EdgeBit gives developers context about new and modified software dependencies when submitted a pull request or pushing a new commit before it merges into main.
This context is useful for:
- vulnerabilities: understand vulnerabilities present in the selected version(s)
- recommendations: see a recommended version with fixed vulnerabilities, if available
- standardization: gain context about versions of the same dependency that other teams may be using at your organization – think of this as a gentle nudge to standarize via social proof
This document will walk through installing EdgeBit GitHub integration into your GitHub organization(s). Multiple organizations can be mapped into one or many EdgeBit projects.
GitHub Behavior Overview
Developers will see a new EdgeBit check on their PRs:
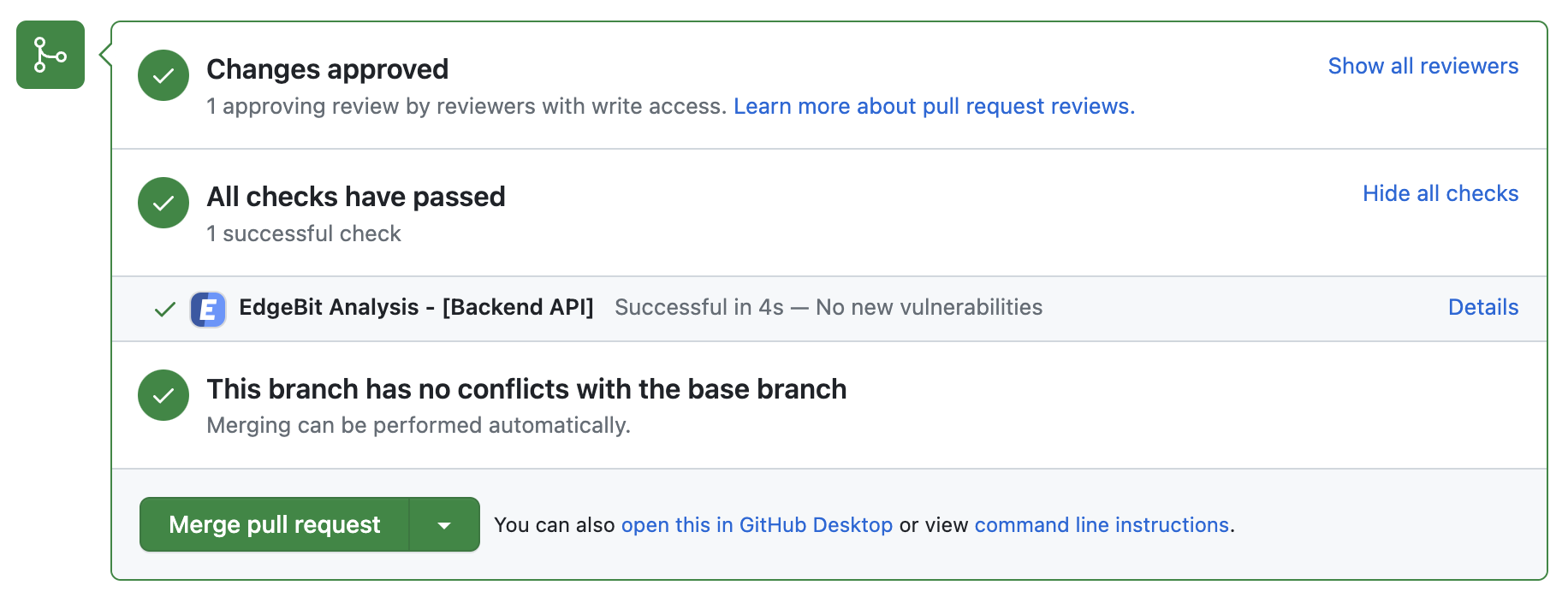
- Generates and uploads an SBOM on each push to the repository
- Comments on the PR if new dependency changes are detected, highlighting:
- New vulnerabilities and supply chain risks introduced by the changes
- Confirming addition, modification or removal of dependency changes without issues
- Link to more detail within EdgeBit about the current state of all known vulnerabilities
Setting up the GitHub Integration
The GitHub integration consists of two parts:
- Installing the EdgeBit GitHub App
- Adding steps to the repositories’ workflow to generate the SBOM and upload it to EdgeBit
Installing the GitHub App
An admin should do the following:
- In the EdgeBit Console, click on “Integrations” in the left navigation pane.
- Click “New Integration” to start the GitHub app installation process.
- Grant EdgeBit access to all repos in an organization or a subset.
- Choose which project(s) the GitHub integration should be used with.
