The new CVSS v4 specification is out. CVSS is the Common Vulnerability Scoring System which is commonly used within vulnerability databases like the National Vulnerability Database (NVD) and Open Source Vulnerability Database (OSV). EdgeBit uses both of these databases as inputs to the security platform and we’re excited about CVSS v4.
Why care about any of these specs or their changes?
Incorrect prioritization can leave open a gap that attackers are utilizing. Combining CVSS scores from industry experts with your unique environment and risk posture can allow you to focus on the small number of real threats – before they are exploited.

Brief History of CVSS
The CVSS wikipedia has great detail that I won’t repeat here. CVSS v3, which came out in 2015, is both widely used and universally maligned for how it’s applied to reported vulnerabilities.
v3 expanded additional metadata about each vulnerability, such as network-based exploitability, difficulty executing the attack, the privileges required, etc. The exact parameters that map to a high vs a low attack complexity rating were quite subjective, depending on who rated the vulnerability.
Further clarification of the definitions of the added metrics was published under v3.1 but in many security organizations, the reputation for how useful these metrics can be was tarnished.
What’s new in CVSS v4
The goals for v4 are laid out in the specification document. The summary is that by providing 4 types of metrics, more nuance and a risk-based approach can be taken by each consumer.
CVSS v4 is composed of four metric groups:
- Base: severity according to intrinsic characteristics, designed to be constant over time and assumes the worst case
- Threat: adjusted based on if a POCs exists and reported exploits in the wild. If you’re familiar with EPSS, this is similar in spirit.
- Environmental: modifications based on the specifics of a deployment environment
- Supplemental: representation of additional extrinsic attributes for added context
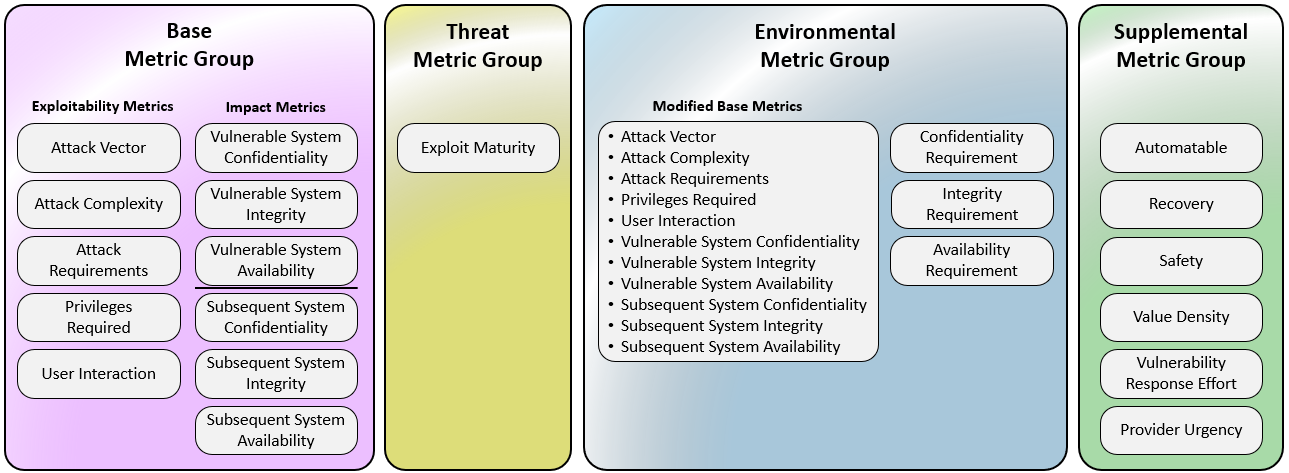
When referring to a score using the first 3 groups, you’re using CVSS-BTE, which is the score using Base + Threat + Environmental categories.
You’ll start seeing these scores used in the NVD and OSV starting in 2024.
Environment is Essential Context
Given the high volume of new vulnerabilities and the complex nature of our software supply chains, vulnerability prioritization can only reasonably done by evaluating the risk factors for your environment and your applications.
EdgeBit already uses environmental factors from your running applications to highlight to suppress issues as they are found in your workloads.
Reacting in milliseconds to changes in real-time, we’re able to detect that 80% of most container content is dormant which can bring the list of security issues down to single digits. This is all based on your app and languages/ecosystems of course — use EdgeBit for free to focus on the vulnerabilities that matter.
