An enclave guarantees that sensitive data can never leave the enclave unless specifically allowed. Data inserted, processed or decrypted can never be read by an attacker.
This protection starts in the hardware with isolated RAM, dedicated CPU cores, reduced default networking and Trusted Platform Modules (TPM), all powered by AWS Nitro Enclaves.
EdgeBit adds additional network policy that is embedded into the enclave image by the author, so it can't be relaxed or removed.
An enclave fulfills the exact definition of privacy: being free from observation or disruption by others. Even a hostile parent machine can't introspect the enclave or modify its operating parameters.
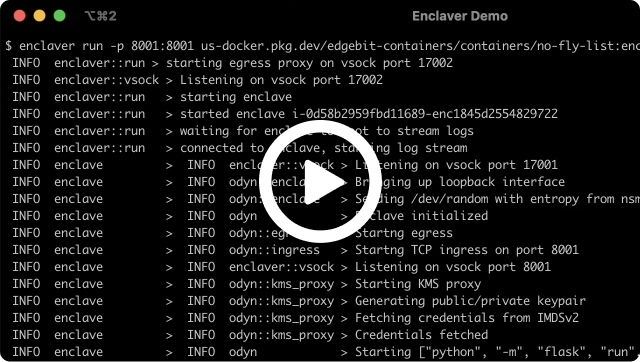
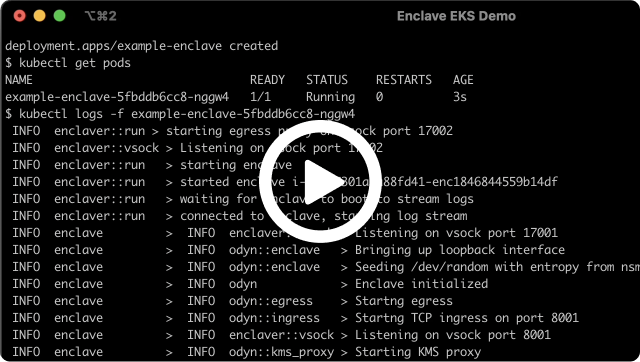
Enclaves are the perfect environment to decrypt and process sensitive data of any sort. This can be long-lived like a complete microservice or short per-request workflows.
Encryption key access policies can be tied to the enclave's attestation which guarantees that only trusted code can fetch the key.
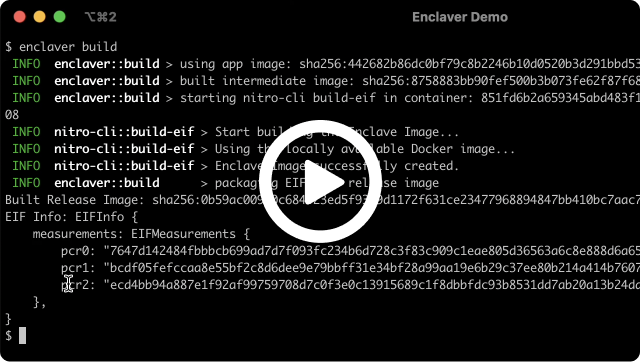
An attestation is a reproducable "measurement" of a piece of code that can be used to give the code a unique identity. An attestation can be generated at build time and trusted at runtime by infrastructure teams.
Tying credentials or access policies (for encryption keys) to an attestation is extremely powerful because the attestation can't be spoofed or stolen like human credentials or hardcoded secrets.
Read more about Enclaver attestations.