Upgrade Proposals
A Dependency Autofix “Proposal” is a set of dependency and library updates which are generated, analyzed and evaluated for risk as a group.
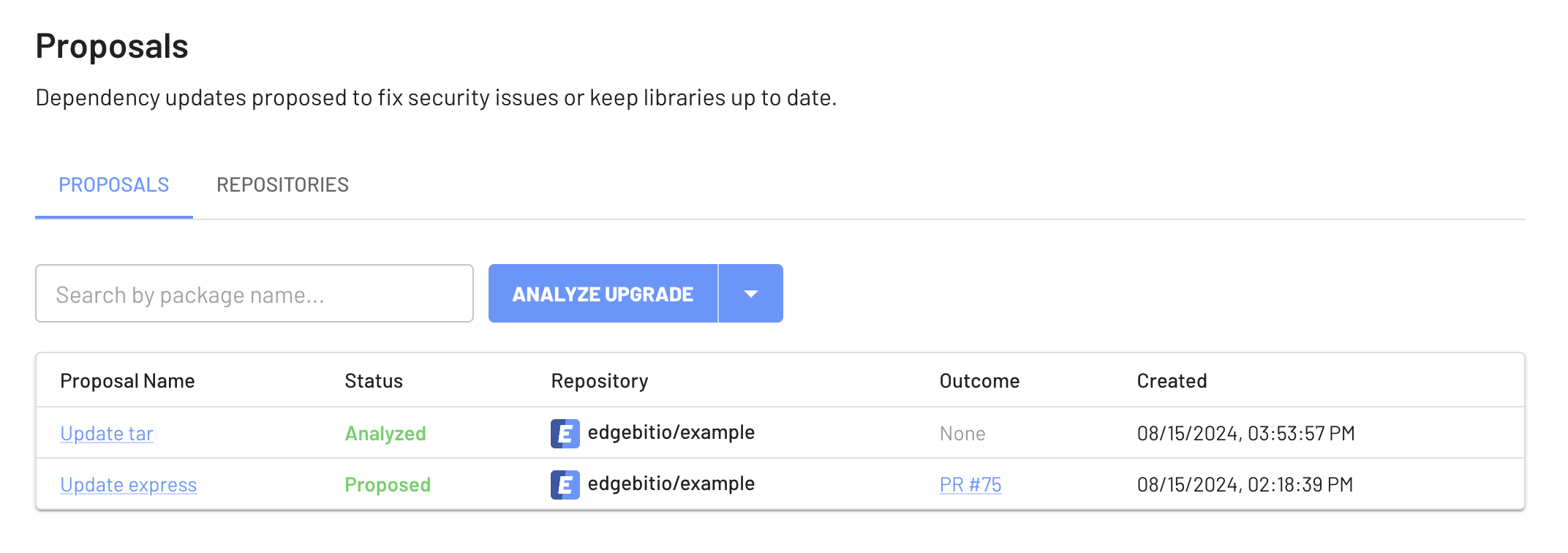
Typically a proposal is focused on upgrading a single package – containing a vulnerability or simply out of date – which will then require more transitive dependencies to be added, removed or upgraded.
All of these changes can affect your app, especially when transitive upgrades touch packages that are already in use by other parts of your application.
Upgrade Analysis Report
By default, each Proposal has a detailed report of how your application code interacts with each of the dependencies that were upgraded.
