Akul Gupta is a Computer Science student at The University of Illinois Urbana-Champaign and joined EdgeBit for a software engineering internship. EdgeBit interns exercise engineering skills and software design on real world problems in EdgeBit’s software supply chain security platform. Akul breaks down a few of his projects in this post.
At EdgeBit, we’re always striving to push the boundaries of what’s possible in the realm of cybersecurity. Our latest achievement? Enhancing EdgeBit Components to track base operating system (OS) vulnerabilities like never before. If you’ve been following EdgeBit, you might remember a previous blog post on using Components to enrich application Software Bill of Materials (SBOMs). That release was focused on application workloads. Today, we’re extending coverage to the base OS as well.
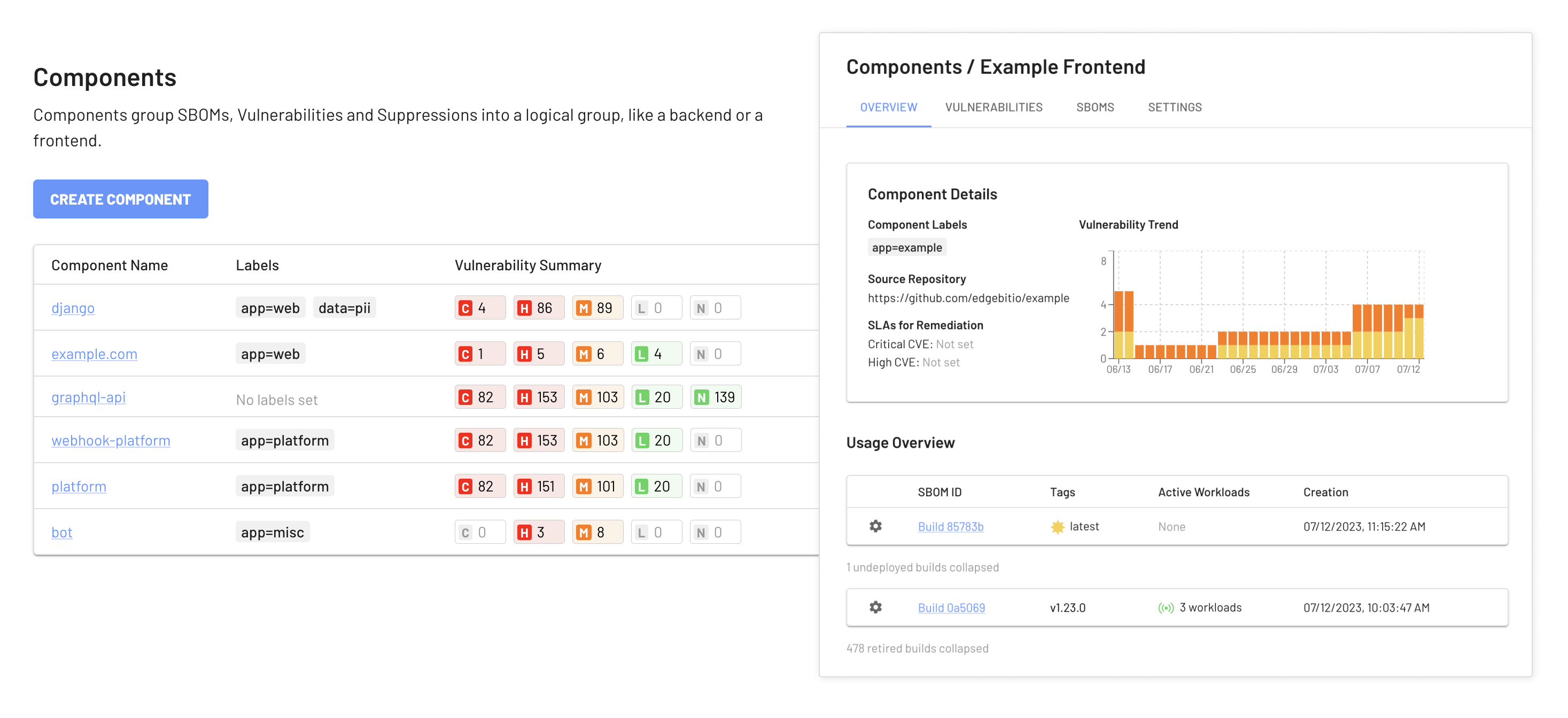
Enriching SBOMs with Components for Base OS Vulnerability Discovery
We’ve taken the concept of Components and supercharged it to serve a vital purpose: identifying vulnerabilities in the very foundation of your systems - the base OS. The EdgeBit agent, has always created a real-time machine SBOM and used the EdgeBit platform to enrich it with vulnerability details.
Here’s where it gets exciting. Our EdgeBit agent not only automatically discovers all the software running in your infrastructure, but it also maps this software to corresponding Components and SBOMs. This means that at a glance, you can easily discern the versions of software currently deployed and explore their third-party dependencies - all within the Components framework.
