In November 2023, the New York Department of Financial Services published the second amendment to its cybersecurity requirements for institutions based in New York. Included are stricter standards for vulnerability management and application security for both internally and externally developed apps.
Vulnerability Management
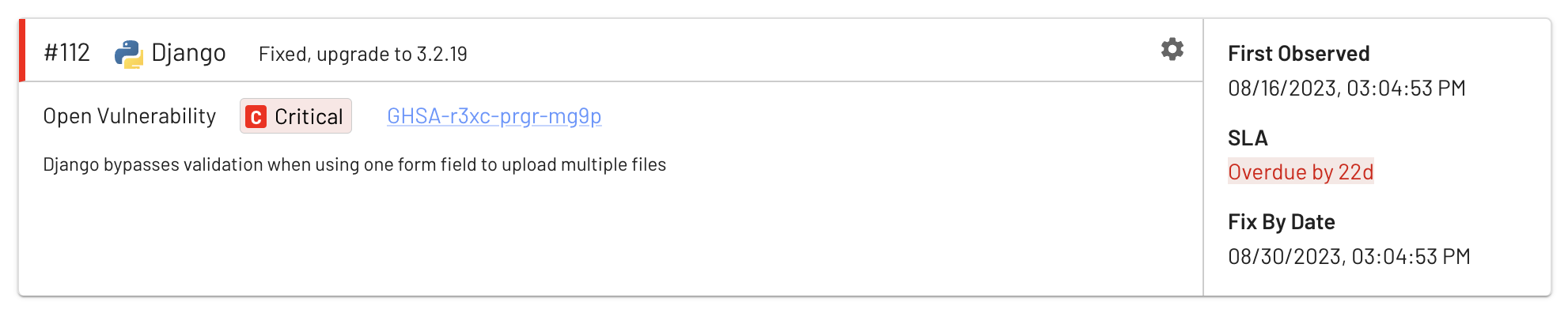
NYDFS 500.5 contains changes strengthening vulnerability management practices, with an emphasis on dialing up the urgency based on risk and material system changes.
Real-time knowledge of your app infrastructure is the only way to manage the constant flux of app changes that affect your risk:
- What versions of each app apps are currently running
- Which libraries and dependencies are actually in use?
- What known vulnerabilities do they contain?
- Are issues overdue based on the remediation SLA?
Material system changes are also easily detected:
- What vulnerabilities are about to be fixed in this deployment?
- What new vulnerabilities will be introduced with this deployment?
Here’s the full text of the relevant requirements:
(a) conduct, at a minimum: … (2) automated scans of information systems, and a manual review of systems not covered by such scans, for the purpose of discovering, analyzing and reporting vulnerabilities at a frequency determined by the risk assessment, and promptly after any material system changes;
(b) are promptly informed of new security vulnerabilities by having a monitoring process in place; and (c) timely remediate vulnerabilities, giving priority to vulnerabilities based on the risk they pose to the covered entity.
Risk is not a static score of course — it’s constantly changing as different parts of your app are exercised. EdgeBit watches in real time to detect which libraries and dependencies are in-use or dormant and can adjust risk factors for vulnerabilities accordingly. Communicating context about the production environment reduces noise and allows your engineers to fix the actual risks.
Application Security
NYDFS 500.8 covers application security for both external and internal apps. These requirements are straightforward but an SBOM-based security platform brings a standard set of tools to address both types of apps.
