Today we are excited to introduce a set of features that allow software engineers to view an enriched history – a stream of SBOMs – for each component of their stack.
Companies that fall under FDA, NIST, or PCI v3 regulations, or sell to the Federal government must comply with software supply chain regulations. The meat of these regulations is to provide software bills of materials (SBOMs) and vulnerability disclosure reports (VDRs) as part of your software sales process or medical device certification.
Meeting your compliance goals requires producing SBOMs for each functional piece of your software, like a frontend, backend, or microservice. The process quickly gets complex when each component has its own technology stack and build pipeline. Organizing and automating the enrichment of your SBOMs requires specialized tools.
Introducing the “Component”
Traditionally, SBOMs have been a static, point-in-time object but that’s not helpful for software that’s constantly being authored and vulnerabilities that are constantly being discovered.
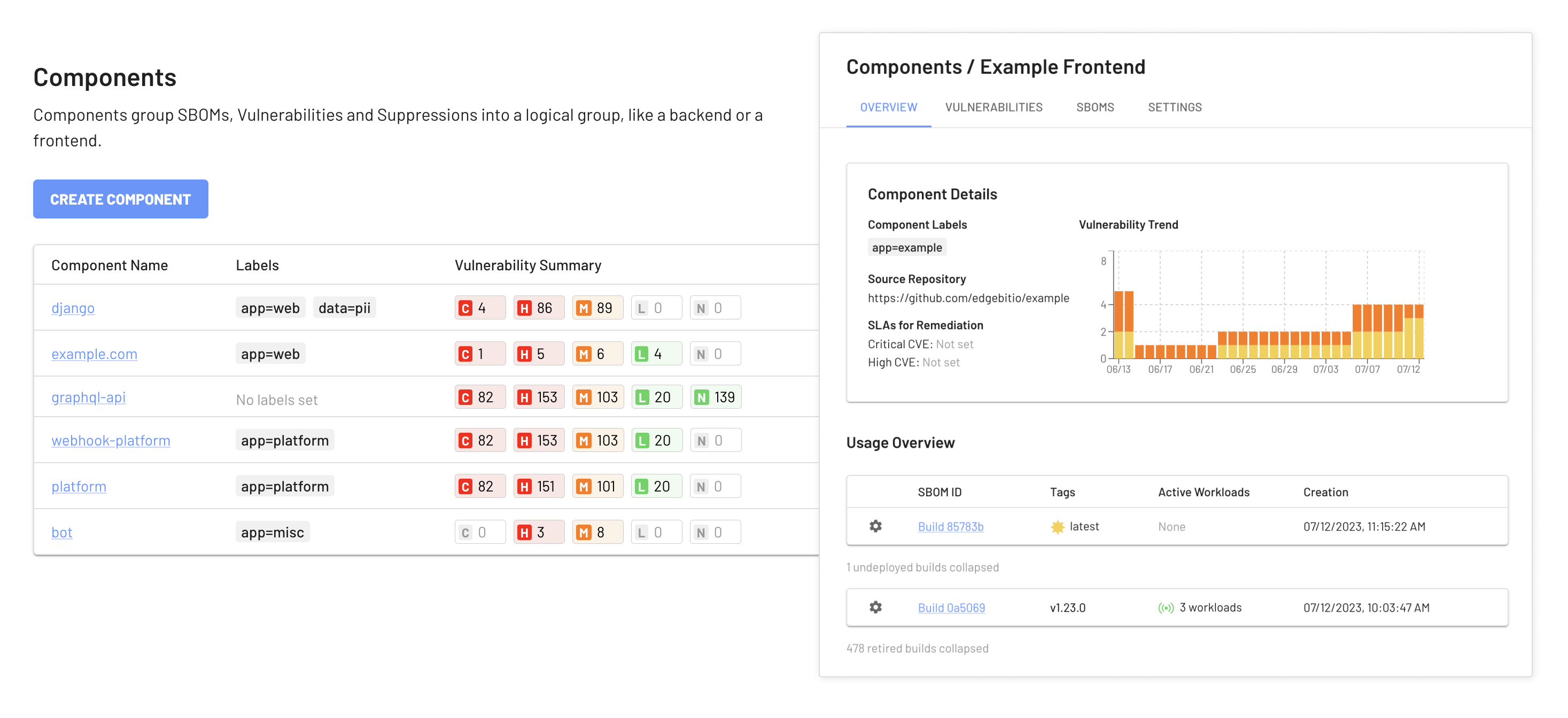
EdgeBit Components collect and visualize the activity for a stream of SBOMs. EdgeBit automatically discovers all of the software running in your infrastructure and maps it to the corresponding Components and SBOMs, making it easy to tell at a glance what versions of your software are currently deployed, and to explore their third party dependencies.
