EdgeBit gives developers context about new and modified software dependencies when submitted a pull request or pushing a new commit before it merges into main.
This context is useful for:
- vulnerabilities: understand vulnerabilities present in the selected version(s)
- recommendations: see a recommended version with fixed vulnerabilities, if available
- standardization: gain context about versions of the same dependency that other teams may be using at your organization – think of this as a gentle nudge to standarize via social proof
This document will walk through using the SBOM and attestation capabilities of docker buildx build and docker buildx bake which uses Docker BuildKit.
This guide will use Docker to build a container image and SBOM, store both in a remote container registry, and then use the EdgeBit CLI to ingest the stored SBOM.
Setting Up the Pipeline
First, in the EdgeBit Console, generate a new Access Token for this repository to use. You can find this in the left hand navigation under “Access Tokens”.
$ export EDGEBIT_API_KEY='dnrekvq95CJ6_JcVixpfTEx8L3k3hDsggoqSr'
$ export EDGEBIT_URL='https://foo.edgebit.io'
Install the CLI tools:
$ curl -sL https://install.edgebit.io/releases/edgebit-cli/v0.8.1/edgebit-cli_Linux_x86_64.tar.gz --output ebctl.tar.gz
$ tar -xvf ebctl.tar.gz
In your pipeline, run the following commands to generate an SBOM during your container build. This guide assumes you have a BuildKit builder already configured.
$ export IMAGE='registry.example.com/foo:latest'
$ export NAME='foo'
$ docker buildx build \
--tag $IMAGE \
--sbom=true \
--provenance=true \
--push \
.
Once complete, you should see both a new container in your registry but also an SBOM and provenance document tied to it. While most container registry UIs don’t render these, EdgeBit can fetch and enrich them easily.
Upload SBOM to EdgeBit
First, compile some commit info in order to identify where this SBOM was generated from:
$ export BASE_BRANCH='main'
$ export CURRENT_BRANCH=$(git rev-parse --abbrev-ref HEAD)
$ export LATEST_SHA=$(git rev-parse HEAD)
$ export EDGEBIT_TAG=$(echo "$CURRENT_BRANCH" | grep -q "$BASE_BRANCH" && echo 'latest' || echo "$CURRENT_BRANCH")
Next, gather some container details from the registry. Be sure to configure access to your registry. We’re specifying the amd64 architecture here and read below if you use multiple architectures:
$ export DIGEST_ID=$(docker buildx imagetools inspect --raw "$REPO" | jq -r '.manifests[] | select(.platform.architecture=="amd64") | .digest')
$ export IMAGE_ID=$(docker buildx imagetools inspect --raw "$REPO"@$DIGEST_ID | jq -r '.config.digest')
Fetch the SBOM from the registry and upload it to EdgeBit:
$ ebctl upload-sbom \
--component $NAME \
--tag $EDGEBIT_TAG \
--repo https://github.com/org/repo \
--commit $LATEST_SHA \
--image-tag $IMAGE \
--image-id $IMAGE_ID \
--repo-digest $(docker buildx imagetools inspect --format '{{ json .Manifest }}' $IMAGE | jq -r .digest) \
registry:"$(IMAGE)"
Multiple Architecture Images
If you build multiple architectures, you have two options: pick one of them to use for security tracking, or upload each architecture individually. Both strategies are perfectly valid.
When you point ebctl at a multi-arch manifest, make sure you specify each platform and architecture in two places:
- specify the architecture when fetching the
DIGEST_ID and IMAGE_ID information
- specify the
--resolve-platform=linux/amd64 flag in addition to the other options in ebctl upload-sbom
It is most common to loop through all of your architectures in your build script, executing the above steps for each combination.
Test the EdgeBit Bot
Create a new branch and commit the changes to watch your pipeline run.