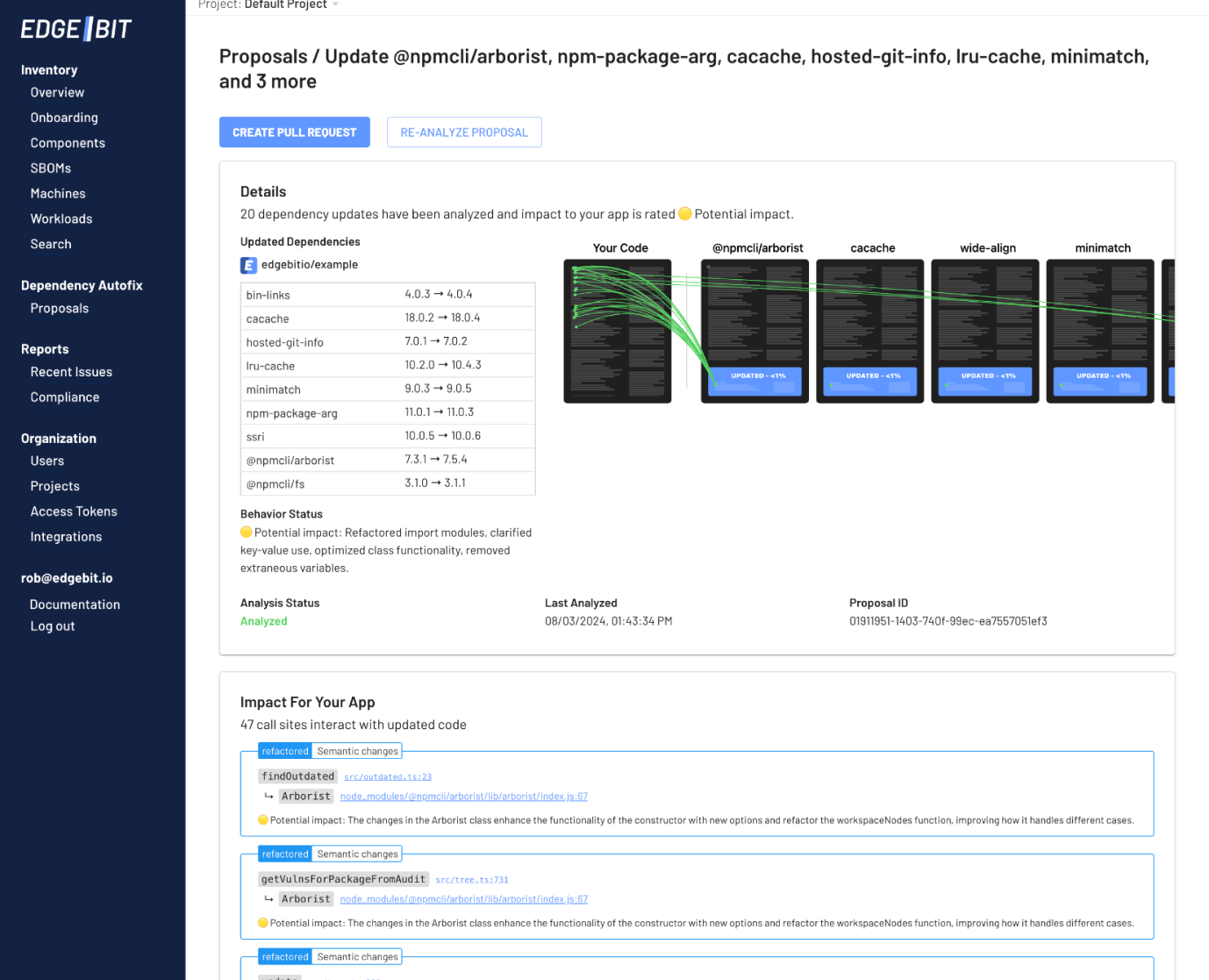
Each of your call sites that is affected by the upgrade is highlighted. AI is used to do a first pass analysis on the changes to the specific function in the upgraded depenency. Engineers have a very specific starting point for a second look, versus scouring release notes and reading code manually.
If 0 call sites are impacted, the Proposal is updating transitive updates exclusively. The trickiest part of transitive updates is to understand how deeply the packages are used from your top-level dependencies. Dependency Autofix has a visualization focused on this understanding instead of looking at affected call sites (which don’t exist).
