I am excited to share some exciting news that EdgeBit has raised $3.1M in seed funding, led by Haystack, with participation from Y Combinator, Box Group, and Liquid2, as well as an incredible set of angels: co-founders of CoreOS, co-founders of ScaleFT, Okta executive leadership and other security leaders.
Over the past year we’ve worked with an amazing group of customers to secure their supply chains through vulnerability tracking, SBOM generation and proactive protection before code merges. It’s clear from these efforts and discussions with many security leaders that our industry needs more focus on fixing vulnerabilities rather than just detecting them. EdgeBit is leaning hard into “find, fix and merge” by introducing Dependency Autofix to our security platform.

Introducing Dependency Autofix
Let’s face it: dependency management is a chore. There are a million excuses to put it on the backburner – the top excuse is typically that it’s never clear how safe an upgrade is, even if you have a Pull Request ready to merge. You may doubt your tests, or not want to be the one to “touch it last”, or be required to shepherd the change through to production. Now you’ve got a pile of “security debt” accruing quickly.
The solution is to upgrade and deploy often. Dependency Autofix does the hard work to make your code branches have the latest and safest set of dependencies, using AI and static analysis under the hood.
We’re focusing on the Javascript/Typescript ecosystem first due to its complexity, attack surface and the pain that teams feel when managing their NodeJS dependencies.
Our frontend JS projects are lacking in enough unit, integration, and e2e that most of those devs are scared to touch any dependencies.
jml78 on Hacker News
By understanding what is extremely safe, EdgeBit can change developer behaviors.
Determining Safety with Call Site and Reachability Analysis
EdgeBit uses static analysis and call graph processing to understand exactly how your code calls into your dependencies. When dependencies are updated, charting a path through what changed and if/how your app interacts with those changes provides a clear signal of risk.
Once call sites have been identified, more investigation is done by EdgeBit’s AI to understand the changes in the library, how that specific function was changed and what that means for your app code. It’s important to note that the use of AI is complementary to our usage of static analysis & dependency graph knowledge. In all use-cases, the security and upgrade decisions are based on hard facts and AI augments that knowledge.
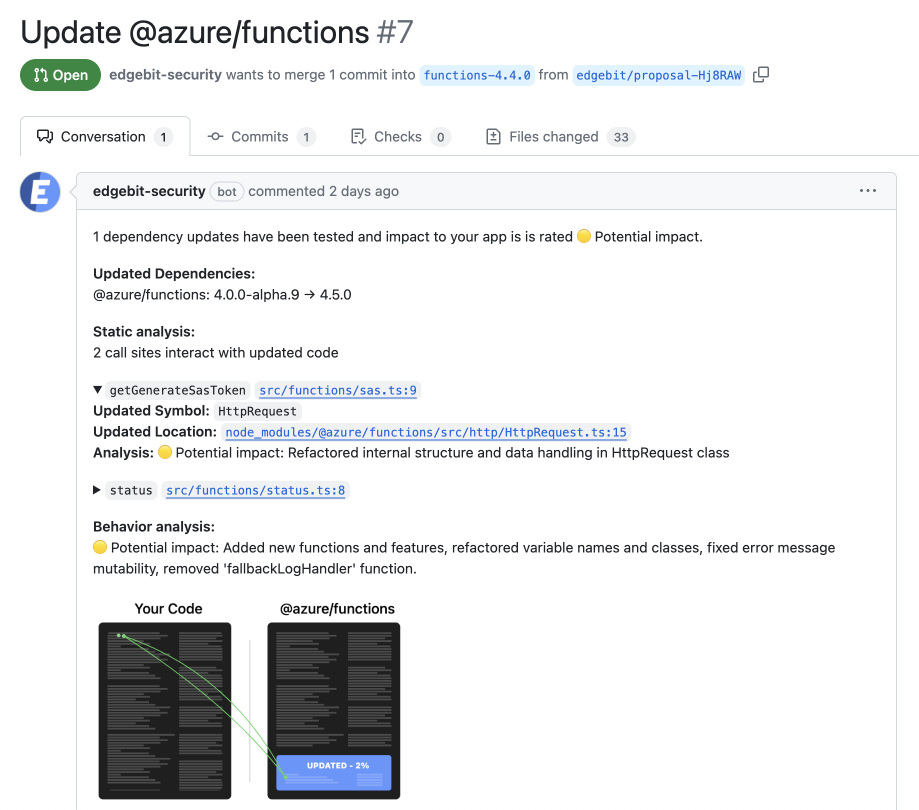
In many cases, a dependency update is a “no-op” in terms of impact to your app. However, risk only goes down once you can determine that with certainty.