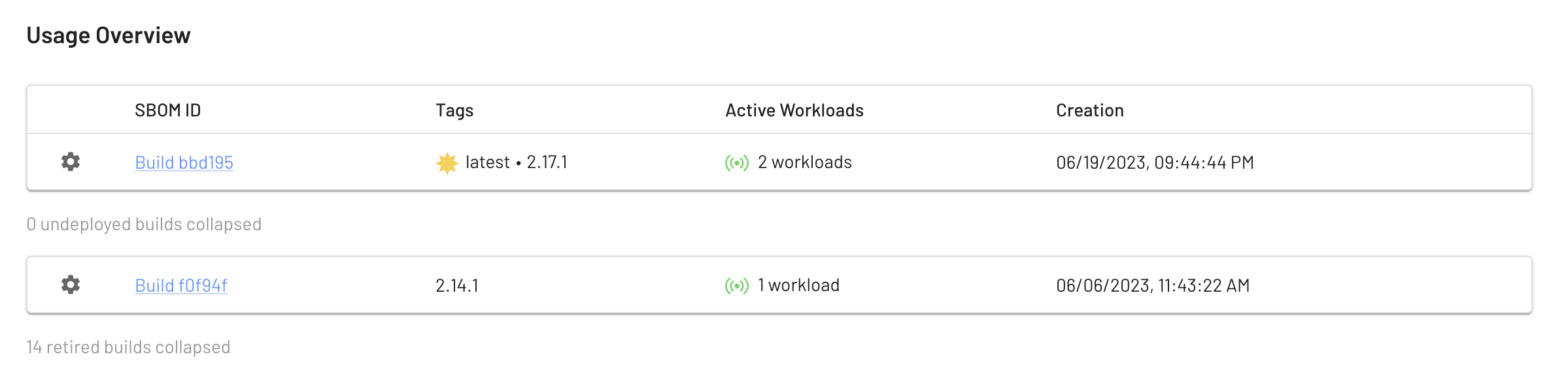
These versions can have tags that float from version to version, just like container tags. In the screenshot above we are using the latest tag to track builds from our main branch; we can see that the current latest version is also tagged 2.17.1 and it is actively running on two workloads. An older 2.24.1 is deployed once and there are no undeployed builds in between.
Painless Tracking, Triage and Suppression of Security Issues
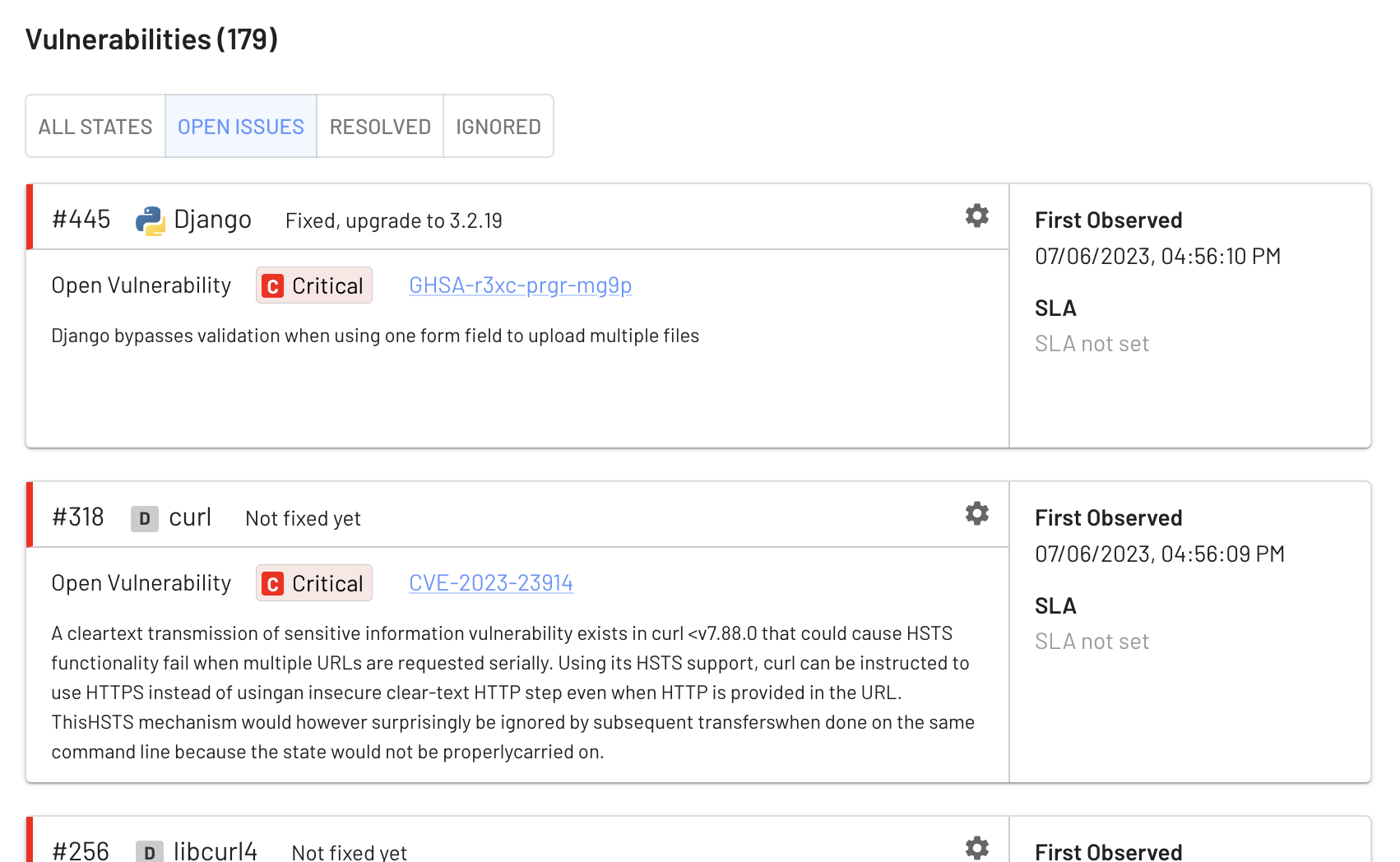
Components enrich each package and library in your software to discover known vulnerabilities and start tracking when issues were first observed. EdgeBit combines a real-time inventory of your infrastructure with the stream of incoming SBOMs and external enrichment data to help you better prioritize important vulnerabilities while suppressing false positives.

When EdgeBit discovers a vulnerability it will suggest upgrade actions like “upgrade to v1.2.5” and provide a description of the issue for more research. If the issue is no longer spotted in a newer SBOM, it is automatically closed.
EdgeBit reduces the severity of vulnerabilities in dormant dependencies based on a customer-configurable policy, to allow for the most urgent issues to be prioritized first. You can choose to drop one or two levels down, or to assign all issues related to dormant dependencies to a certain severity level. You can also choose to automatically ignore vulnerabilities in dormant dependencies.
Each component can also be configured to ignore issues below a certain severity.
