EdgeBit’s May release expands our previously announced ability to deploy through Kuberentes and connect your Kubernetes workloads back to supply chain artifacts in your build pipelines.
Civo Kubernetes
Civo Kubernetes comes in two flavors, one using k3s with Alpine Linux and one using Talos Linux. The EdgeBit Linux agent has been tuned to some of the differences between k3s and mainstream Kubernetes.
Our engineering team worked with the Civo team to streamline Alpine configuration of fanotify, eBPF and BTF (BPF Type Format, the metadata format which encodes the debug info for BPF programs).
We’re working to complete the same work for using Talos Linux. Until then, use EDGEBIT_PKG_TRACKING=false to skip active/dormant dependency determination while still tracking workloads in the cluster.
Check out the full Kubernetes guide for Civo deployment instructions.
New guide for AWS CodeBuild
A new guide for AWS CodeBuild has been released which walks through integrating SBOM generation, the EdgeBit Build agent, and AWS SecretsManager into a pipeline to secure your software supply chain.
EdgeBit Linux agent updates
The EdgeBit Linux agent gained a number of performance improvements and bug fixes as well.
Active dependency tracking became more performant by using an LRU list to reduce sending duplicates and reports to EdgeBit’s SaaS are now batched into 1 second intervals. Thundering herd issues are also alleviated with added jitter.
The agent has better handling of stopped workloads, which balances the need for full visibility and large workload quantities when used with active machines or Kubernetes clusters.
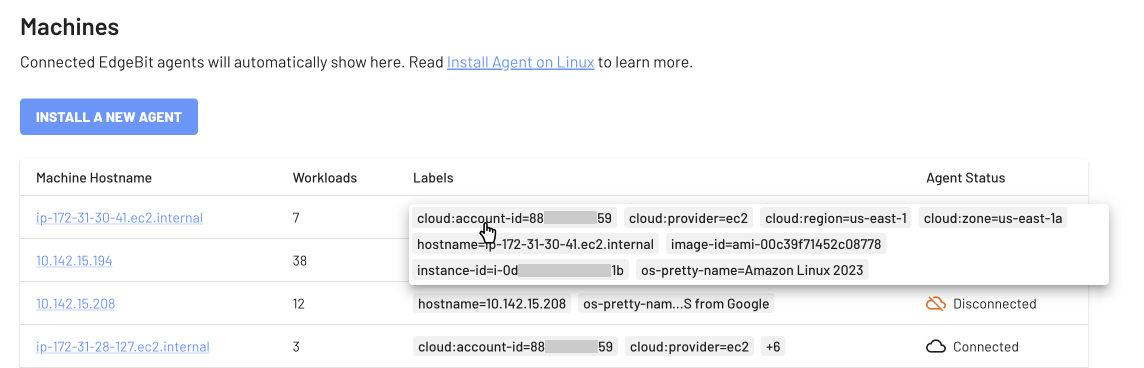
Workloads now gain additional metadata for organization and reporting. Kubernetes workloads are enriched with namespace and pod name. Workloads on cloud machines are enriched with the cloud details like account id, region, etc.
Read the v0.4.0 release notes for more info and to use the installation artifacts.
