EdgeBit gives developers context about new and modified software dependencies when submitted a pull request or pushing a new commit before it merges into main.
This context is useful for:
- vulnerabilities: understand vulnerabilities present in the selected version(s)
- recommendations: see a recommended version with fixed vulnerabilities, if available
- standardization: gain context about versions of the same dependency that other teams may be using at your organization – think of this as a gentle nudge to standarize via social proof
This document will walk through setting up a GitHub action (open source code) although the workflow is generally the same for all build tools and CI/CD pipelines.
The action uses the Syft open source project to generate the software bill of materials (SBOM).
Setting up GitHub Integration
The GitHub integration consists of two parts:
- Installing the EdgeBit GitHub App
- Adding steps to the repositories’ workflow to generate the SBOM and upload it to EdgeBit
Installing the GitHub App
An admin should do the following:
- On the left navigation panel in the EdgeBit Console, click on “Integrations”.
- Click “New Integration” to start the GitHub app installation process.
- Grant EdgeBit access to all repos in an organization or a subset.
- Choose which project(s) the GitHub integration should be used with.
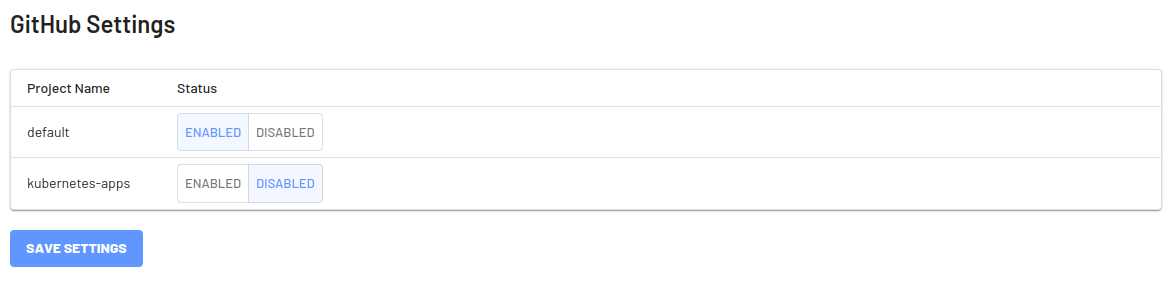
Setting Up the Action
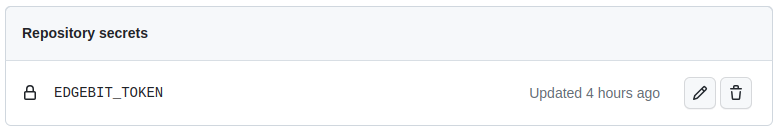
First, in the EdgeBit Console, generate a new Access Token for this repository to use. You can find this in the left hand navigation under “Access Tokens”.
Save it in GitHub under the repository GitHub Action secrets named EDGEBIT_TOKEN.
Modify the Workflows
Use this pipeline if your deployment artifact is a container.
Locate the workflow that builds the Docker container and add steps to generate and upload the SBOM.
This shows an example workflow file with the added steps.
This action assumes that the default branch is named main. When the code is merged into main, it will add a latest tag for the corresponding SBOM.
In your code repo, create .github/edgebit/container-syft.yaml with the default config file.
$ mkdir -p .github/edgebit
$ curl -sL https://edgebit.io/docs/0.x/assets/container-syft.yaml > .github/edgebit/container-syft.yaml
name: Build
on:
push:
branches:
- "main"
pull_request:
types: [opened, reopened, synchronize]
env:
CONTAINER_IMAGE: registry.example.com/foo:latest
jobs:
build-container:
runs-on: ubuntu-latest
steps:
- name: Checkout
uses: actions/checkout@v3
- name: Build and push
id: build
uses: docker/build-push-action@v4
with:
# Ensure load or push is set to true
load: true
tags: ${{ env.CONTAINER_IMAGE }}
#
# Add these steps following the build
# Assumes that the build step ID is "build"
#
- name: Generate SBOM from the container
uses: anchore/sbom-action@v0
with:
image: ${{ steps.build.outputs.imageid }}
output-file: /tmp/sbom.spdx.json
format: spdx-json
config: .github/edgebit/container-syft.yaml
upload-artifact: false
- name: Upload SBOM to EdgeBit
uses: edgebitio/edgebit-build@v1
with:
edgebit-url: https://foo.edgebit.io
token: ${{ secrets.EDGEBIT_TOKEN }}
image-id: ${{ steps.build.outputs.imageid }}
repo-digest: ${{ steps.build.outputs.digest }}
image-tag: ${{ env.CONTAINER_IMAGE }}
tags: ${{ github.ref == 'refs/heads/main' && 'latest' || '' }}
component: foo
sbom-file: /tmp/sbom.spdx.json
Use this pipeline if there isn't a deployment artifact or it is not a container.