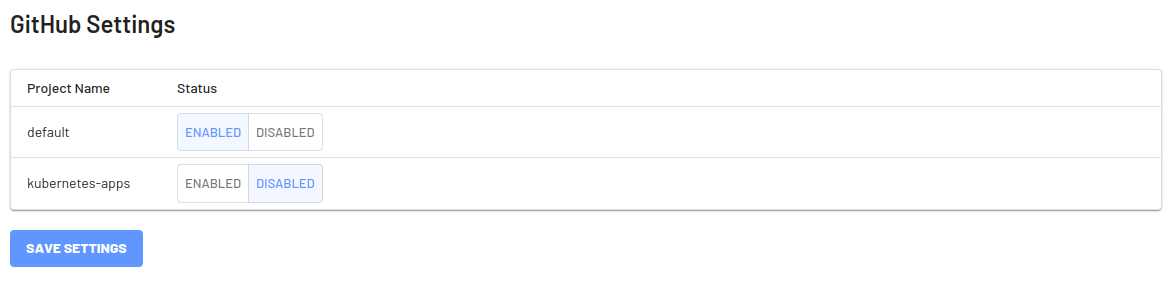
Setting Up Repositories
First, navigate over to the Component and click “Import from GitHub” to view a list of list of available repositories.
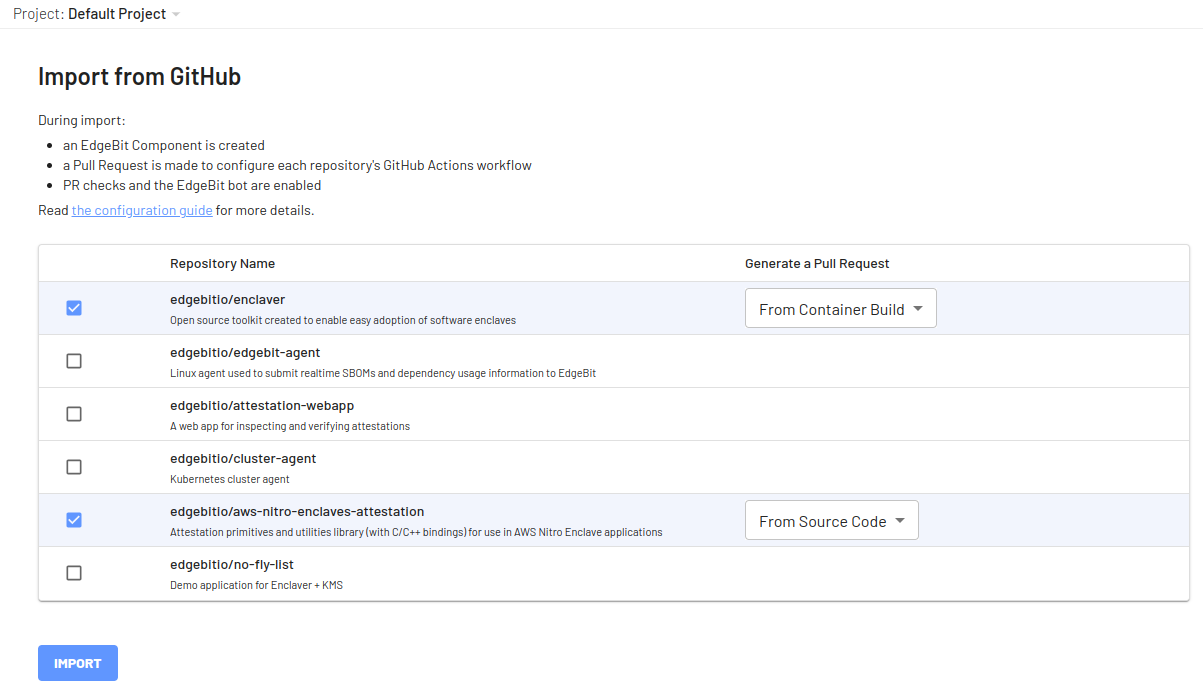
Select the repository(s) along with the type of Pull Request to open in order to modify the Actions Workflows.
For container builds, which are recommended, the SBOM generation step is intelligently added after your container is built without touching the rest of the Actions workflow.
For more control, you can customize GitHub Actions.
A new EdgeBit component is created along side a Pull Request with the changes to the workflow definitions.
Setting up the secret with the EdgeBit access token
Before merging the set up Pull Request, create and save an EdgeBit access token as a repository secret.
You can generate a unique access token per repository or use a single token for multiple repos.
