Getting Started with Dependency Autofix
Dependency Autofix is a security tool designed to resolve application security issues and keep packages up to date.
Autofix operates continuously to plan and execute “upgrade proposals” across your repositories and determine impact to each of your apps, based on how they call into their dependencies.
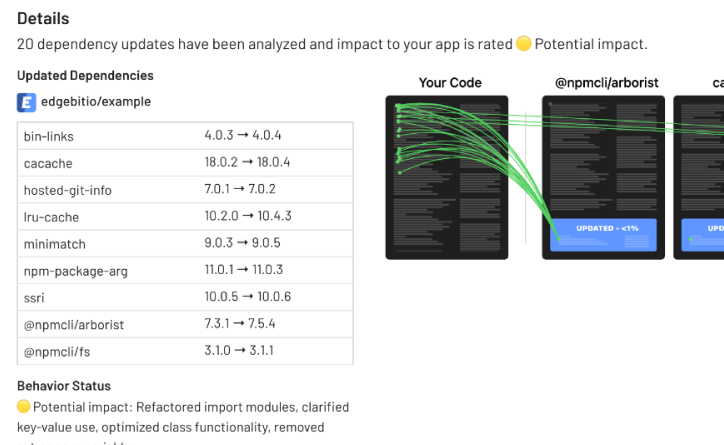
The vast majority of upgrades do not impact apps and merging these updates is safe, keeps you up to date, avoids scrambling when you’re far behind and a security issue is found. The security benefits of Dependency Autofix are so great that we think you should automate them via your change management process.
After following the steps below, Proposals will start being generated within minutes to about an hour, based on the size of your codebase.
Install GitHub app
Install the EdgeBit app into your GitHub organization. Log into your EdgeBit organization and navigate to Integrations > GitHub.
Create Components
Create Components for each functional piece of your software, like a frontend, backend, or microservice. Components typically come from a single code repo or a subdirectory of a monorepo. It’s better to have more components than less.
Each Component is continously inventoried and Autofix Proposals are generated automatically.
Engineers or security analysts can trigger their own Proposals at any time.
More about Dependency Autofix
For more details about Dependency Autofix, you can read the announcement blog post or learn more about how it works behind the scenes.
Dependency Autofix works alongside with EdgeBit’s Pull Request checks, which can protect your apps from vulnerabilities in newly added dependencies before they merge.
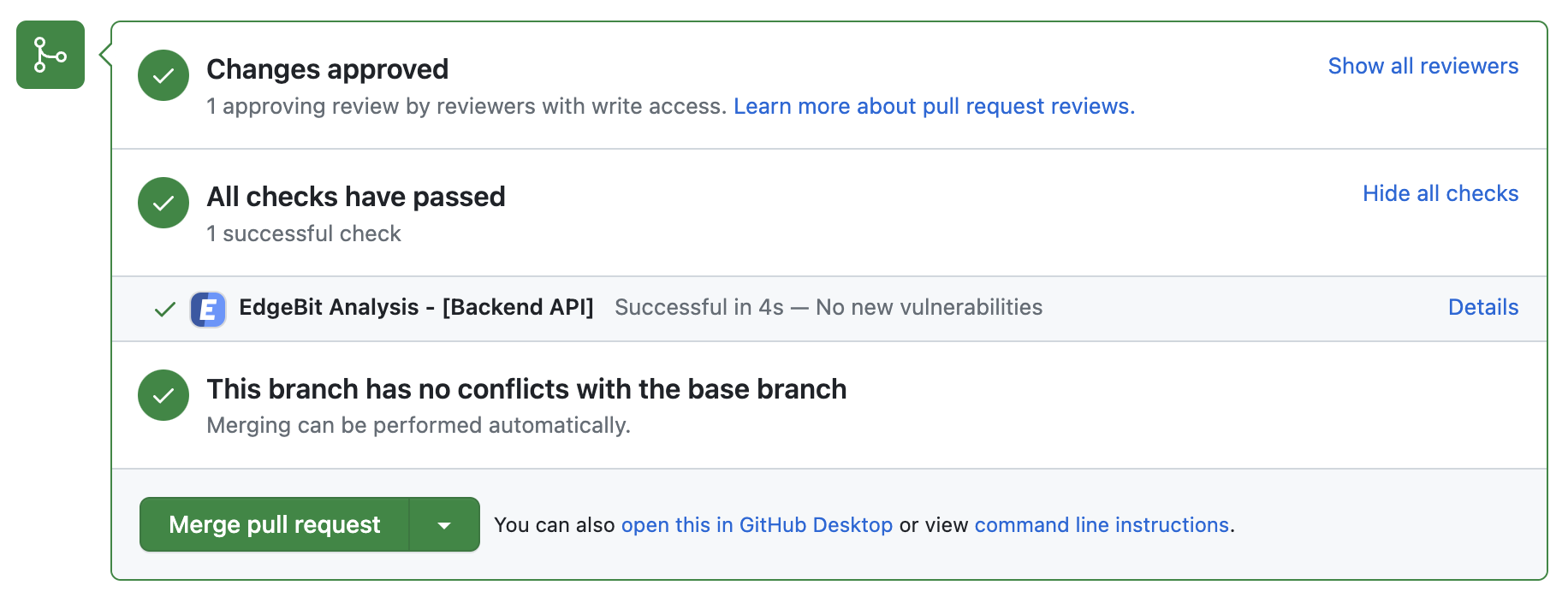
Configure your build pipeline to submit an SBOM to EdgeBit on each run to get started.