This action assumes that the default branch is named main. When the code is merged into main, it will add a latest tag for the corresponding SBOM.
In your code repo, create .github/edgebit/source-syft.yaml with the default config file.
$ mkdir -p .github/edgebit
$ curl https://edgebit.io/docs/0.x/assets/source-syft.yaml > .github/edgebit/source-syft.yaml
In your GitHub repo, create .github/workflows/edgebit.yaml
name: EdgeBit
on:
push:
branches:
- "main"
pull_request:
types: [opened, reopened, synchronize]
jobs:
upload-sbom:
runs-on: ubuntu-latest
# to prevent duplication on a push & PR event:
if: (github.event_name == 'push' && github.event.before != '0000000000000000000000000000000000000000') || github.event_name == 'pull_request'
steps:
- uses: actions/checkout@v3
- name: Generate SBOM from the container
uses: anchore/sbom-action@v0
with:
output-file: /tmp/sbom.spdx.json
format: spdx-json
config: .github/edgebit/source-syft.yaml
upload-artifact: false
- name: Upload SBOM to EdgeBit
uses: edgebitio/edgebit-build@v1
with:
edgebit-url: https://foo.edgebit.io
token: ${{ secrets.EDGEBIT_TOKEN }}
tags: ${{ github.ref == 'refs/heads/main' && 'latest' || '' }}
component: foo