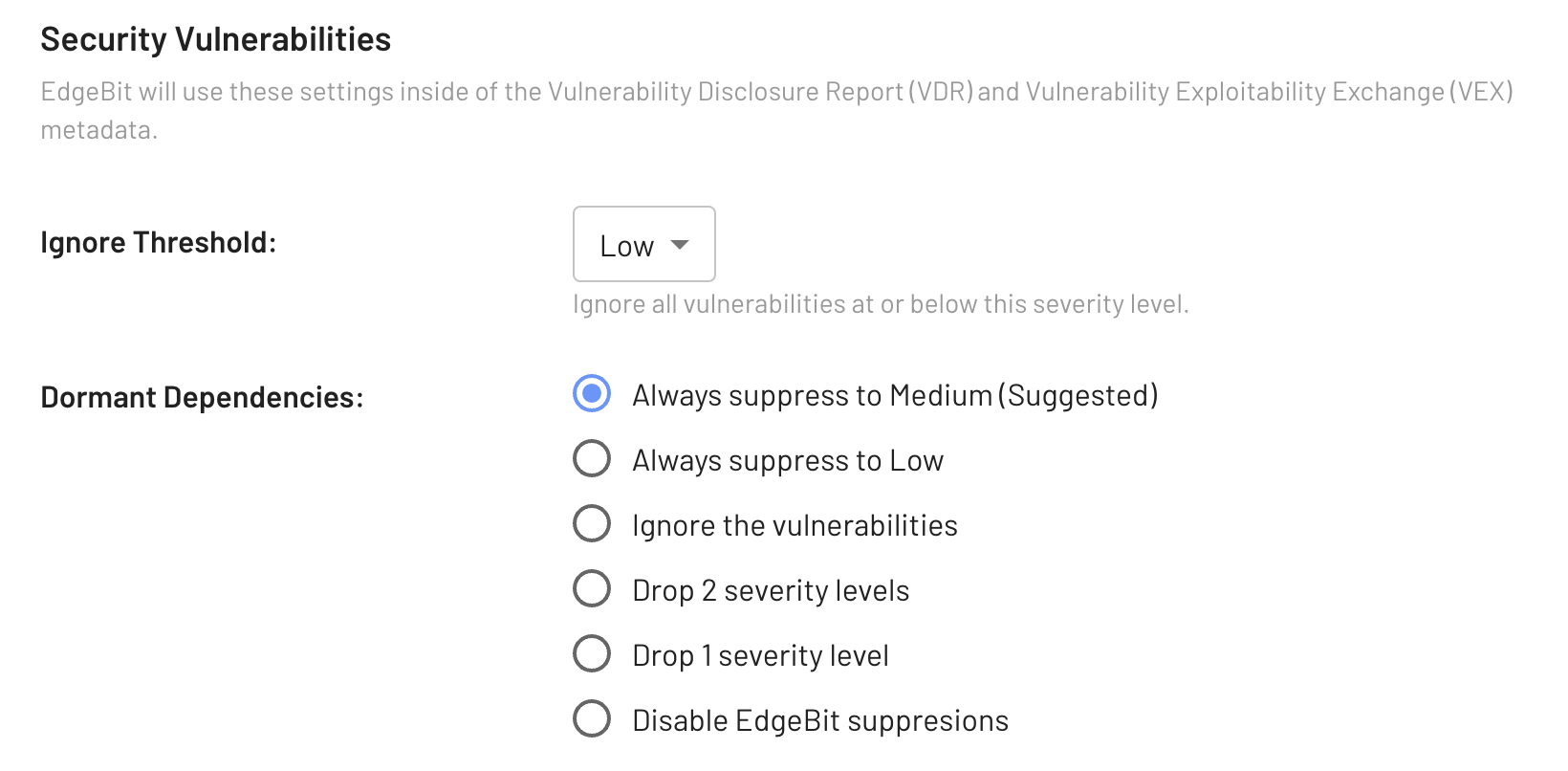
By default, we suggest a threshold of “Ignore all Negligible” and drop issues related to dormant dependences to Medium.
All of this exists to reduce the amount of issues that alert you for investigation, while tracking the full list for awareness and compliance.
Alerts, Feedback, Insights for Engineers
The new Component level reporting is available to all, but engineers get all of the context needed to solve issues right in their Pull Request, at the time they upgrade or downgrade a dependency.
