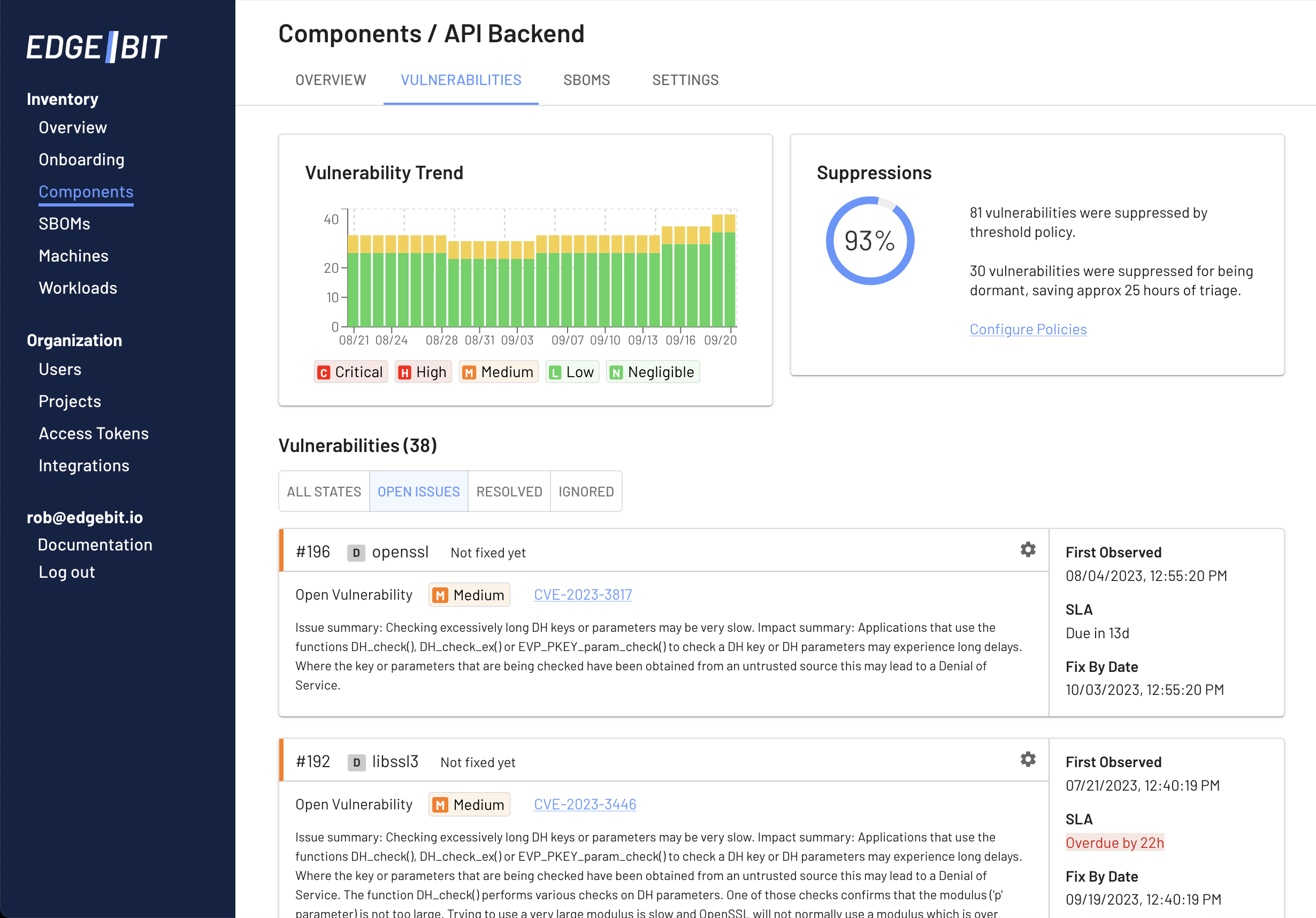
Triage Components
Engineers regularly see security context inside of their pull requests on components but a security team doesn’t have the same day-to-day interaction.
Security staff can look at the full list of vulnerabilities for the actively deployed versions of each component and verify that SLAs are being followed or identify where the SLA has been breached.
Integrate into Sprint Planning
Configure EdgeBit’s Jira integration to automatically create, update and close Jira Issues for discovered security issues. CVSS score is recorded as the Issue Priority and your configured SLA is translated into the Issue Due Date for easy sorting and prioritization during sprint planning.
