EdgeBit’s October release brings new tools for security teams to optimize their vulnerability management workflows:
- SLA tracking with customizable policies per Project
- Automatic VEX report generation per Component
- Expanded GitHub integration for a better PR experience
- New Jira integration for plugging into existing security workflows
We previously announced expanded tracking for OS vulnerabilities and recently used it to reverse engineer GKE and EKS patching practices. It is very cool to see Google and Amazon prioritizing fixes using the same methodology as EdgeBit.
SLA tracking
Tracking remediation deadlines is core to remaining in compliance with SOC2, ISO 27001, PCI and many other programs. EdgeBit now tracks SLAs against your organization’s policy and also applies real-time suppressions for irrelevant issues to keep your compliance scope as accurate as possible.
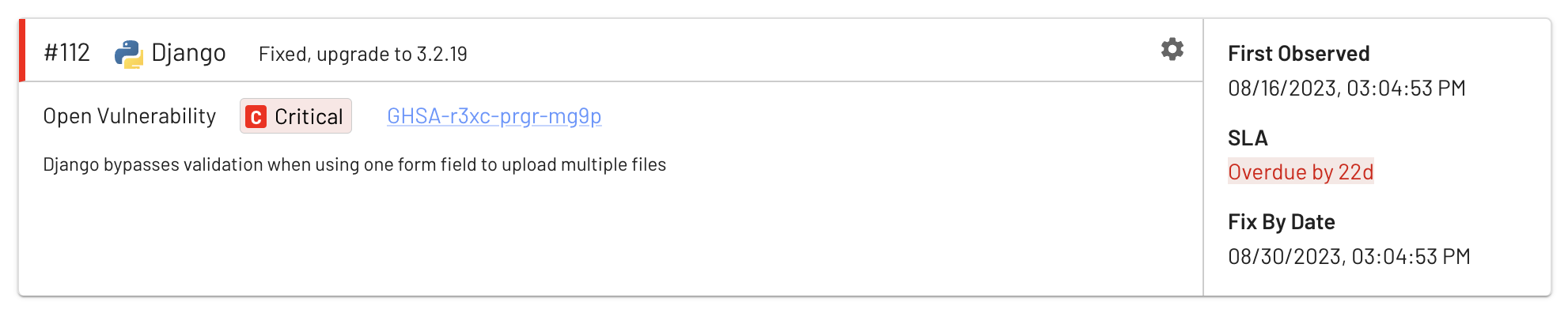
“Fix by” dates are also recorded into Jira Issues via our enhanced Jira integration, which you can read about below.
Download VEX
EdgeBit users can now download a VEX report alongside their SBOM for any component. VEX stands for Vulnerability Exploitability eXchange, which is a mechanism to communicate that a piece of software is or isn’t vulnerable to specific issues that might be found in an SBOM.
Why does this matter? Security and operations teams now have a machine-readable artifact that can be passed into security scanners to suppress distracting output related to vulnerabilities that are not relevant or have already been fixed.
EdgeBit uses the real-time context from how your app is running on your server fleet to populate VEX reports. When a security issue in your software is first found or remediated, a VEX statement is issued or updated. For open issues, the statement communicates whether the issue is found to affect or not affect your app based on how it’s observed while running.