Here’s an example of a downgrade that would introduce a new vulnerability:
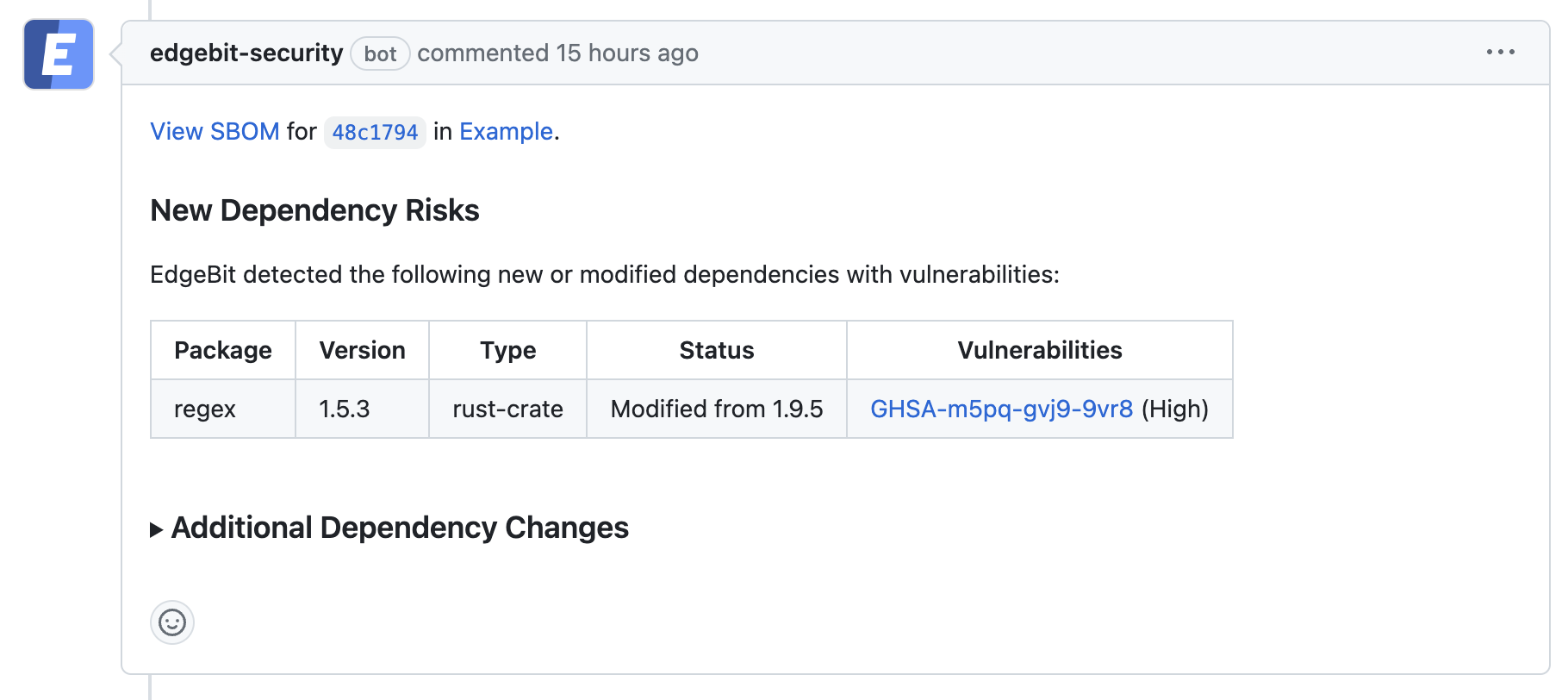
The component is linked for a deeper dive if required.
Shifting Liability for Insecure Software
The importance of understanding your software components and their potential vulnerabilities becomes even more apparent in light of recent developments in cybersecurity legislation. Just this week, the Biden administration has published more details about the implementation plan for the nation’s cybersecurity strategy, and it includes two critical points that affect software companies:
1. Software Bill of Materials: Increasing software transparency allows market actors to better understand their supply chain risk
Using, consuming and publishing SBOMs are a core pillar to the strategy.
2. Allows market actors to hold their vendors accountable for secure development practices
Yes, you are reading that correctly - there is a shift in liability for software companies that don’t follow these best practices. A safe harbor provision is available for organizations that follow best practices but still have an incident. Organizations not following the CISA and NIST guidelines are ineligible.
Read more about the downstream software supply chain regulations from various government agencies and industry groups.
Back to Work
We’re hard at work adding more functionality to Components and other highly-requested features. Stay tuned for more, and if there’s something you’d like to see us add don’t hesitate to reach out! In the meantime, see the Components documentation for details on how to get started!