Set Up the GitHub app
Optionally, use the EdgeBit’s GitHub app to allow Developers to see a new EdgeBit check on their PRs:
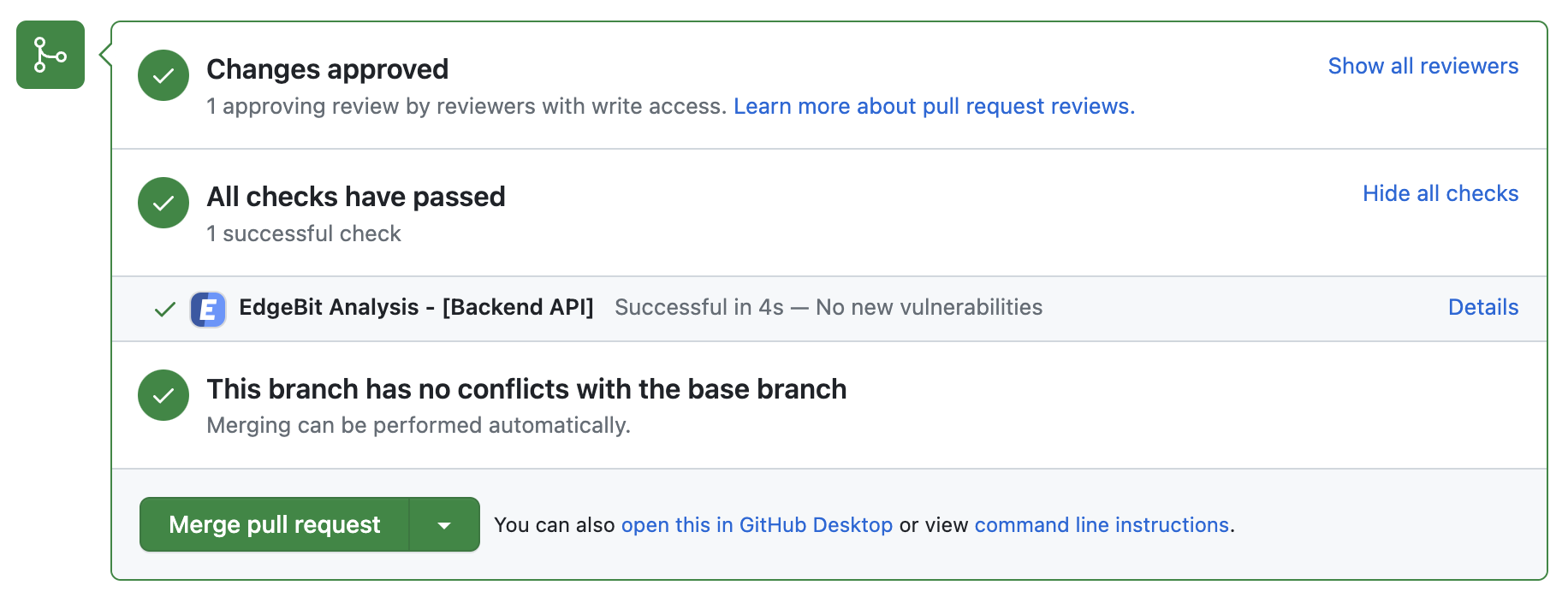
- Comments on the PR if new dependency changes are detected, highlighting:
- New vulnerabilities and supply chain risks introduced by the changes
- Confirming addition, modification or removal of dependency changes without issues
- Link to more detail within EdgeBit about the current state of all known vulnerabilities