sbom-file: /tmp/sbom.spdx.json
This workflow can run independently of any other GitHub actions you may use. It does the following:
- Generates a software bill of materials (SBOM) by scanning the built container or from the current directory, detecting most common programming languages, by using the Syft open source project
- Uses your EdgeBit Access Token to upload the SBOM to EdgeBit and ties it to the specific commit and container image metadata (if using).
Fill in the required inputs at the bottom of the file.
| Input Name |
Description |
Value |
edgebit-url |
EdgeBit organization url |
Required
https://foo.edgebit.io |
The other options have default values, but may be modified if needed:
| Input Name |
Description |
Value |
token |
EdgeBit access token |
Required
${{secrets.EDGEBIT_TOKEN}} |
sbom-file |
Location of the SBOM on disk |
Required
/tmp/sbom.syft.json |
component |
Name of the component, like a frontend or backend. A new component will be created automatically if it doesn’t exist. |
Optional
my-frontend |
tags |
Identifiers to organize a single SBOM in a stream of SBOMs. Conceptually similar to container tags. |
Optional
'latest', 'v1.2.3' |
repo-token |
GitHub API token used to post comments on PRs |
Optional
${{secrets.GITHUB_TOKEN}} |
image-tag |
The tag of the container image |
Optional
Taken from the build step |
image-id |
The ID of the container image |
Optional
Taken from the build step |
Test the EdgeBit Bot
Create a new branch and commit the changes to the Actions Workflow files from the step above. Open a Pull Request to see the bot in action:
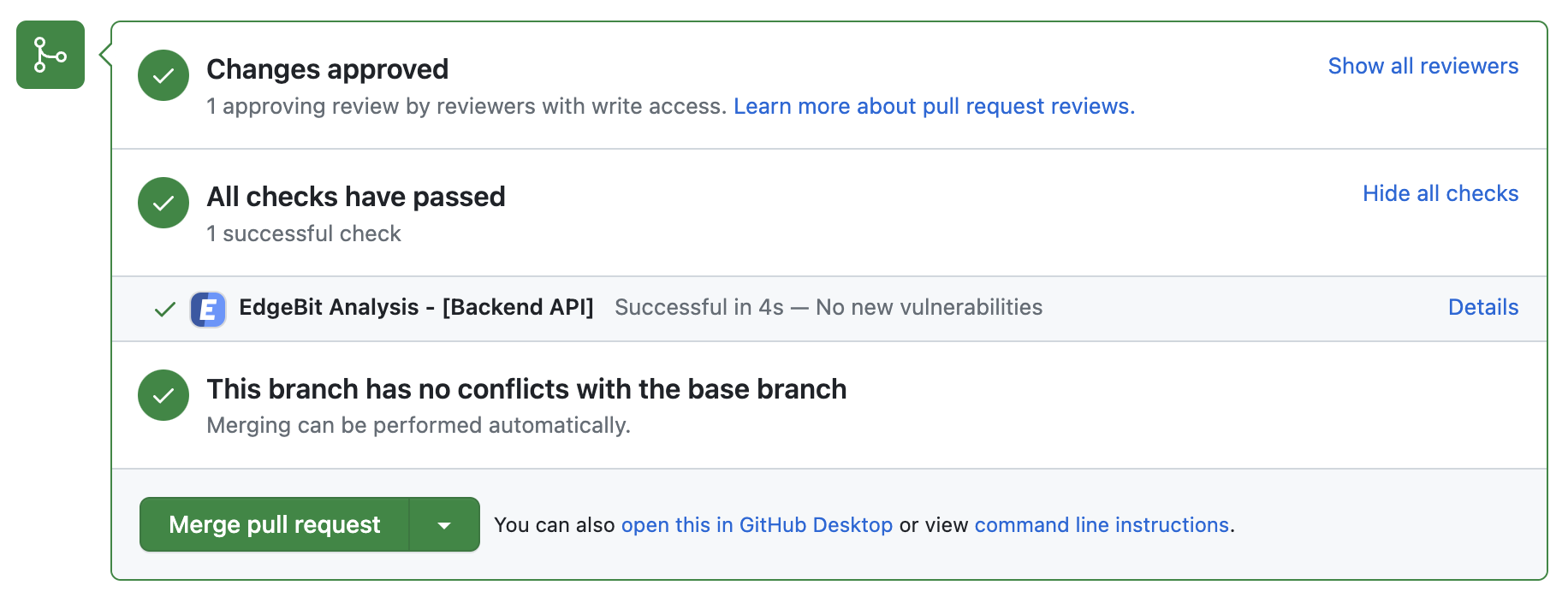
- Comments on the PR if new dependency changes are detected, highlighting:
- New vulnerabilities and supply chain risks introduced by the changes
- Confirming addition, modification or removal of dependency changes without issues
- Link to more detail within EdgeBit about the current state of all known vulnerabilities
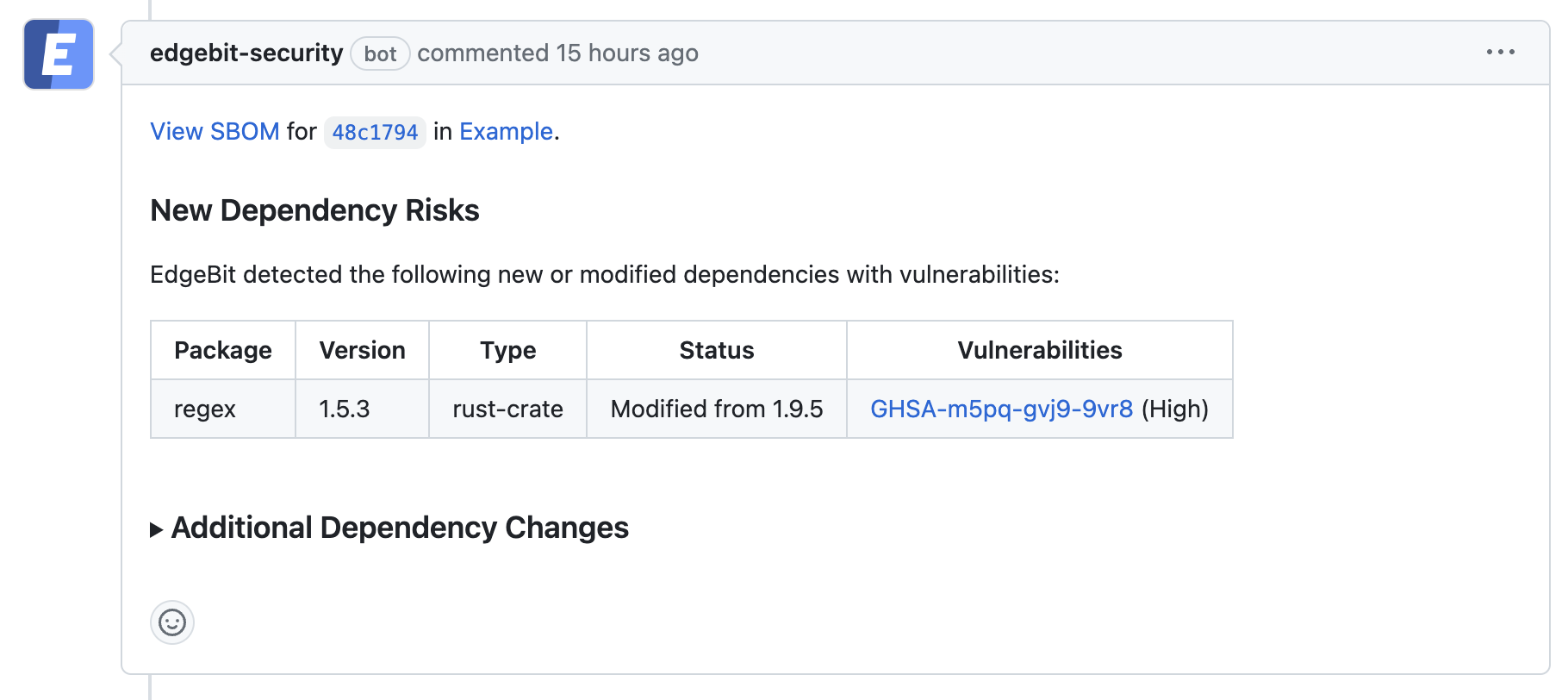
If a PR makes dependency changes and new issues are found, EdgeBit will comment with more information:
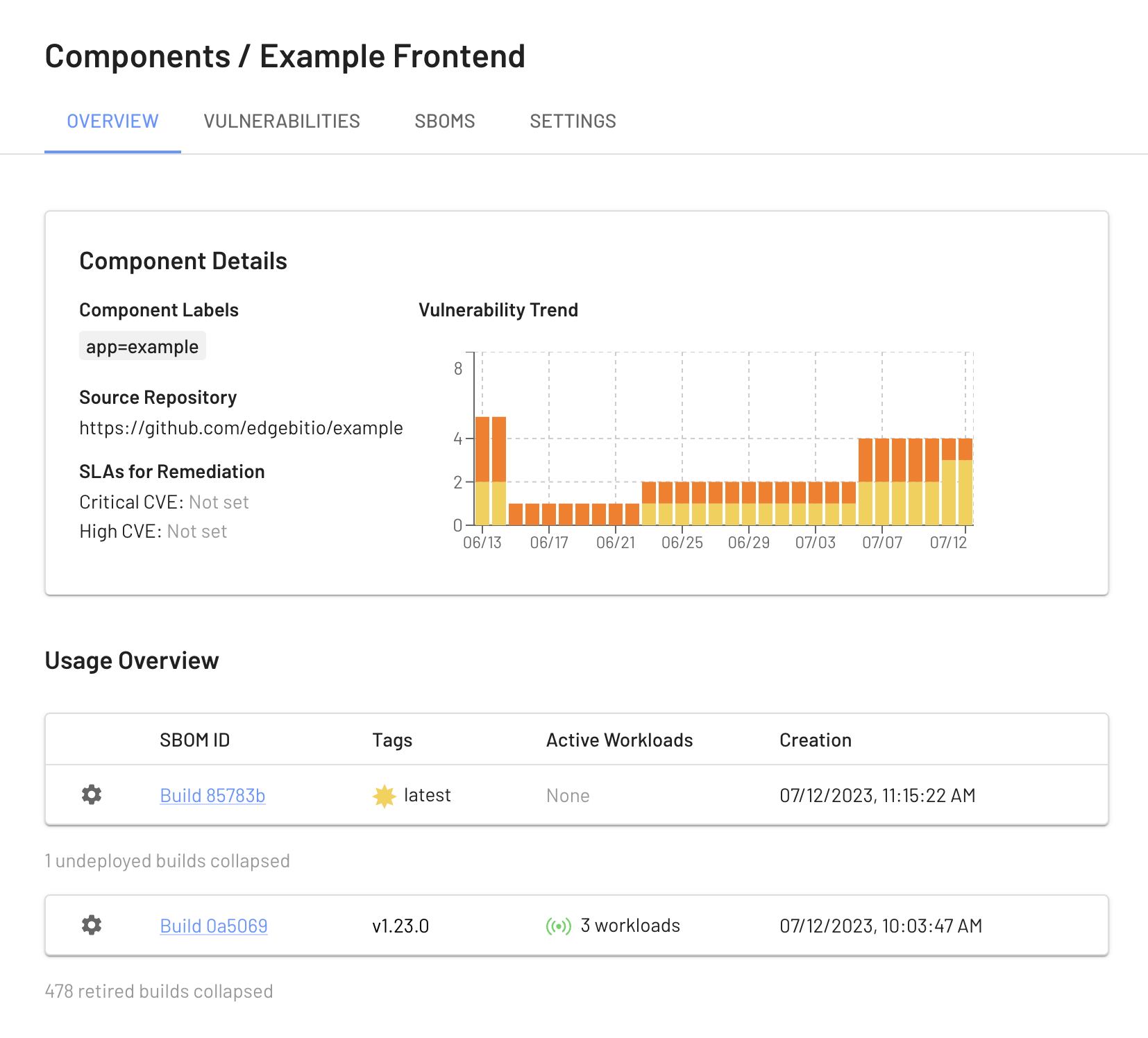
View your Build Artifacts in the EdgeBit Console
Your EdgeBit Console contains reports about each SBOM uploaded and the current state of all vulnerabilities in your software Components.
Next: Install Machine Agent





