Today I want to discuss a new concept: the real-time software bill of materials (SBOM). A real-time SBOM is an inventory of a live server, with a filter for packages and libraries that are active and running.
EdgeBit is a tool to secure your software supply chain that focuses on code that is actually running. This simplifies vulnerability management as it cuts through noise. The real-time SBOM is the brains behind the noise reduction.
EdgeBit watches in real time — we cross-reference your build pipelines and server fleet with multiple data sources to communicate your live inventory and actual risk.
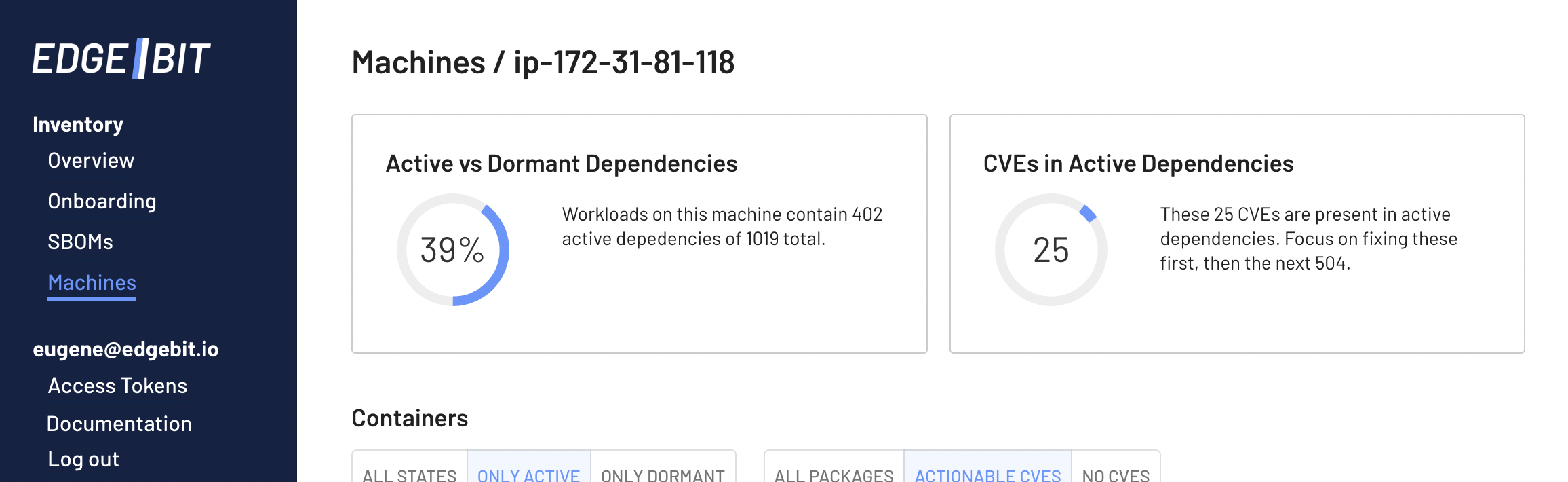
In this example, our Linux machine has 39% of its 1019 packages active, which allows an engineer to focus on 25 vulnerabilities instead of the full set of 504.
Dormant dependencies are a huge source of noise
Nothing is more frustrating than investigating a vulnerability to find that it’s not exploitable at all. EdgeBit Founder and CTO Russell Haering ran security engineering at Okta and knows first hand it’s a constantly moving target of dependencies, frameworks and deployment platforms.
Automation is key, but security teams aren’t experts in each app, so “open a ticket for any vulnerability found” is a typical workflow. These tickets are a firehose – “shift left” is about moving security closer to the engineer, but it’s noisy and frustrating.
Here’s a few stats that show how it really adds up:
- It takes ~51mins to triage, fix and patch a single vulnerability
- A large enterprise is tracking ~1-4M known vulnerabilities
Meet your vulnerability SLAs with ease
EdgeBit ranks threats that need to be fixed to keep the SLA promised to your customers and helps engineers patch the riskiest items first. Almost every compliance framework requires setting SLA thresholds for your organization and they can be challenging to meet.
EdgeBit uses eBPF-based observation of workloads to keep the threat list as short as possible. For example, if your code has a history of exec-ing imagemagick we’ll include it, but if it’s dormant we can lower the priority of those vulnerabilities.