Here’s an example of a report:
{
"@context": "https://openvex.dev/ns/v0.2.0",
"@id": "https://openvex.dev/docs/public/vex-97b4fb302dc42eeee13724c1e85bba58ab687dd27651f8bfb63d9e7d6ff11804",
"author": "EdgeBit",
"role": "Realtime Security Platform",
"timestamp": "2023-09-18T14:07:00.1097922Z",
"version": 1,
"statements": [
{
"vulnerability": {
"@id": "CVE-2021-22922"
},
"products": [
{
"@id": "pkg:deb/debian/libcurl4@7.74.0-1.3+deb11u7?arch=amd64&upstream=curl&distro=debian-11",
"identifiers": {
"purl": "pkg:deb/debian/libcurl4@7.74.0-1.3+deb11u7?arch=amd64&upstream=curl&distro=debian-11"
}
}
],
"status": "fixed",
"impact_statement": "EdgeBit automated analysis indicates that the vulnerable code is fixed"
},
…snip…New GitHub app integration
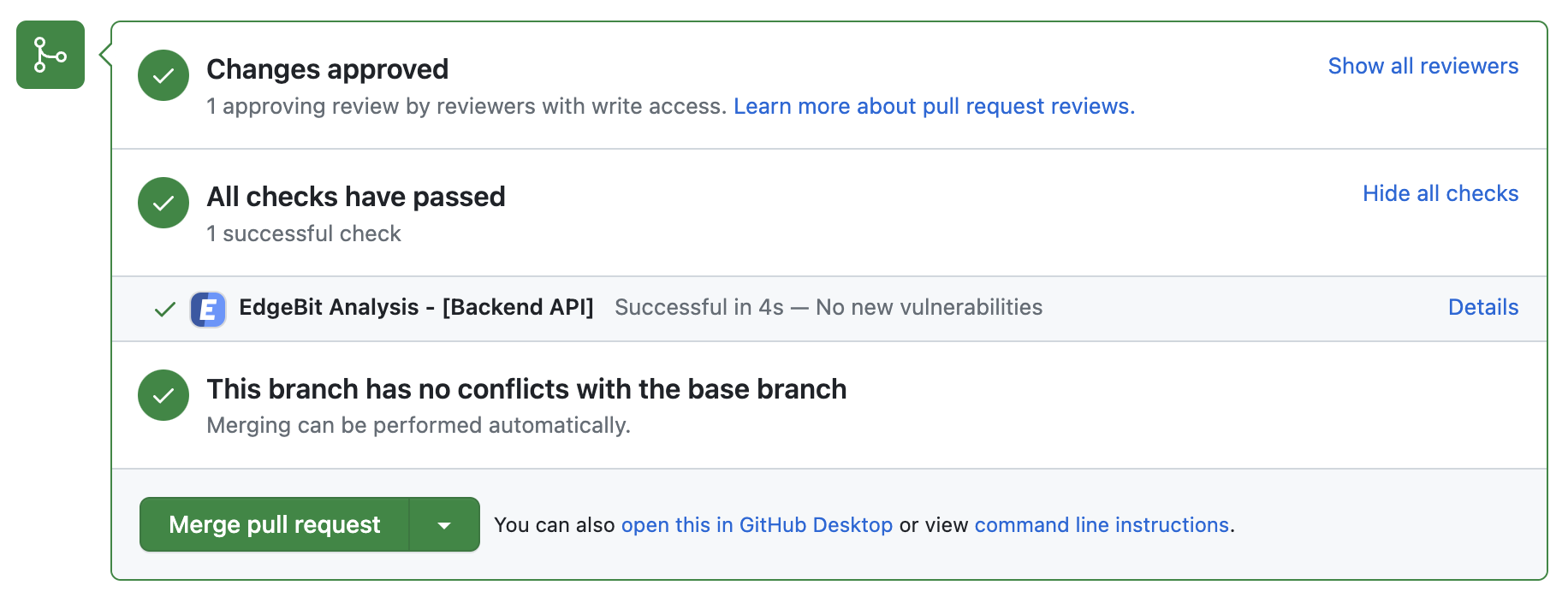
EdgeBit has a new GitHub app integration to complement our existing GitHub Actions. Once installed, a new “check” is added to Pull Requests on your repos to signal that changes are free from security risks.