In the EdgeBit Console, generate a new Access Token. You can find this in the left hand navigation under “Access Tokens”.
Save it in GitHub under the repository GitHub Action secrets named EDGEBIT_TOKEN.
Once that PR is merged, the Component will track the SBOMs and you can test out the new supply chain checks in your workflow.
Test the EdgeBit Bot
Ensure the set up Pull Request is merged before testing out the bot.
Open a Pull Request to see the bot in action. EdgeBit’s GitHub app allows Developers to see a new EdgeBit check on their PRs:

- Comments on the PR if new dependency changes are detected, highlighting:
- New vulnerabilities and supply chain risks introduced by the changes
- Confirming addition, modification or removal of dependency changes without issues
- Link to more detail within EdgeBit about the current state of all known vulnerabilities
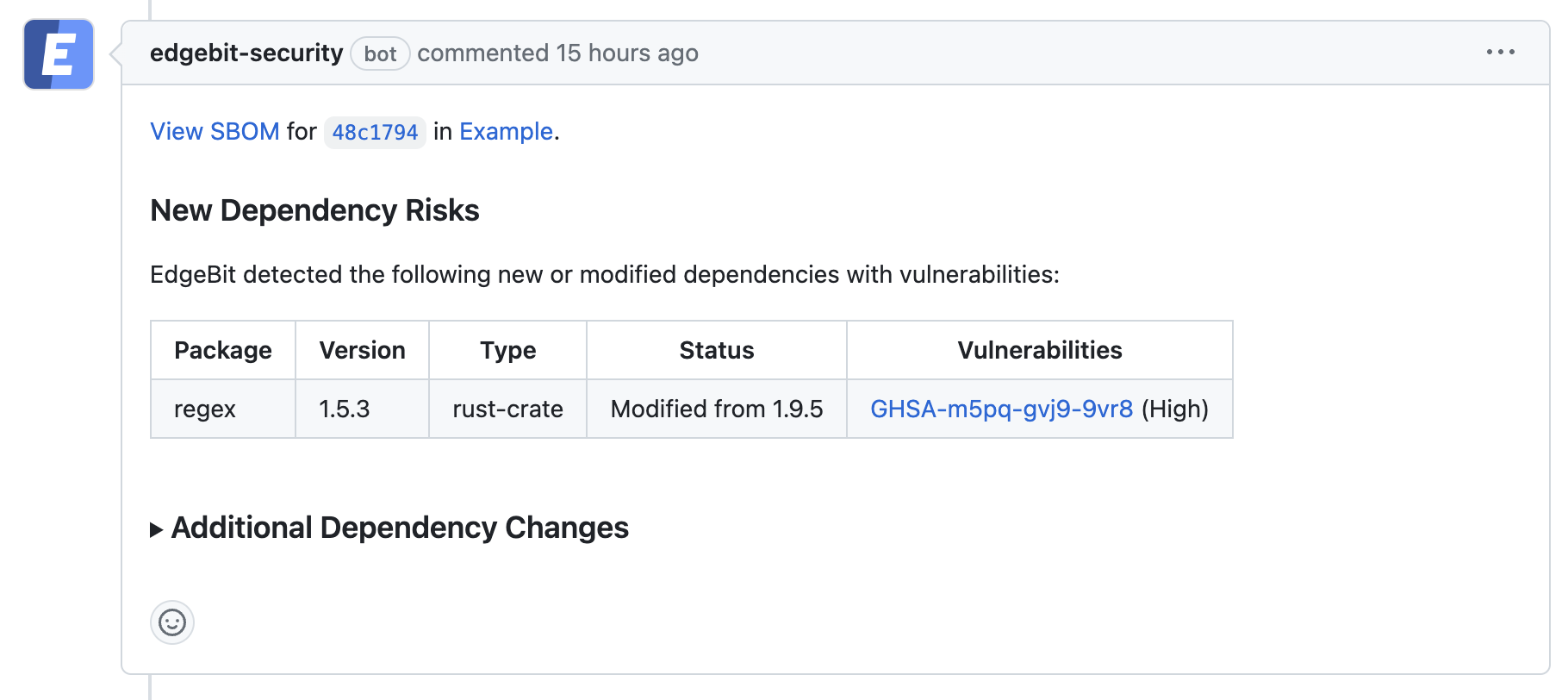
If a PR makes dependency changes and new issues are found, EdgeBit will comment with more information:
View your Build Artifacts in the EdgeBit Console
Your EdgeBit Console contains reports about each SBOM uploaded and the current state of all vulnerabilities in your software Components.
Next: Install Machine Agent





