Sharing your internal vulnerability management knowledge with your customers establishes trust and removes security noise from their use of your container images.
A Vulnerability Exploitability eXchange (VEX) document is the mechanism used to tell a security scanner to not alert on specific issues that don’t affect your product. A report can also confirm that an issue affects your software.
Customers will scan your containers
Many SaaS platforms have downloadable components that customers run themselves, such as connectors, agents or migration tools. It’s logical for a customer to scan a container image you distribute before running it in their environment.
It’s not ideal for them to see a slew of security issues. It’s doubly bad if these issues are ones that your team has already triaged and ignored because they don’t affect your software.
Creating a VEX document about a container image
EdgeBit supports the OpenVEX standard for VEX reports. These can be created manually with vexctl or automatically by platforms like EdgeBit.
Manually creating a VEX report about an OCI artifact
The subject, or product of the VEX report should be the SHA256 of the OCI repo digest, in a very specific format:
pkg:oci/alpine@sha256:c5b1261d6d3e43071626931fc004f70149baeba2c8ec672bd4f27761f8e1ad6bThis can be passed to vexctl along with other data:
vexctl create --product="pkg:oci/alpine@sha256:c5b1261d6..." \
--vuln="CVE-2024-2511" \
--status="not_affected" \
--justification="inline_mitigations_already_exist"
This document is now ready to be distributed to your customers and passed into scanners such as Grype or Trivy. Here’s what two supressed issues look like in Grype. Note that if you didn’t pass --show-suppressed you wouldn’t see these at all.
$ grype alpine:latest --vex alpine.vex.json --show-suppressed
✔ Vulnerability DB [no update available]
✔ Loaded image alpine:latest
✔ Parsed image sha256:ace17d5d883e9ea5a21138d060...
✔ Cataloged packages [16 packages]
✔ Scanned for vulnerabilities [12 vulnerability matches]
├── by severity: 0 critical, 0 high, 12 medium, 0 low, 0 negligible (2 unknown)
└── by status: 2 fixed, 12 not-fixed, 2 ignored
NAME INSTALLED FIXED-IN TYPE VULNERABILITY SEVERITY
busybox 1.36.1-r15 apk CVE-2023-42366 Medium
busybox 1.36.1-r15 apk CVE-2023-42365 Medium
busybox 1.36.1-r15 apk CVE-2023-42364 Medium
busybox 1.36.1-r15 apk CVE-2023-42363 Medium
busybox-binsh 1.36.1-r15 apk CVE-2023-42366 Medium
busybox-binsh 1.36.1-r15 apk CVE-2023-42365 Medium
busybox-binsh 1.36.1-r15 apk CVE-2023-42364 Medium
busybox-binsh 1.36.1-r15 apk CVE-2023-42363 Medium
libcrypto3 3.1.4-r5 3.1.4-r6 apk CVE-2024-2511 Unknown (suppressed by VEX)
libssl3 3.1.4-r5 3.1.4-r6 apk CVE-2024-2511 Unknown (suppressed by VEX)
ssl_client 1.36.1-r15 apk CVE-2023-42366 Medium
ssl_client 1.36.1-r15 apk CVE-2023-42365 Medium
ssl_client 1.36.1-r15 apk CVE-2023-42364 Medium
ssl_client 1.36.1-r15 apk CVE-2023-42363 MediumEdgeBit’s automatically generated VEX reports
EdgeBit generates up-to-the-millisecond accurate VEX reports based on your security team’s triage, the real-time context from how your app is running on your server fleet and the current database of known vulnerabilities.
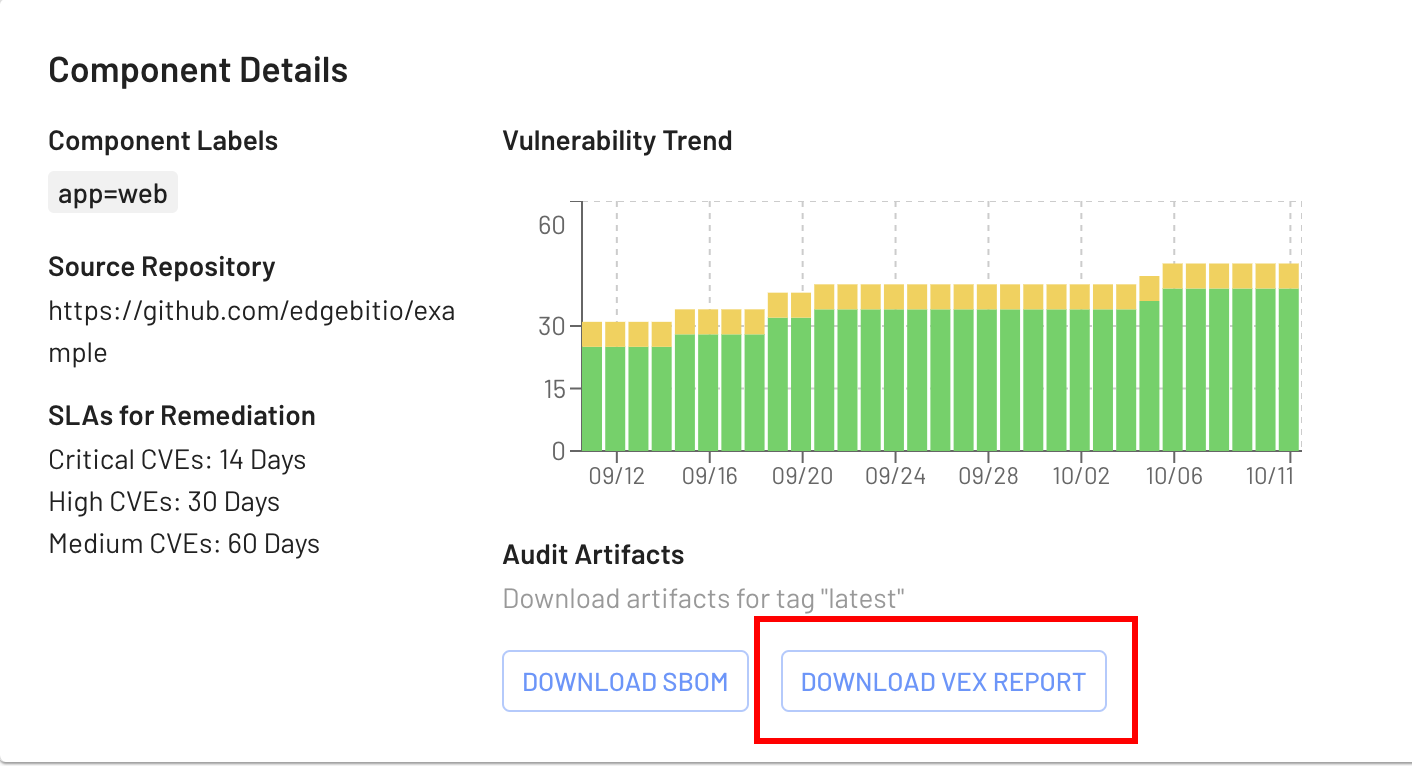
When a security issue in your software is first found, supressed or remediated, the VEX document is regenerated. For open issues, the statement communicates whether the issue is found to affect or not affect your app based on how it’s observed while running.
For many use-cases, a VEX document is more useful than providing a Vulnerability Disclosure Report (VDR) and contains a superset of the same information. Reach out to the EdgeBit team to discuss your specific circumstances.