If issues are found, details are provided in the comment without having to switch contexts:
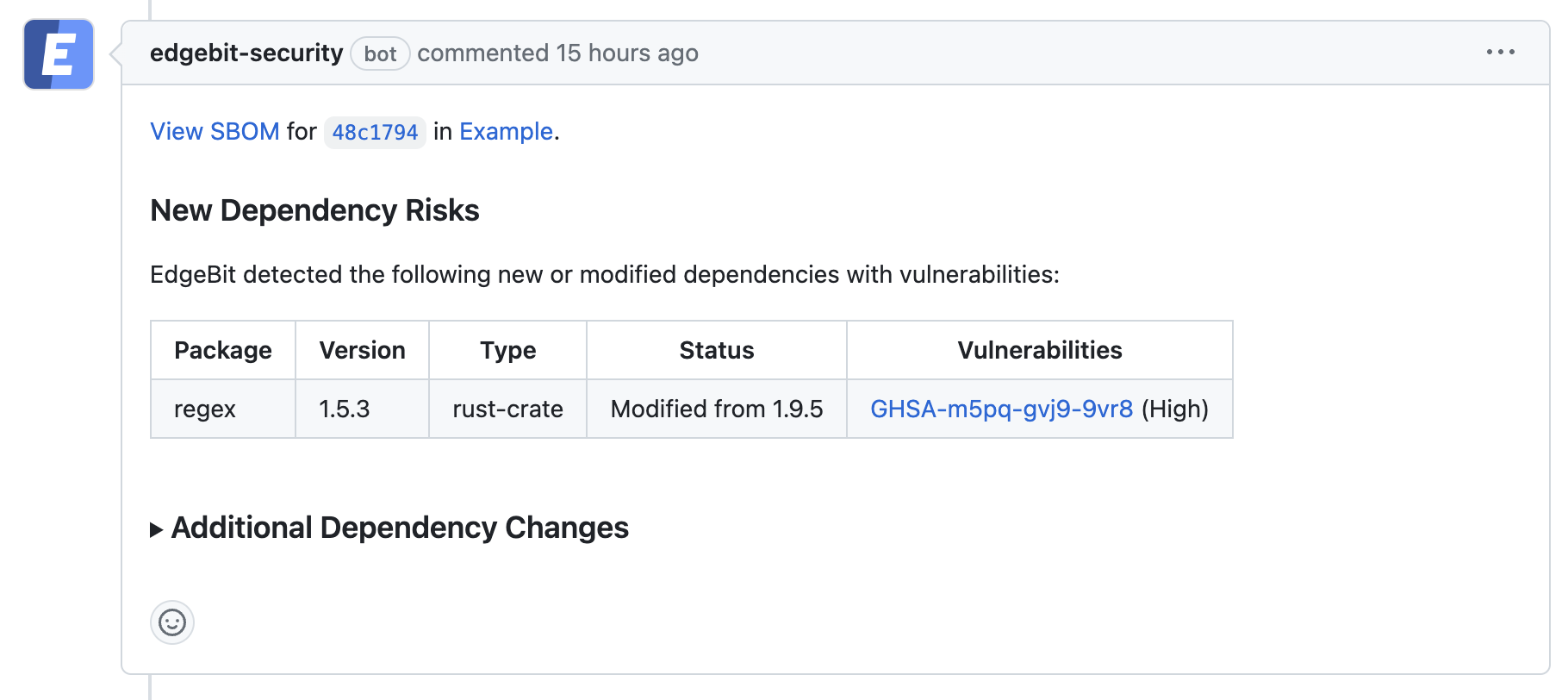
For security teams, the EdgeBit app is easy to enable for all of your repos, and is even able to open Pull Requests against your repos to add or modify your GitHub Actions workflows.
Enhanced Jira integration
EdgeBit’s enhanced Jira integration is an OAuth-based workflow for creating new Jira Issues for new security issues discovered in your apps.