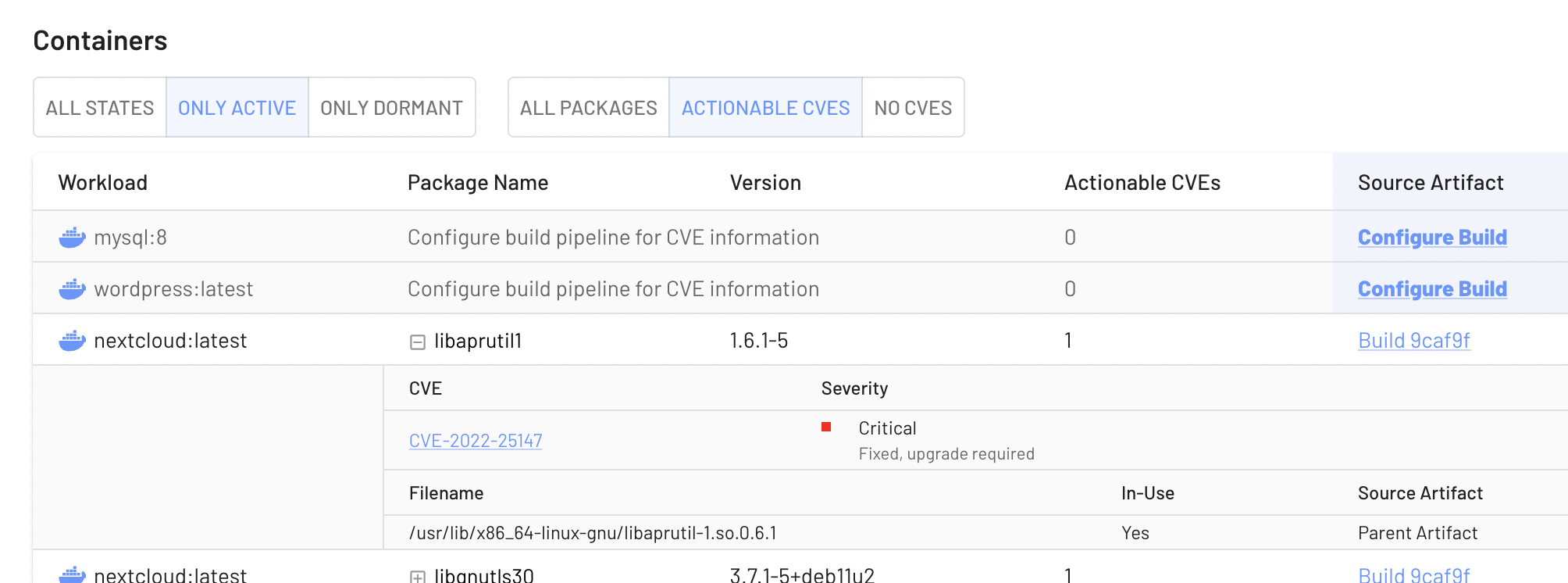
Social cues towards consistency
When adding a new dependency, EdgeBit’s runtime knowledge helps our GitHub bot suggest versions already in use by other teams in your company, as social proof to nudge towards consistency.
