- Platform
-
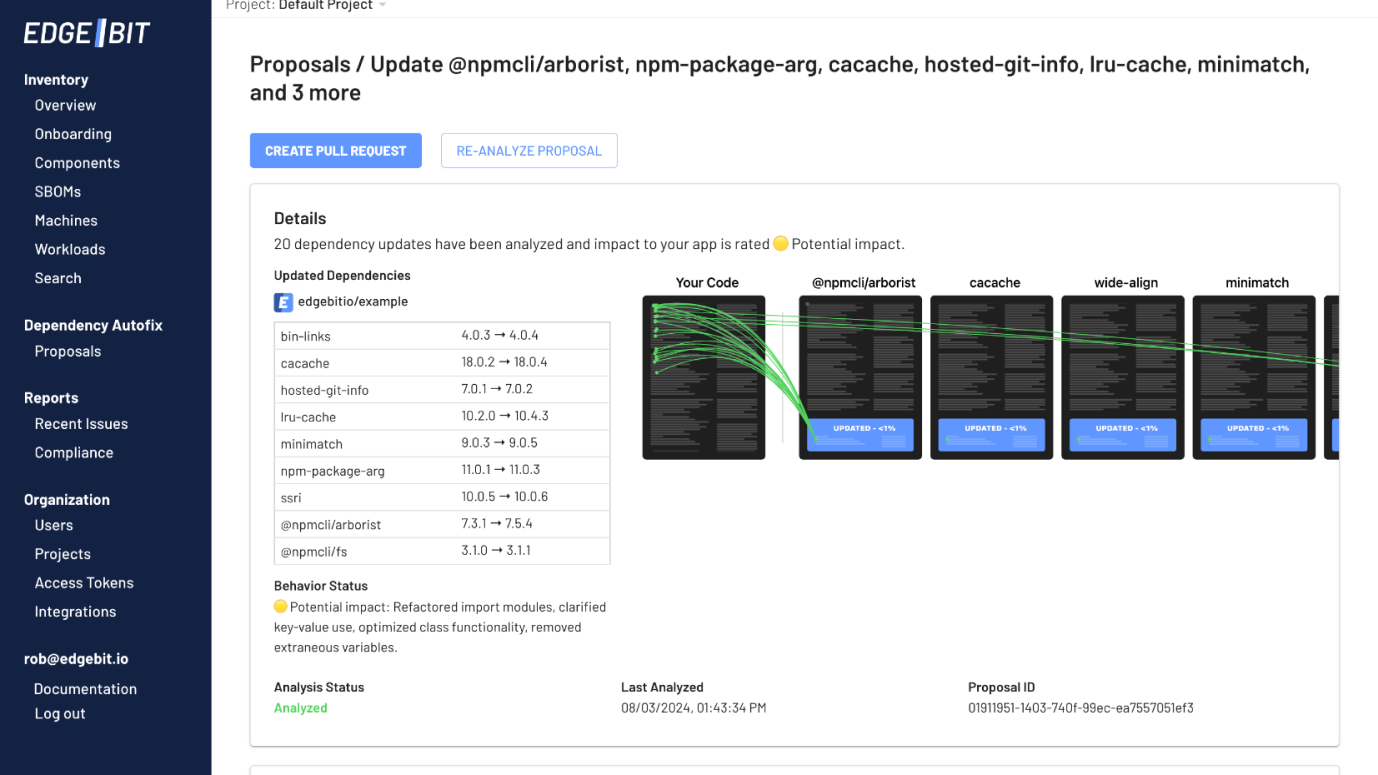
Dependency AutofixKeep dependencies up to date with static analysis, reachability and AI
-
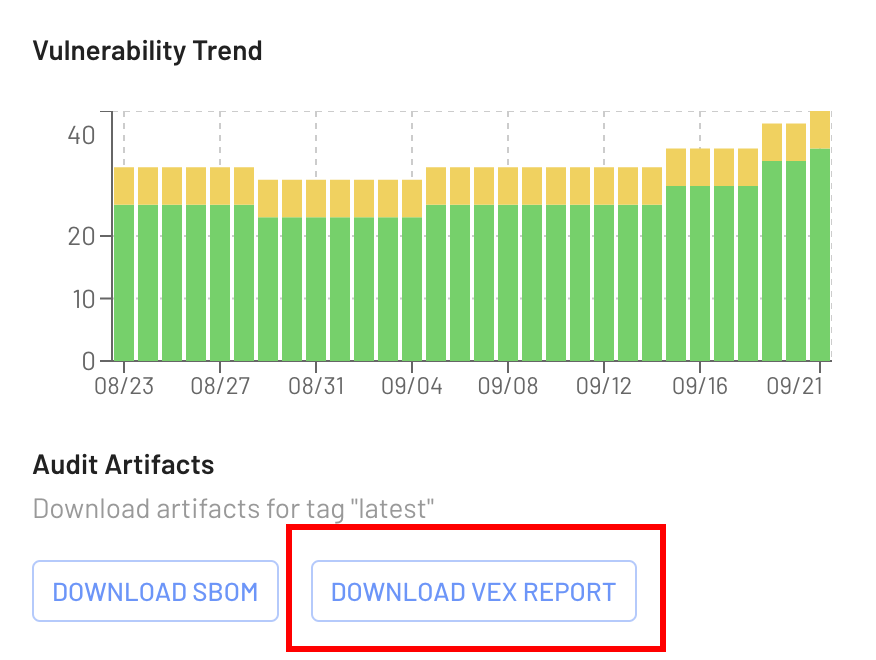
Scanning, SCA & VulnerabilitiesContinuously catalog open source usage, vulns, & map to production
Found, Fixed, and Merged with one complete platform.
- EdgeBit for GitHub pipelines
- EdgeBit for Kubernetes
- EdgeBit for ECS & Containers
- Sync to Jira, Vanta and other tools
Product Features: -
- Solutions
- Docs
- Open Source
- Pricing
- Company