Generative AI and more traditional machine learning unlock huge potential but also bring sprawling ecosystems of dependencies with them.
Many of these projects are extremely fast moving, and with layers of transitive dependencies, it’s hard to keep up.
ChatGPT application
I recently loaded up a sample OpenAI application from reflex.dev into EdgeBit. The app embeds a simple ChatGPT interface using the reflex tool. Reflex is a toolkit for making full-stack web apps in Python; frontend included.
Breaking Down the SBOM
The SBOM visualized by EdgeBit is pretty large, but this is representative of the dependency needs of modern AI and standardized container base images — remember, this one is just a sample app!
Since, the chat app repo didn’t have a Dockerfile, I created one from python:3.11-bookworm which is the source of the Debian packages. Don’t let these counts reflect poorly on the Reflex team.
| Type | Count |
|---|---|
| NodeJS | 270 packages |
| Debian | 431 packages |
| Python | 77 packages |
| Binary | 3 binaries |
As you can see, we’re finding the NodeJS packages used behind the scenes in reflex in addition to the expected Python packages.
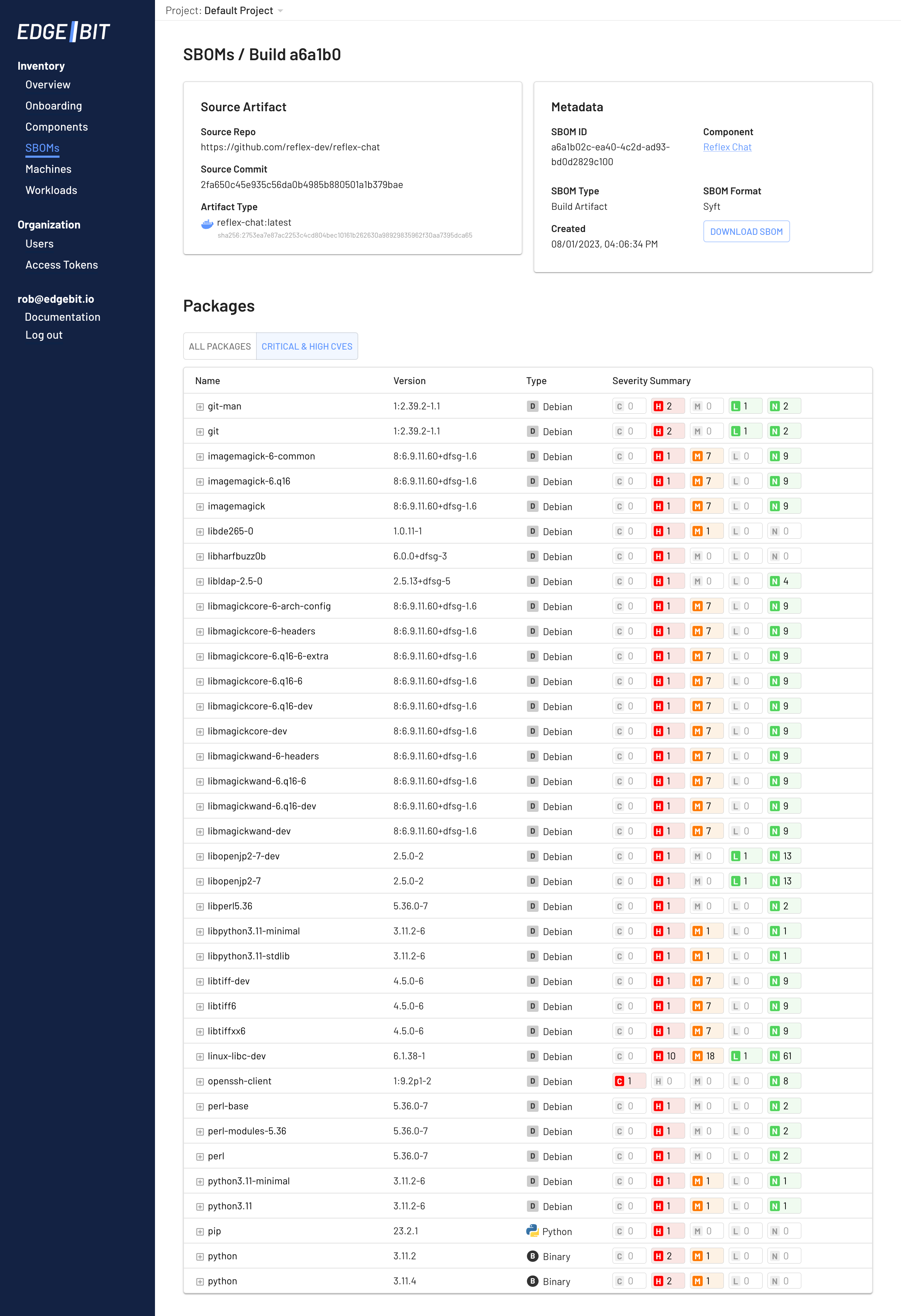
Filtering to just High and Critical, we see the dreaded sources of noise like ImageMagick and Perl. These are unlikely to be used but are pulled in as transitive dependencies. Using risk-based prioritization, we’ll find out if EdgeBit deprioritizes them below.
