Many of the popular SBOM formats are JSON-based, but merging two SBOMs together with standard JSON tools does not work well. For example, any other jq examples you may find on the web do not work with SBOMs.
To save you a bit of researching, below is an extremely simple Bash script that combines two SBOMs and returns the output so it can be piped into another file.
Platforms like EdgeBit can help you manage SBOMs, but sometimes you need a simple tool for quick investigation.
#!/bin/bash
#
# Merges two json files together
#
# Usage:
# merge-sbom.sh file1.syft file2.syft > merged-file.syft
#
jq -s 'def deepmerge(a;b):
reduce b[] as $item (a;
reduce ($item | keys_unsorted[]) as $key (.;
$item[$key] as $val | ($val | type) as $type | .[$key] = if ($type == "object") then
deepmerge({}; [if .[$key] == null then {} else .[$key] end, $val])
elif ($type == "array") then
(.[$key] + $val | unique)
else
$val
end)
);
deepmerge({}; .)' $1 $2Execute it like this and your combined SBOM is available at merged-file.syft:
$ merge-sbom.sh file1.syft file2.syft > merged-file.syftThis assumes that both files are the same format and this script has been tested with two Syft SBOMs.
Combining and Aggregating SBOMs
Use-cases for combining SBOMs together:
| Use-Case | Description |
|---|---|
| Combine Front-end & Back-end | A single SBOM to represent your entire application |
| Aggregate Microservices | Organize a set of services for vulnerability management |
| Combine Source Directory and Container SBOMs | Collect dependencies inside and outside of your container builds |
The combined and aggregated SBOMs can fulfill supply chain security regulations for SOC2/ISO 27001 compliance or as part of your FDA certification of a class 2 or 3 software medical device.
Automate a Stream of SBOMs
EdgeBit can automate a constant stream of SBOMs from your build pipelines into action items directly in a pull request for engineers and give security teams a holistic overview of all of your software components.
EdgeBit Bot in Pull Request
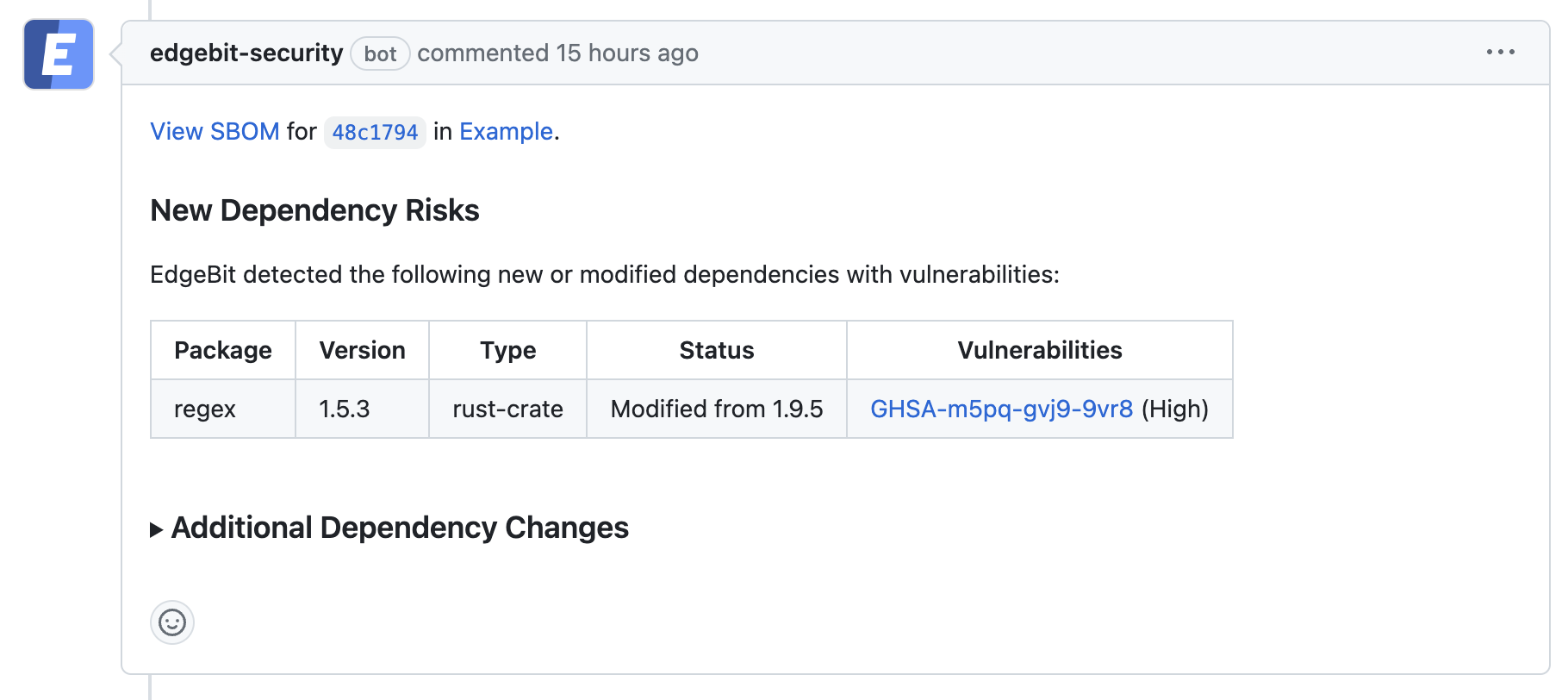
Tracking Inventory, History and Vulnerabilities
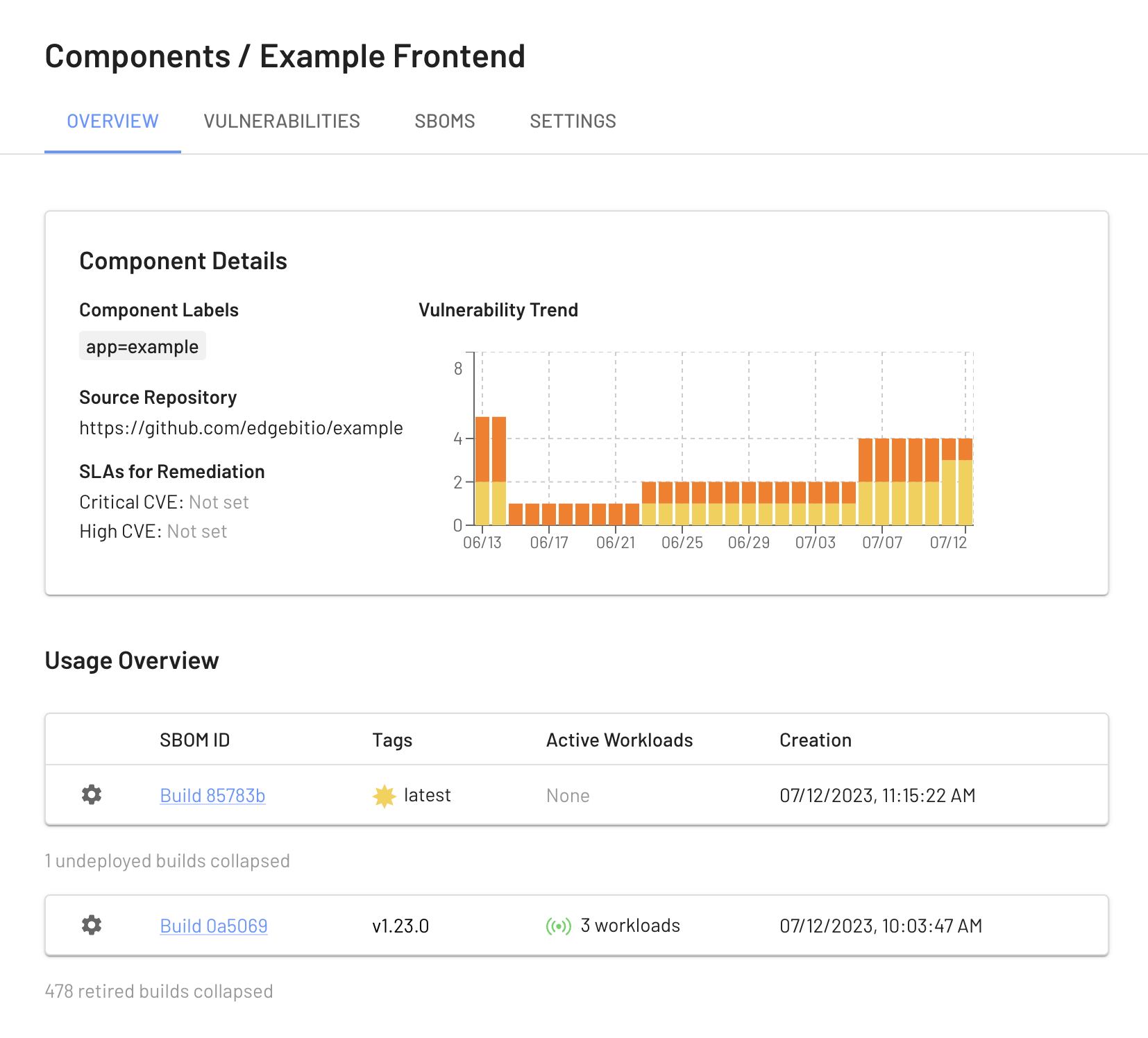
Jump over to the EdgeBit platform docs for more examples of supply chain security automation.