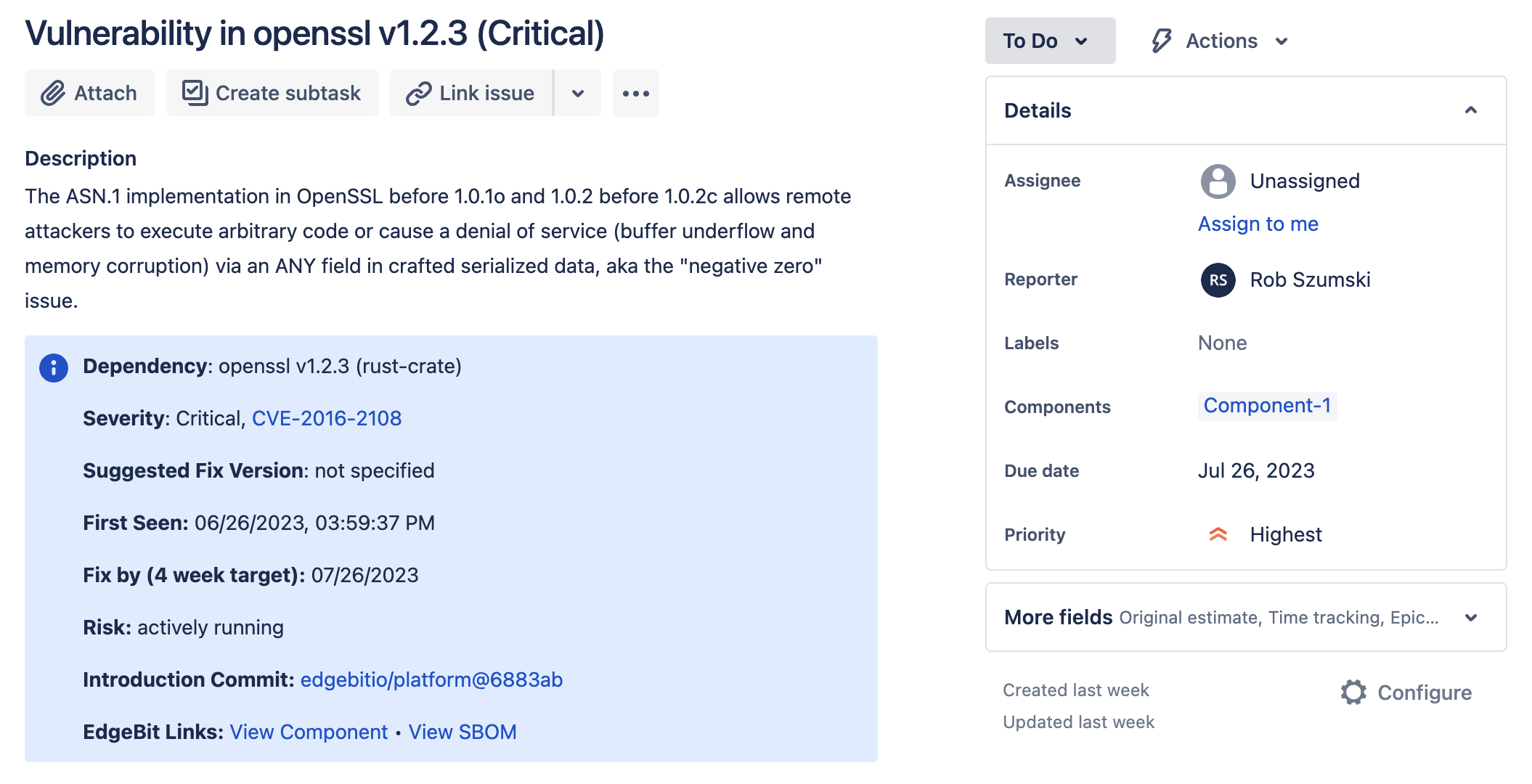
All of the information needed to remediate the vulnerability is included in the issue, including SLA tracking, EdgeBit’s real-time context and links for further details.
Jira Components are tagged automatically from your EdgeBit Components, so the right folks get alerted and you can track remediation all the way to a future sprint.
Try It Out
All EdgeBit customers and trial accounts (sign up) have access to SLA tracking, the GitHub integration and VEX reports.
We are testing out the enhanced Jira workflow on a per-customer basis. Get in touch to try it out!
