How It Works: Tracking Active Dependencies
Connecting “build” to “run” allows EdgeBit to surface relevant vulnerabilities by understanding what is actually executing. Let’s take a deeper look at how EdgeBit determines what the active or dormant state of a dependency.
Tracking File Usage
Our definition of an active dependency is when any file contained in the package is opened and active.
We use a combination of eBPF and fanotify to track open files. It’s trickier than you think due to paths crossing cgroup and chroot boundaries for containers.
These drive our kernel requirements but are also a shifting target between distros. We’re striving for the widest possible compatibility and the easiest installation experience.
Correlating Files to Packages
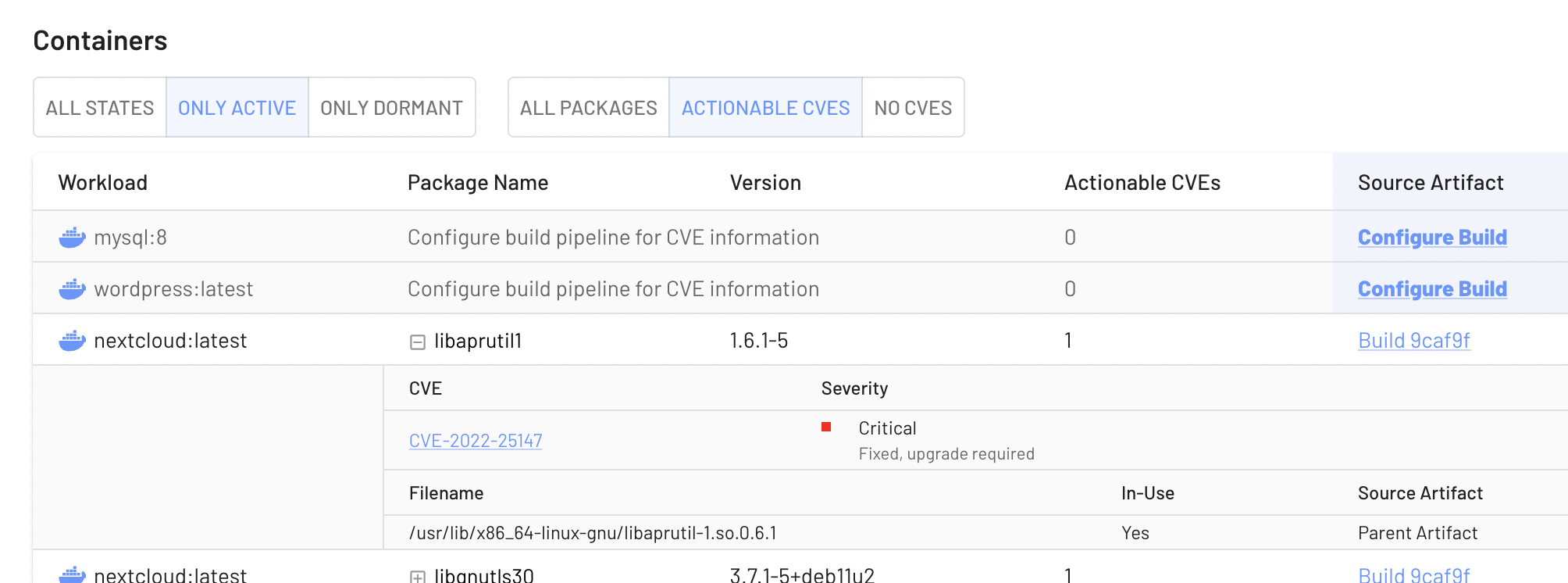
The software bill of materials (SBOM) contains information about dependencies of course. We cross reference the open files with the SBOM to determine which packages are actively used for a given workload.
You can see these files listed when you expand a package:
Tracking from Boot with Linux IMA
The most comprehensive file tracking is through Secure Boot and the Linux Integrity Measurement Architecture, which tracks every single file used from boot onward. The “measurement” side of this is calculating file hashes and it can even enforce the integrity of that file through extended metadata in the filesystem.
We’re progressing towards using the IMA system in an optional way for customers with really stringent supply chain requirements. The downside is that it does require more configuration on the Linux side, and the corresponding work to connect the SBOM inventory and hashes into the filesystem.
Please reach out if using Linux IMA for supply chain security is interesting for you – we are looking for design partners to explore this direction.