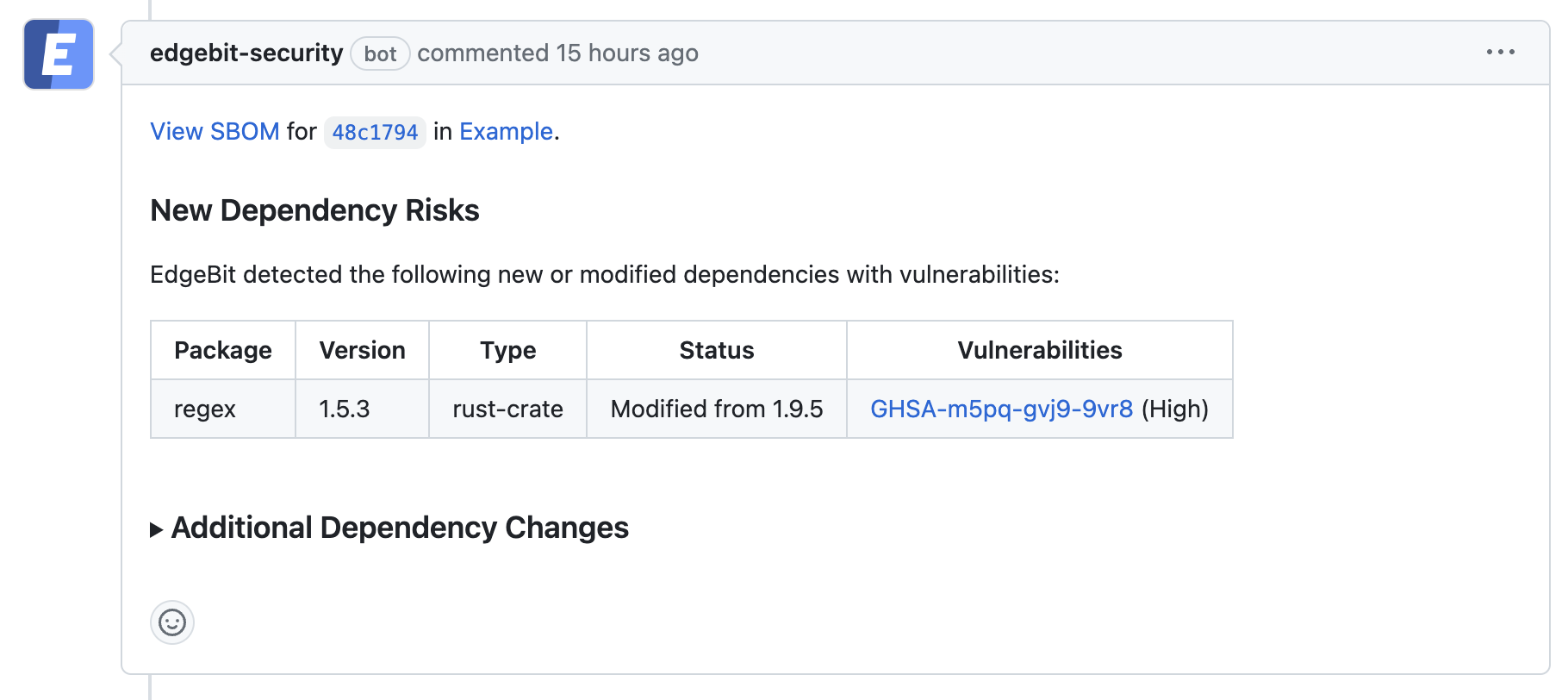
By building SBOMs and assessing internal app changes during development and at the pull request, security issues can be caught before code is merged. For issues discovered later, the chain of custody is well established by tying the SBOM to the commit to understand exactly when and where the risk was introduced. By matching running workloads via the SBOM, you also gain immediate insight into where the risky code is deployed in real time.
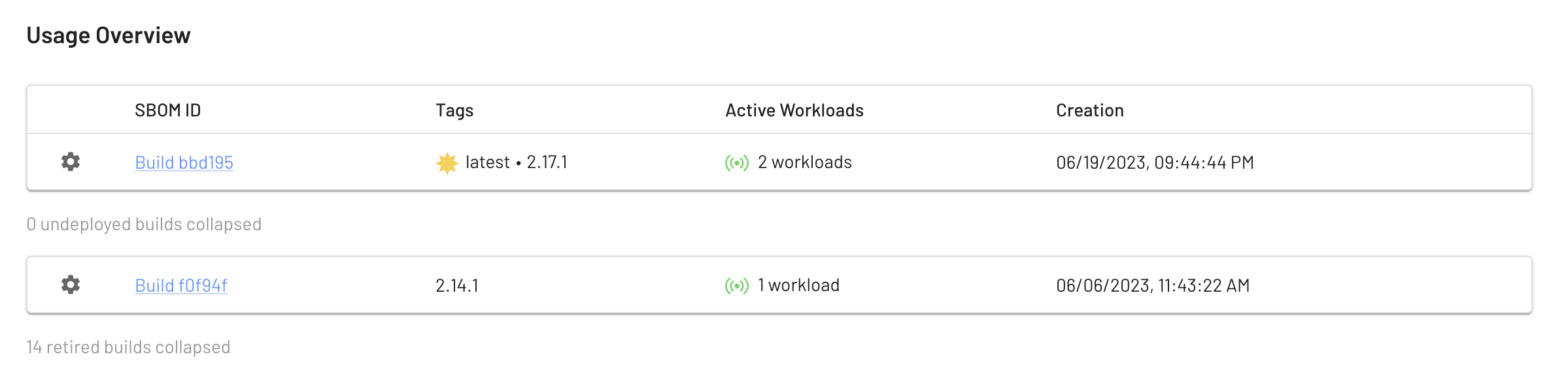
For external apps, you’re not involved in their development, but you can still catch vulnerabilities with the same process. Consume an SBOM from the vendor or generate one from the delivered app artifacts to start the chain of custody and understand your risk before starting a deployment.
Here’s the relevant text of NYDFS 500.8:
(a) Each covered entity’s cybersecurity program shall include written procedures, guidelines and standards designed to ensure the use of secure development practices for in-house developed applications utilized by the covered entity, and procedures for evaluating, assessing or testing the security of externally developed applications utilized by the covered entity within the context of the covered entity’s technology environment.
Other Notable Changes
The second amendment has a new requirement around privileged access management, following the theme of speeding up reaction to change in risk and user need, just like their vulnerability management changes.
Similar to recent SEC rules for cybersecurity disclosure to the public, NYDFS requires the CISO to issue a “timely report” about material cybersecurity issues (e.g., significant cybersecurity events and significant cybersecurity program changes).
Read the full text of the second amendment to the NYDFS cybersecurity requirements.
Cybersecurity and Software Supply Chain Regulations
Jump over to our regulations page to read about the national cyber security strategy and how it’s impacting NIST, FDA, PCI, SEC and other organizations in the US, Europe and Australia.
