EdgeBit now supports syncing workload information from Amazon ECS to power automatic remediation, inventory tracking, and vulnerability SLA calculations. This joins our existing workload syncing from EKS, CNCF-certified Kubernetes clusters, and standalone Linux machines.
Runtime context is a powerful asset for security teams
The key to understanding your risk right now is EdgeBit’s runtime knowledge of the container builds actively running in production.
Runtime context is also central to a highly automated security program. Merging code is what many security platforms consider fixed, but EdgeBit closes out security issues when they are fully deployed to production — the actual “fix” event.
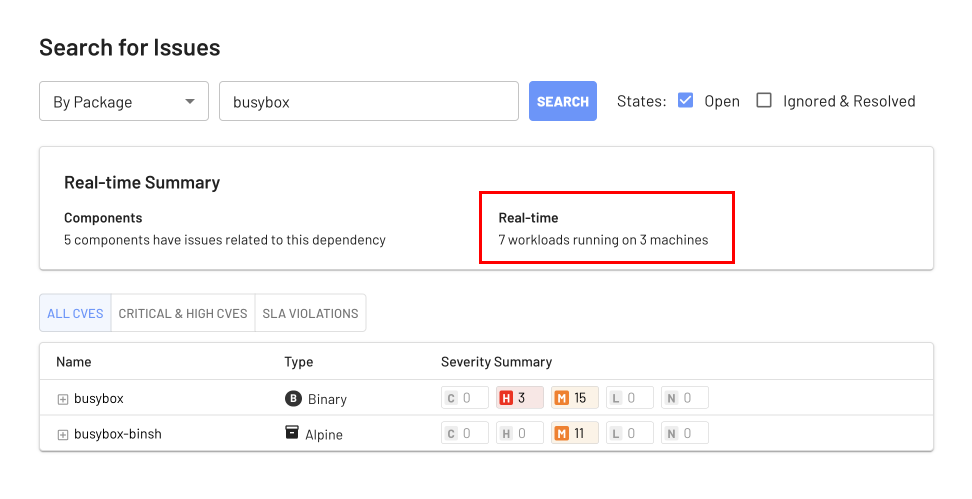
Using runtime context as the trigger ensures your SLA calculations are accurate and frees up your project managers or security engineers from manually tracking and closing out Jira tickets. EdgeBit does it all automatically for you.
EdgeBit’s user interface makes it very clear when a component of your stack is lagging behind on its security updates, making it easier to identify areas of focus.
Supporting Fargate and EC2-backed clusters
Workload syncing from Amazon supports both ECS Fargate clusters and ECS backed by EC2 machines. Cluster name, region, zone and other metadata are automatically collected which blends your ECS workloads seamlessly with existing workloads in EdgeBit.
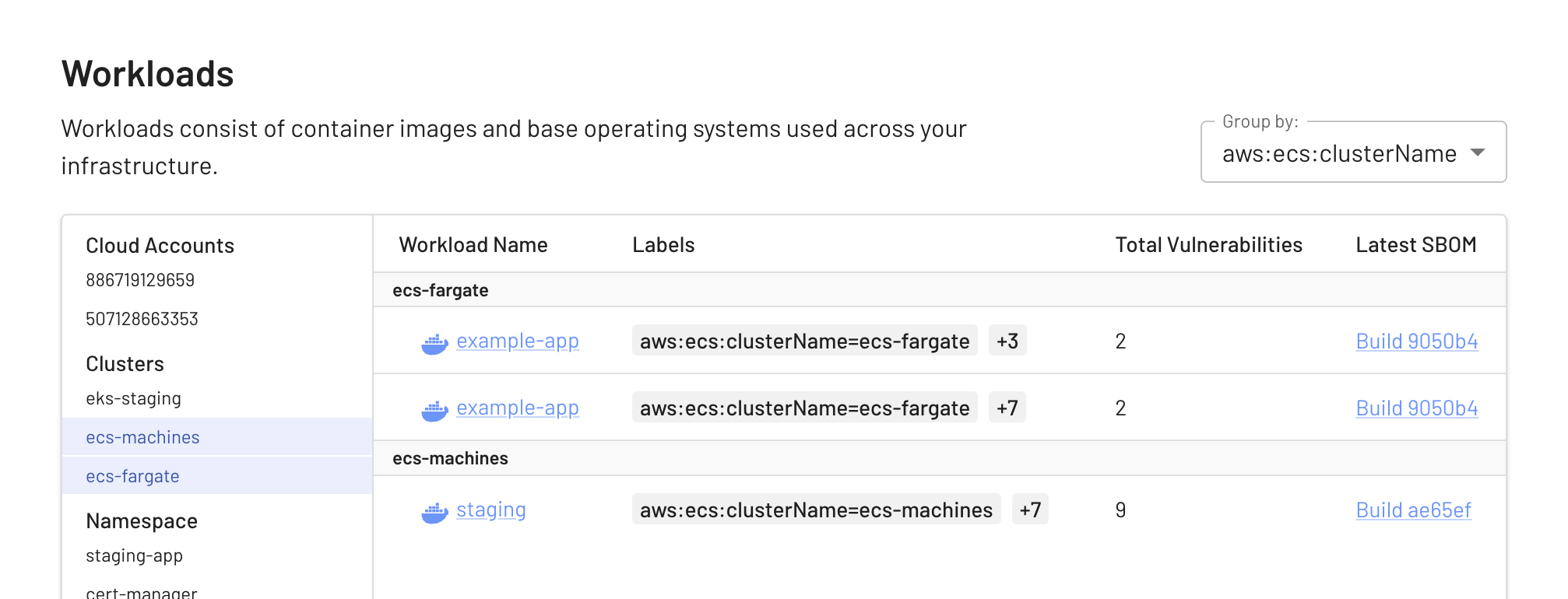
When you connect your account, you can specify which regions should be searched for clusters and workloads.
Connecting to your AWS account
ECS workload information is fetched through an IAM “assumed role” which grants EdgeBit access to read from your clusters. This approach avoids the use of static credentials and provides a full audit trail.
Multiple AWS accounts can be configured, if you had a production and staging account for example. Simply run the configuration process for as many accounts as you’d like.
Try it out and let us know what you think!