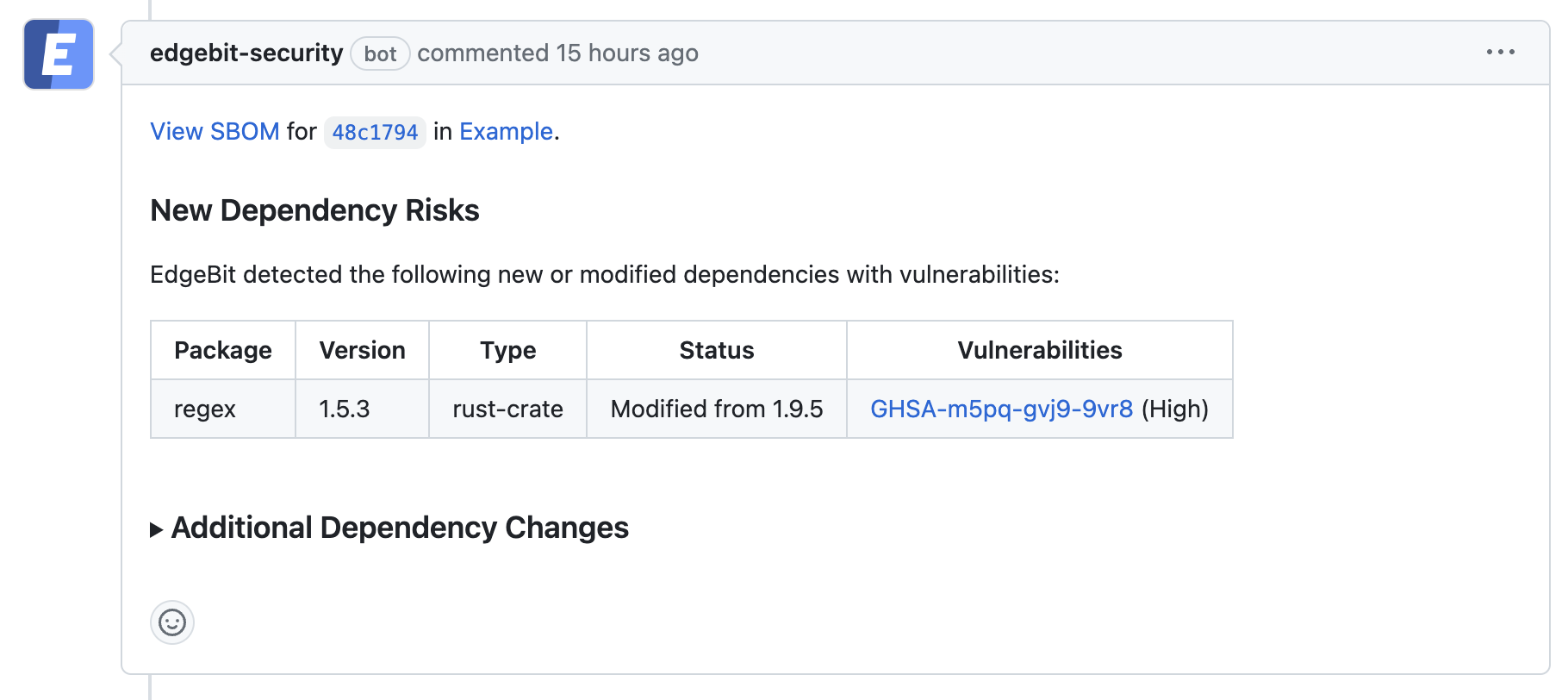
If a PR makes dependency changes and new issues are found, EdgeBit will comment with more information:
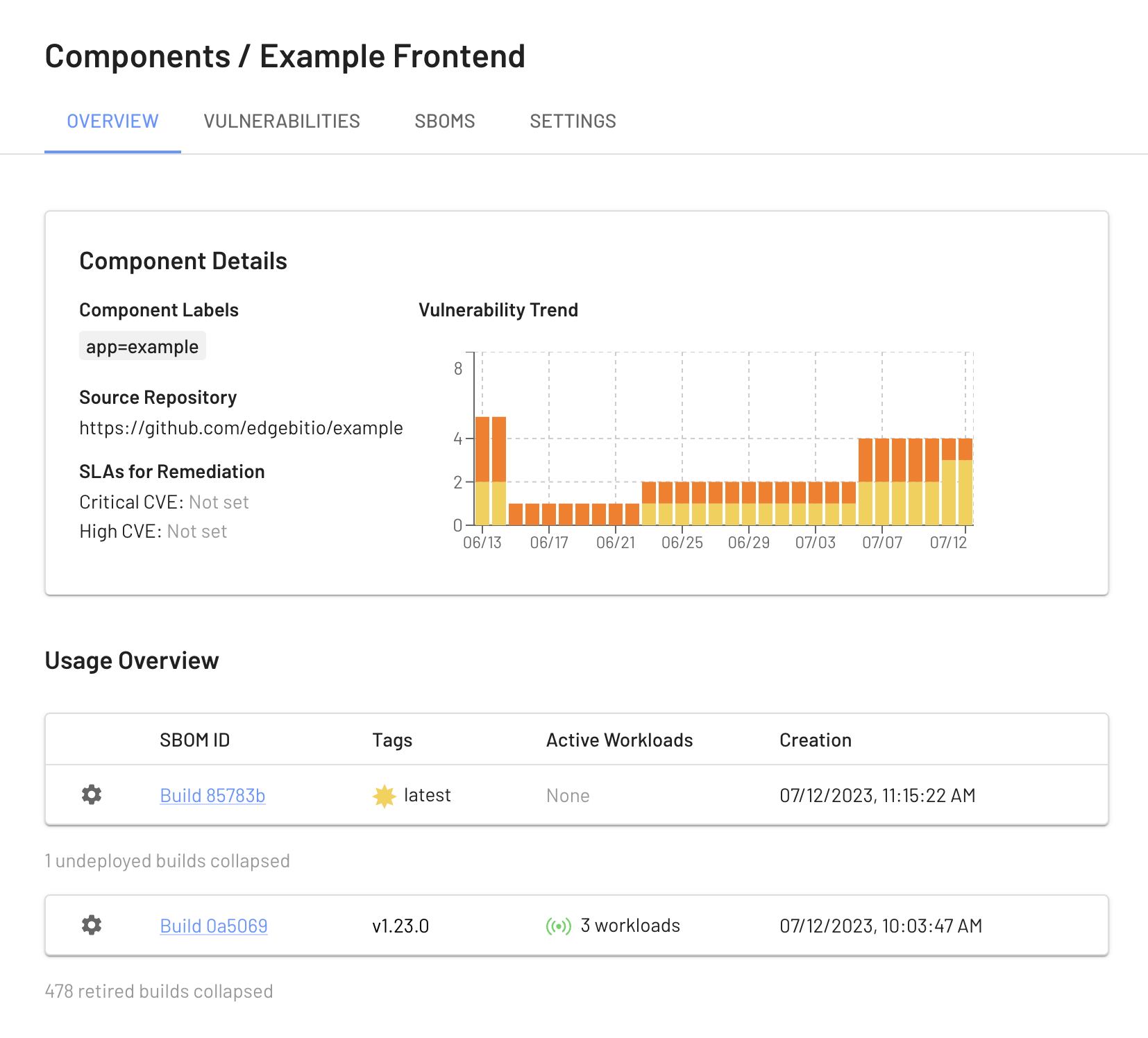
View your Build Artifacts in the EdgeBit Console
Your EdgeBit Console contains reports about each SBOM uploaded and the current state of all vulnerabilities in your software Components.
Next: Install Machine Agent