Best of all, Jira Issues are automatically marked as done when EdgeBit detects the issue has been fixed and deployed.
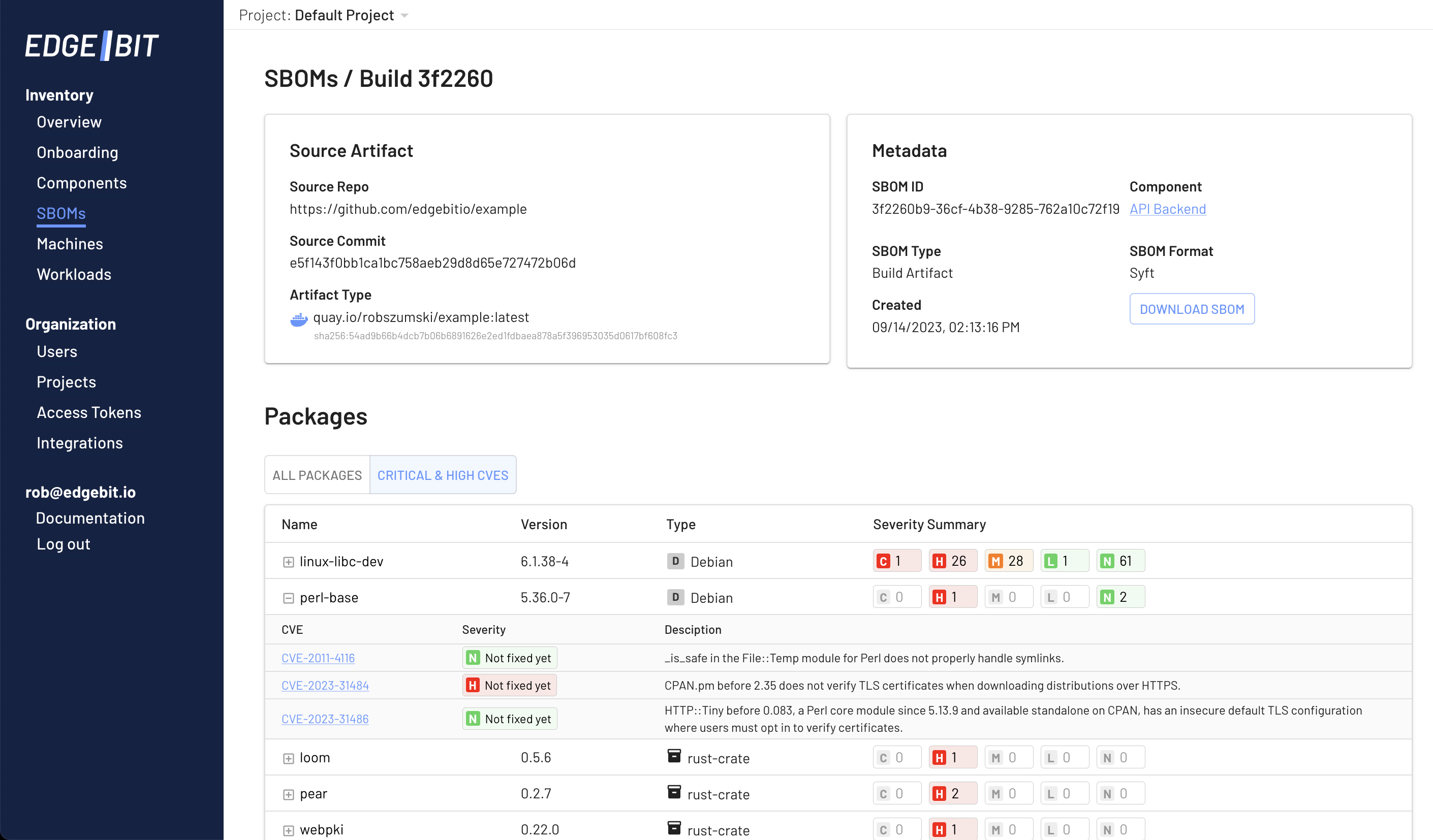
Software Bill of Materials (SBOM) Overview
When investigating a specific app version, digging into the SBOM is a great place to start. You’ll see info about the type of package detected, the severity of the vulnerability and whether it’s been fixed, or won’t ever be fixed.