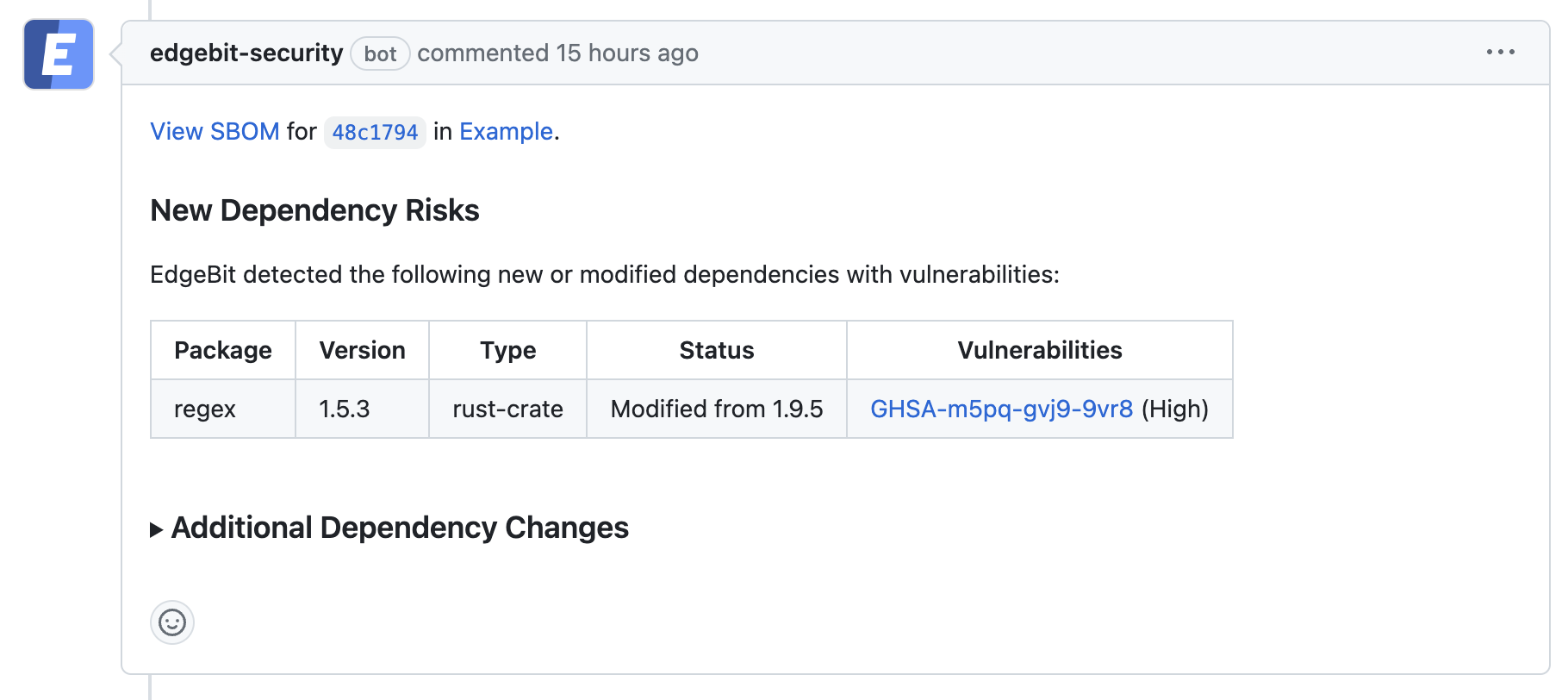
How does EdgeBit work?
To use EdgeBit, each build execution sends a software bill of materials (SBOM) to EdgeBit. We’re big fans of the open source Syft project, which we use to generate SBOMs. After a build is deployed, we use eBPF to identify packages and files in use, and compare it to the SBOM and vulnerability databases.
If there’s a new CVE, EdgeBit passes along context to the engineers tasked to fix it. If a package reports a CVE, but we observe it’s dormant, the CVE doesn’t need to hit the pager…EdgeBit’s focus factor at work.
All of this happens continuously, unlike other runtime SBOMs, which allows EdgeBit’s security platform to detect changes, track SLAs and resolve issues automatically.
Real supply chain attacks are underway
Looking beyond compliance, real attacks are happening via software dependencies. Since the Colonial Pipeline attack, Federal compliance requirements and Biden’s cybersecurity executive order now cover tracking and understanding your supply chain.
For a single library, it’s tricky to securely download, integrate, sign and verify it…and very hard for 100s of dependencies across many apps. A single view across OS packages, standalone binaries and containers is required to understand the full attack surface. Where did the dependency come from? What builds is it in? Where is it deployed?
When developers commit with new dependencies, the inventory is stored in an SBOM, allowing you to meet NIST and other software supply chain security requirements with ease.
Try out EdgeBit
Try it out by building a real-time SBOM from a live server and then trace your workloads to close the loop. I think you’ll be surprised by the ratio of active to dormant dependencies - we’re seeing about 20-40% are actually active.
We love showing it off in demos – please reach out. Here’s a quick 1 minute teaser:
What’s next for EdgeBit
There is a lot on the nearterm roadmap: tighter integration with sigstore, pulling SBOMs out of containers automatically, and a smarter Kubernetes admission controller. Today we track file accesses and correlate it to package managers like Deb, RPM, PyPi. Soon we’ll add more language specific hooks to better support compiled languages.
Further out, we will also allow you to block execution of dormant dependencies and enforce file integrity to ensure the bits that are executing match the SBOM. And we’re also exploring how an app can communicate its trust profile to other apps, like a secret store.