Now, we’ve taken it a step further. Our updated Components feature can enrich these SBOMs to prioritize, deduplicate and track SLAs for all vulnerabilities spotted across your server fleet. Just picture it: a seamless integration that not only visualizes your software landscape but also pinpoints vulnerabilities within it.
Configuring this functionality is straightforward. We’ve introduced label query based mappings to automatically assign EdgeBit-generated SBOMs to the desired components. Now, you’re not just detecting vulnerabilities on a per-machine basis; you’re prioritizing CVEs for the engineering teams responsible for a group of machines.
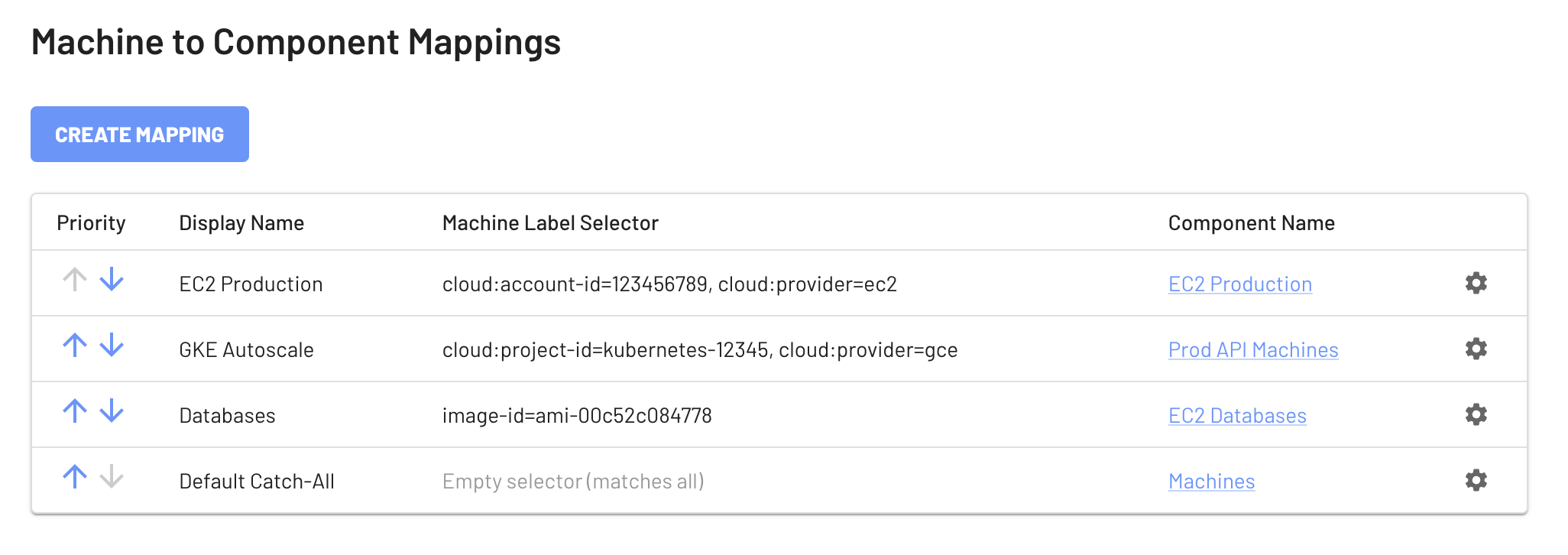
Let’s paint a clearer picture with an example. Say you’re managing a fleet of app servers, and you’re particularly concerned about all machines in your production cloud account. With EdgeBit’s enhanced Components, you can set up a policy that focuses solely on vulnerabilities associated with those machines with a query like cloud:account-id=123456789, cloud:provider=ec2 and easily view them under a single component.
As the EdgeBit agent generates SBOMs, these policies will be applied, and you’ll be able to see if any of your machines are at risk. The system also excels at autoscaling, with numerous customers successfully scaling 100+ machines on a timed schedule. Don’t worry if you’re not the most tech-savvy person in the room. We’ve designed the user interface to be intuitive and user-friendly.