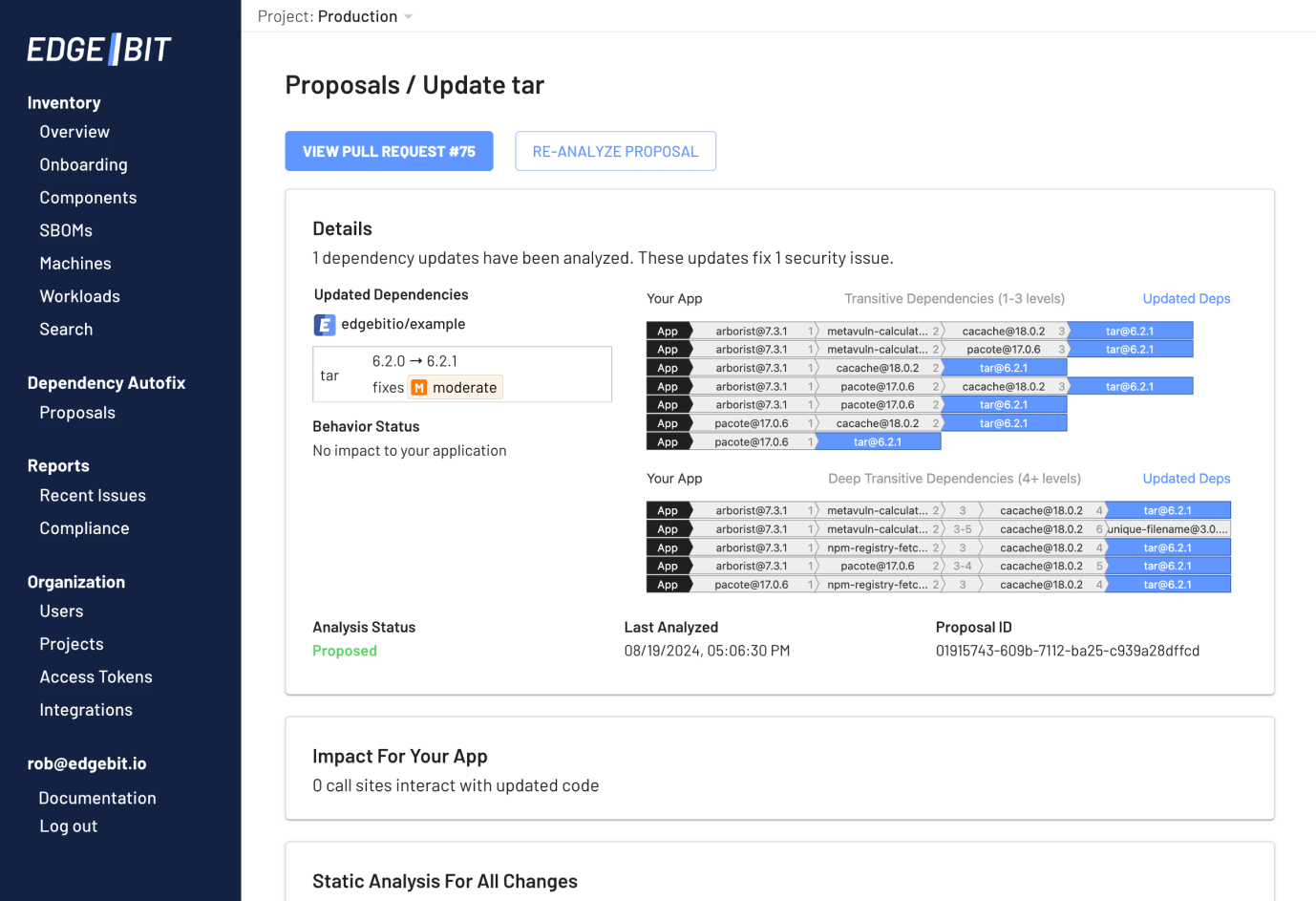
Quantifying Risk for Your App
EdgeBit’s analysis engine walks your entire code base before and after the proposed upgrade to determine where your app code calls into each dependency.
Call sites are considered affected by the upgrade if they are both reachable in the execution of your code and mutated by the upgrade. Our analysis engine is smart enough to ignore non-semantic changes to reduce noise.
For many upgrades, no call sites are mutated and the update is considered no risk or very very low risk. Merging these updates into your code base is safe, keeps you up to date, avoids scrambling when you’re far behind and a security issue is found.
Solving the “Lack of Tests” Problem
Many frontend teams lack tests in certain areas or have no tests that exercise dependencies enough to give them confidence that a passed CI run is a useful signal.
EdgeBit’s code analysis can make a similar determination about breaking changes that a test suite would but without the effort required to implement or maintain it.
The result is your engineers gaining insight into the exact area where they should focus their code review and EdgeBit augments the lack of tests with code analysis and risk scoring.



