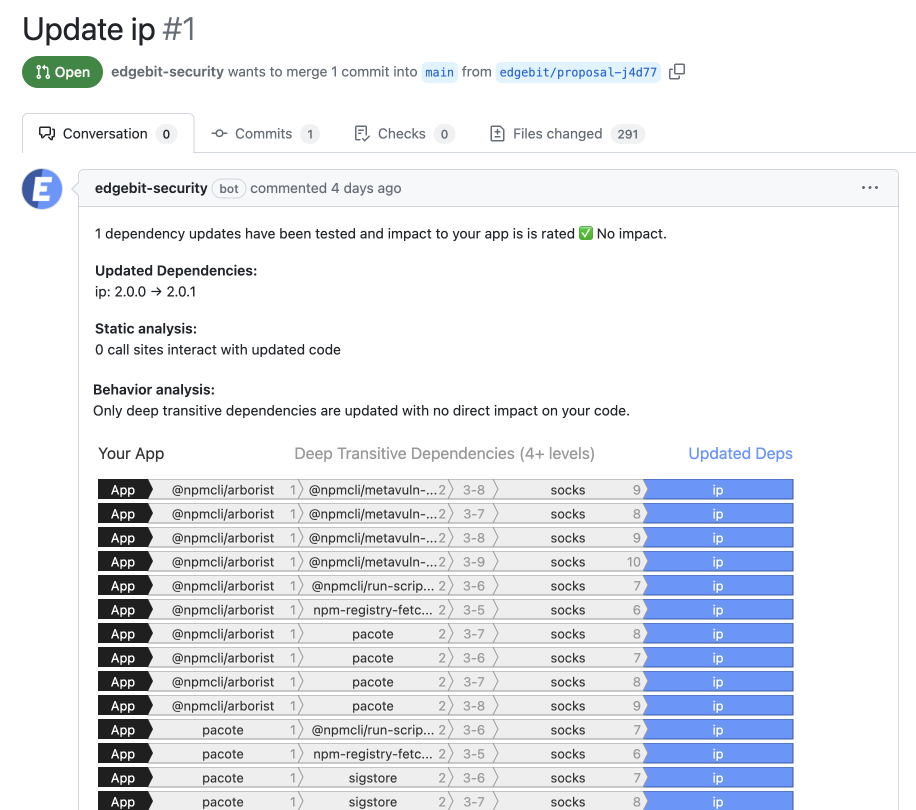
All enterprises use source code scanning to find programming mistakes and flag packages with security issues. The result of a scan creates tickets or alerts that app teams must triage. Sprawling supply chains ensure that nobody has time to fix them all. You’re forced to prioritize — either manually with a meeting or using your scanning tools to help.
Fine-grained reachability is possible by tracking usage at the function level. This should be way less noisy! But there’s a huge downside: most vulnerabilities don’t include function-level metadata. Highly dynamic languages can also complicate function tracking.
Reachability for Prioritization Isn’t Viable Long Term
With perfect function-level metadata, you’re still left with a decision: update dependencies now or defer until later?
Even cutting-edge reachability tools only deprioritize security issues and then stop. This isn’t a viable approach over time:
- Tickets still pile up
- Scanners show warnings
- Vulnerable code still exists in your repository
- Your security ↔ engineering sync meeting still eats up time
When the next big vulnerability is found in something you’ve deferred, you still need to figure out how to update, but now you’re scrambling.
Use Reachability To Do Work
EdgeBit uses reachability to improve your apps: to continually find, fix and merge dependency updates.
- Fix security issues and SCA findings
- Identify impact to your app
- Merge updates with no impact
- Highlight changes an engineer needs to review
For too long, the security industry has focused solely on identifying vulnerabilities rather than fixing them. EdgeBit turns dependency management on its head with automation and cutting-edge code analysis, empowering organizations to streamline workflows, reduce grunt work, and tackle vulnerabilities effectively.
Learn more about EdgeBit’s approach using semantic diffs to speed up code review.