Risk-based Prioritization
EdgeBit is modifying the risk score of 99% of the vulnerabilities found right off the bat. 514 were suppressed by the default policy of ignoring Negligible CVEs (lower than Low!) that are just noise. Commonly issues that a security researcher has submitted so they are tracked but are deemed not worthy of time.
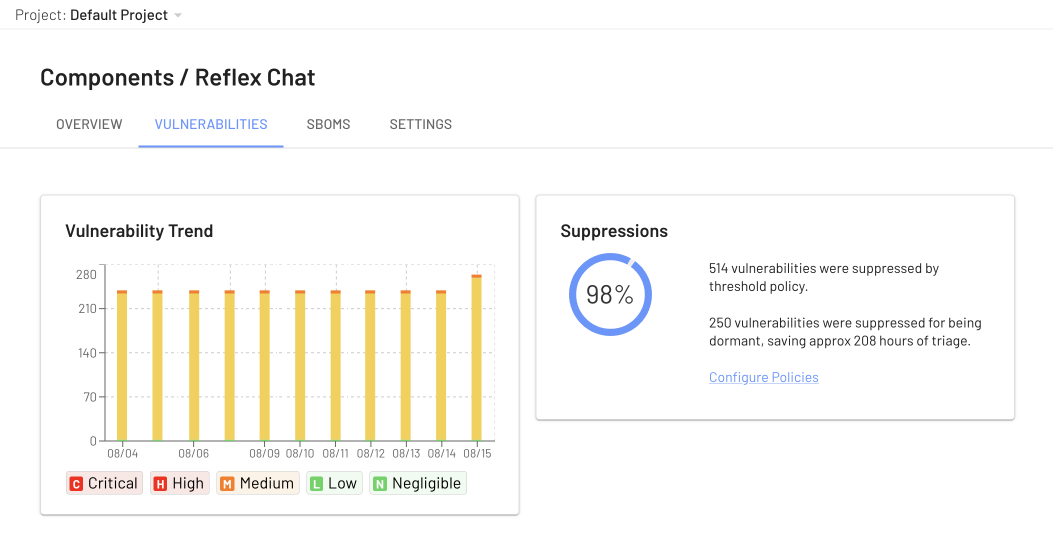
More impressive however, are the 250 vulnerabilities that were lowered in severity by policy because they aren’t detected or loaded in our app when it runs.
The default policy is to lower anything dormant to Medium, which you can see by the large amounts of them. Other options are to always drop by 1 or 2 levels, to drop to Low, or ignore them altogether.
Ignoring them is useful if you use an “inbox zero” style workflow, where you’re constantly fixing issues that bubble to the top. EdgeBit reacts in real-time to any change in your applications so this list is kept up to date with accurate prioritization.
OS Packages Bring Vulnerability Noise
On day one, we saw a large amount of noise from the Debian packages that EdgeBit cut through for us.
Since our sample app pulls the latest version of most AI dependencies, it looks great on day one, but starts to accumulate issues as things are discovered and reported. This is realistic of any app - development and dependencies start fresh but don’t remain that way forever. In fact, you can see things ticking upwards on the last bar in the history graph.
Maintaining Upstream Compatibility for Enterprises
Enterprise engineering teams both write software and operate open source components. Modification of the open source components from their upstream makes it much harder to consume newer versions over time. Many projects and products use the most minimal base image they can, but it’s impossible to pair down the transitive dependencies even if they aren’t used.
EdgeBit solves this problem for engineers by filtering out vulnerability noise generated by either OS packages or code dependencies.