“Dependency Autofix quickly led me to the revelation that almost no engineering teams have the context to properly understand dependency update risk. Teams put blind faith in semantic versioning and an aspirational goal across the industry to prevent breaking changes.”
Noah Stanford, CEO of 0pass
As Noah alludes, breaking changes and incorrect versioning do happen, but they can be detected with code analysis.
Why Is This Groundbreaking?
Static analysis is hard, especially in a language as dynamic as JavaScript. Unlike languages like Go or C#, where the analysis can be performed by just parsing the source files, JavaScript libraries will often dynamically build up their public APIs when they’re first loaded.
To properly analyze their call graphs, requires a purpose built engine capable of simulating their execution flow. EdgeBit is proud to have developed such a revolutionary technology to drive unparalleled accuracy in reachability and impact analysis.
Solving the “Lack of Tests” Problem
A universal concern we hear from customers is that they lack tests in certain areas or have no tests that exercise dependencies enough to give them confidence that a passed CI run is a useful signal.
EdgeBit’s code analysis can make a similar determination about breaking changes that a test suite would but without the effort required to implement or maintain it.
The result is your engineers gaining insight into the exact area where they should focus their code review and EdgeBit augments the lack of tests with code analysis and risk scoring.
Updating Groups of Dependencies
Dependency Autofix upgrades groups of dependencies together, both to streamline the amount of review required and because your transitive dependency graph typically requires that multiple packages are updated at the same time.
EdgeBit continually generates a set of change proposals for your active repos and their branches, and then based on how your app is impacted, may:
- open a PR with no impact, ready to merge
- open a PR and assign a reviewer (based on Git history) if a proposal needs review
- send a chat to your org’s expert in using a library to review a proposal

Proposed changes aren’t just reactive to security findings. Our goal is to keep all of your dependencies up to date so you can realize the benefits of bug fixes and not be far behind when a security issue is only available for the newest releases of a dependency.
Working within your Developer Culture and SDLC
Dependency Autofix works with all Git-based workflows and has tight integration with GitHub. All levels of engineers will feel ease and confidence using EdgeBit to understand how specific apps use each dependency.
Code review, branch/forking rules and merge policies frequently differ between repositories. Dependency Autofix can adapt to any workflow from heavy review all the way to auto-merge.
While EdgeBit can augment gaps in your tests, at every step of the way your existing test suites can run as they normally do to add confidence to the safety of proposed code changes.
Distributing Work Across Your Teams
Spreading around the chore of updating dependencies is an energizing cultural shift for your engineering organization. No longer will dependency updates fall on just your Principal Engineers or the one team member who’s an “expert” in a specific tool or language.
Burn Down your Security Backlog Without the Productivity Tax
Code reachability immediately focuses your engineers on the handful of call sites that might impact your app functionality. EdgeBit’s understanding of how your code uses its dependencies eliminates the toil of compatibility research.
Identifying “no-op” upgrades is an instant 10x improvement in time-to-merge, giving your team back about 1.1x headcount in extra sprint capacity for a team of 15.
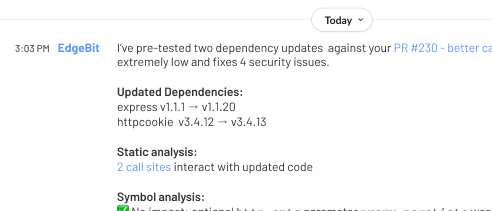
EdgeBit is proactive with new Pull Requests or chat requests when it makes sense to engage your engineers when it makes sense for each situation.
Excited to Execute on our Roadmap
Our team is excited about the roadmap for the upcoming year. We believe there is an immense amount of opportunity to ease the pain of updates, automate away toil and bring positive change to our customer’s engineering culture.
Below is a brief list of topics we’re excited about:
- expanding to additional language ecosystems
- upgrading through minor versions and if needed, mutating the call sites in your code
- syncing up code proposals across repos, eg. “upgrade my Go version everywhere at once”
- more ways to make security workload more equitable between teams and individuals
Want to learn more or share your ideas? Reach out to the team, we’d love to chat.
Try out Dependency Autofix
Trying out Dependency Autofix is extremely easy — just connect EdgeBit to your GitHub account to start your free trial today.
Dependency update proposals will be continuously generated for your repositories and on day 1 you’ll be on your way to changing behaviors around dependency upgrades.