Automation and Static Analysis
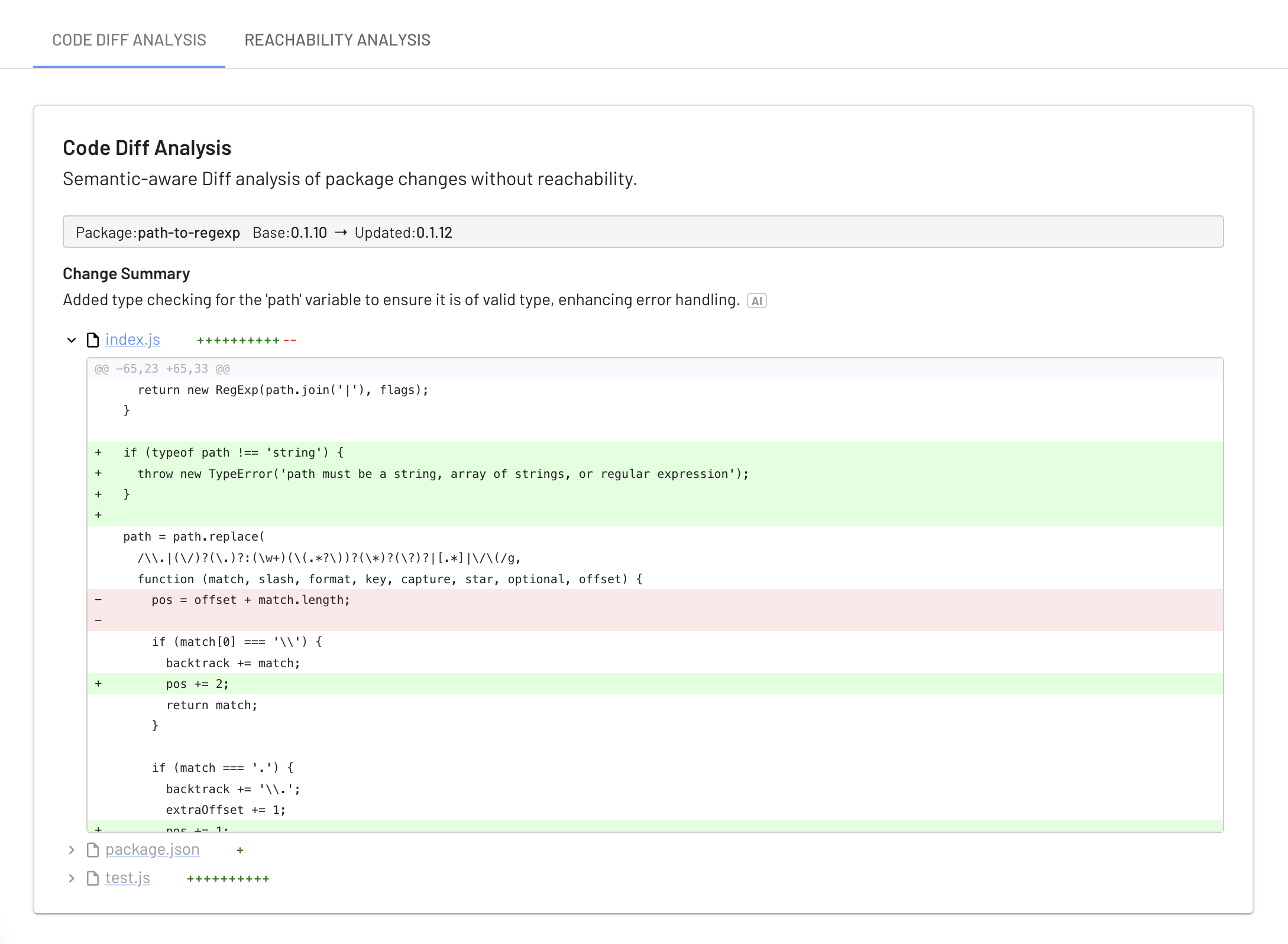
Automation is the cornerstone of modern security workflows. By integrating static analysis, EdgeBit helps teams identify where module updates intersect with application code, pinpointing critical changes with laser focus. This clarity transforms sprawling updates into manageable tasks, enabling engineers to merge updates confidently and efficiently.
Here’s how EdgeBit is reshaping vulnerability management:
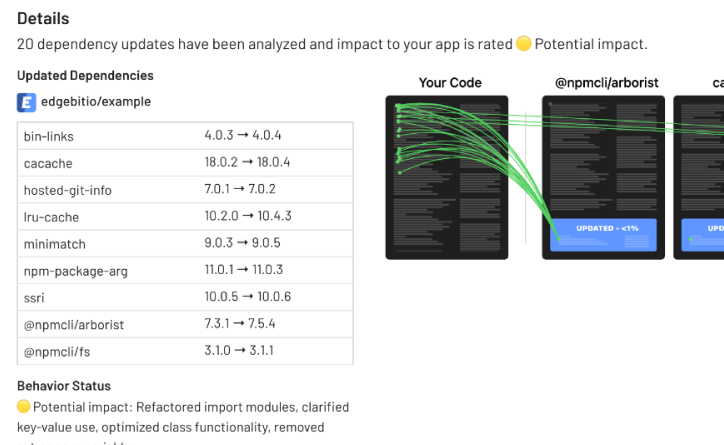
The Business Impact: Time Saved, Risks Reduced
Automation doesn’t just streamline workflows—it’s a game-changer for business outcomes. For a 15-person engineering team, eliminating security grunt work can save the equivalent of one full-time employee’s productivity annually. These time savings free engineers to focus on innovation, enhancing the overall security posture while accelerating project timelines.
Insider Insight: Why Static Analysis Matters
Static analysis dives deeper than surface-level scanning, revealing the true impact of dependency changes. Unlike semantic versioning, which often fails due to inconsistent practices, static analysis focuses on how updates interact with your codebase. This approach ensures that even major version changes are handled seamlessly, minimizing risk while maximizing efficiency.
What’s Next? Automate Your Security Workflow
The future of vulnerability management lies in automation. By addressing both technical and cultural barriers, EdgeBit enables organizations to:
- Burn down backlogs without adding to the workload.
- Reduce the 20% “security tax” on engineering teams.
- Foster a culture of collaboration between security and engineering.
Ready to transform your security workflows? EdgeBit’s GitHub app offers a free tier to get you started. Together, we can eliminate security grunt work and build a future of efficient, secure development.