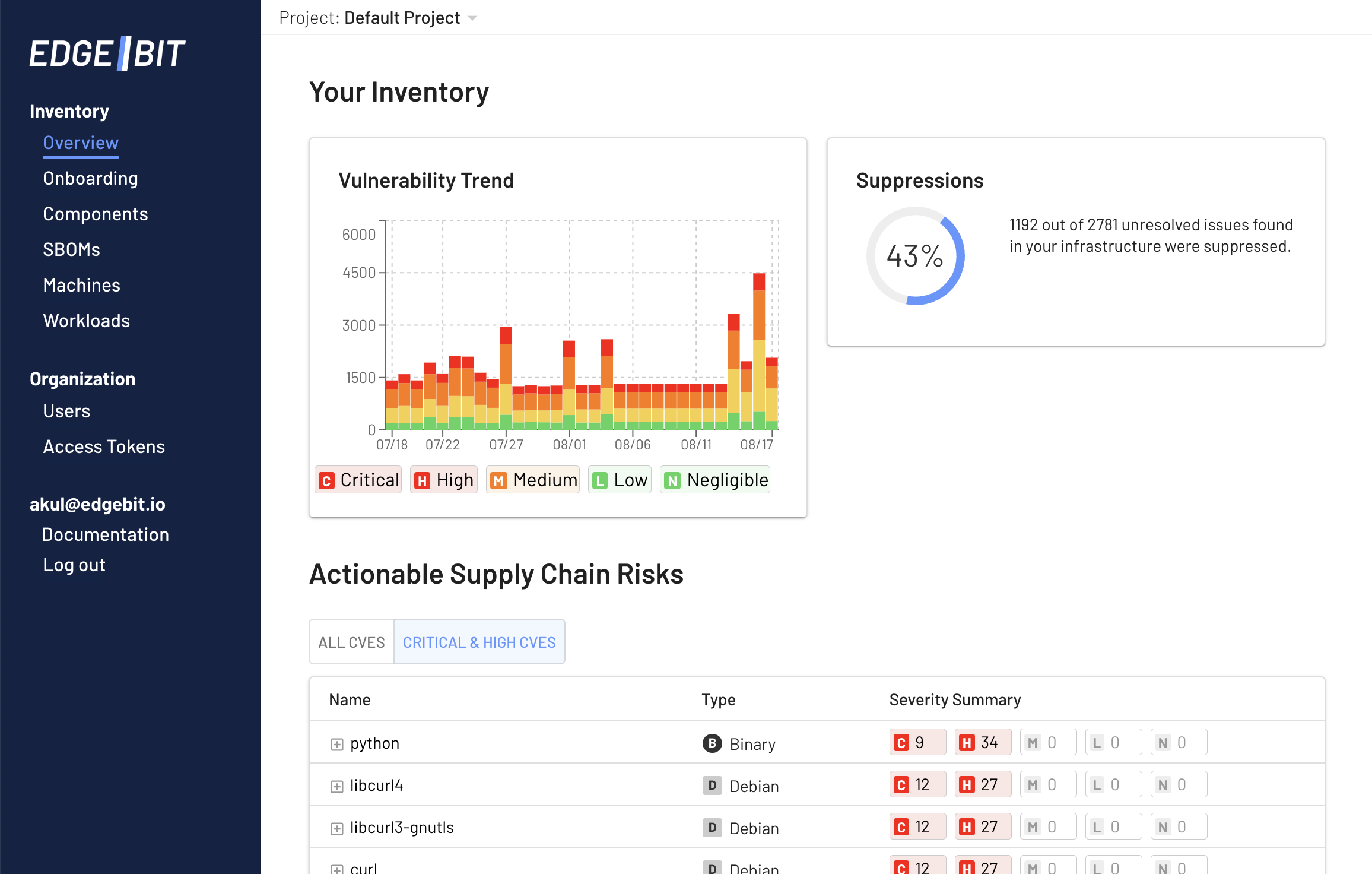
A Glimpse into the Overview Page
We understand the importance of having a comprehensive view of your security landscape. That’s why we’ve also revamped the Overview page. Now, you can access a centralized dashboard that displays all the identified vulnerabilities in one place with CVE details, component breakdown, organized identification of the most vulnerable packages, and a comprehensive trend analysis. No more jumping between screens or trying to sift through SBOMs - everything you need for a holistic overview is right there quickly and efficiently.
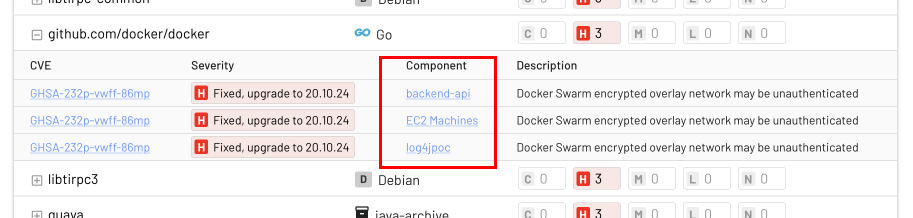
This view represents a prioritized list of items across all your app workloads and machines, which is great for security teams to track high level progress. Below, you can see that the docker Go library was found vulnerable in both two app workloads and a group of EC2 machines.
What’s Next?
As exciting as this update is, it’s just the tip of the iceberg. At EdgeBit, we are committed to constantly evolving and enhancing our features to provide you with the best cybersecurity solutions. We’re already working on building even more functionality into Components, so stay tuned for what’s to come!
If you’re as passionate about staying ahead in the cybersecurity game as we are, make sure to follow us on LinkedIn. It’s where we share insights, updates, and announcements about all the exciting developments happening at EdgeBit.
