Concepts
EdgeBit is designed to secure software supply chains for companies with multiple engineering teams and any size server fleet.
High Level Concepts
Software Bill of Materials (SBOMs)
A Software Bill of Materials (SBOM) contains an inventory of dependencies that make up your application. EdgeBit uses both build-time SBOMs from your CI pipeline and real-time SBOMs from your server fleet to secure your supply chain.
SBOMs are uploaded to the EdgeBit SaaS service and are continually enriched with:
- relevant vulnerabilities for each dependency
- real-time usage of each dependency in your server fleet
- facts about source of each dependency
A common pattern is to have a single build pipeline that builds a separate artifact/container for a frontend and a backend, with an SBOM is generated for each artifact. SBOMs are “tagged” with metadata like a version or floating tags like latest (just like container tagging) and map directly to a Component.
Get started:
Configure Build Pipeline
Install Linux Agent
Install on Kubernetes
Components
Components represent a functional piece of your software, like a frontend, backend, or microservice. Components typically come from a single code repo or a subdirectory of a monorepo and represent a stream of SBOMs produced by your build pipeline.

Modeling this as a stream is useful to understand if a security issue is fixed but not deployed yet, or inventory the set of versions currently deployed across regions/zones.
Each Component has a unique set of detected Vulnerabilities found in the stream of SBOMs. Each vulnerability is tracked from first observation to meet the SLA for fixing it. Suppressions or modifications to the severity of a vulnerability are unqiue to the Component, in order to accurately represent the risk when dependencies are used differently by teams in your organization.
Get started:
Create Components
Workloads
Workloads represent instances of the software you’re responsible for maintaining, both app/container instances and base operating system instances.
Worklaod information is sourced in real-time from your infrastructure via the EdgeBit Node Agent and Cluster Agent.
Infrastructure
Build Pipelines
Build pipelines build and test your software of course, but they also upload SBOMs to EdgeBit for analysis and enrichment. If configured, any issues found are reported directly inside of a Pull Request or Merge Request as a dependency is being updated.
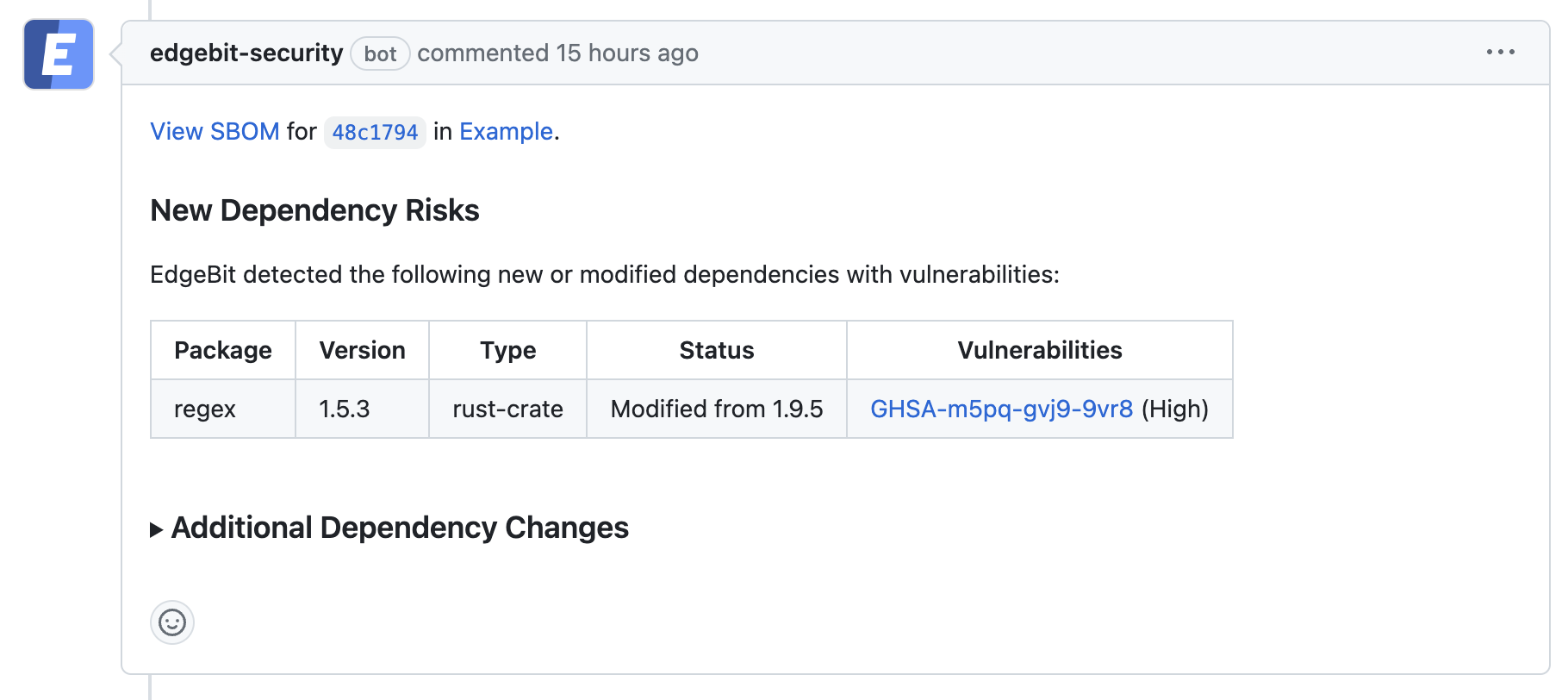
Vulnerabilities are also tracked at the Component level across SBOMs from your build pipelines.
Get started:
Configure GitHub Actions
Configure AWS CodeBuild
Configure Generic Pipeline
Machines
EdgeBit tracks a holistic view of each Machine – taking in the combination of base operating system and application vulnerability state in real-time.
This real-time inventory allows security teams to understand “where is log4j used right now?” or “which team hasn’t rolled out the fix for CVE-123456?”
Even in a Kubernetes world, the base OS is critical to security and node groups can be disrupted or blocked from upgrading the operating system.
Get started:
Install Linux Agent
Install on Kubernetes


